what the administrator is doing?
After installing a new Linux system the administrator runs a command that records the size,
permissions, and MD5 sum of all the files on the system. Which of the following describes what
the administrator is doing?
Which of the following procedures should the administrator perform FIRST on the system?
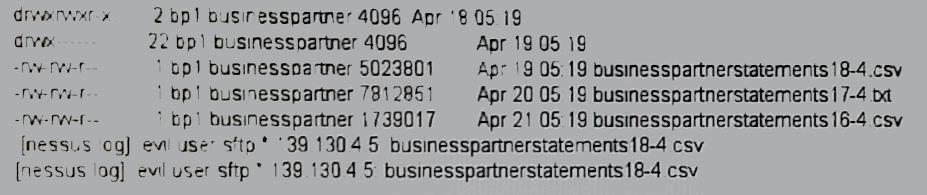
An intrusion has occurred in an internet facing system. The security administrator would like to
gather forensic evidence while the system is still in operation. Which of the following procedures
should the administrator perform FIRST on the system?
Which of the following wireless standards is backwards compatible with 802.11g?
Which of the following wireless standards is backwards compatible with 802.11g?
Which of the following ports will be used for logging into secure websites?
Which of the following ports will be used for logging into secure websites?
which of the following?
The below report indicates that the system is MOST likely infected by which of the following?
Protocol LOCAL IP FOREIGN IP STATE
TCP 0.0.0:445 0.0.0.0:0 Listening
TCP 0.0.0.0:3390 0.0.0.0:0 Listening
Which of the following types of risk mitigation strategies is being followed?
A security administrator is required to submit a detailed implementation plan and back out plan to
get approval prior to updating the firewall and other security devices. Which of the following types
of risk mitigation strategies is being followed?
Which of the following authentication services uses a default TCP of 389?
Which of the following authentication services uses a default TCP of 389?
TO meet confidentiality the tapes should be:
A software company sends their offsite backup tapes to a third party storage facility. TO meet
confidentiality the tapes should be:
Which of the following should Ann enable to support both encryption and proxy services?
Ann, a technician, wants to implement a single protocol on a remote server which will enable her
to encrypt and proxy all of her traffic though the remote server via SOCKS5. Which of the following
should Ann enable to support both encryption and proxy services?