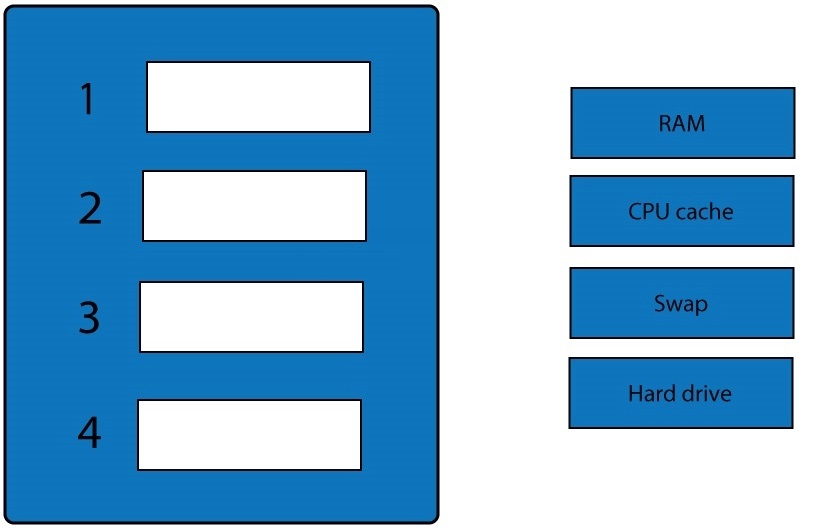
Which of the following does this represent?
A security architect has developed a framework in which several authentication servers work
together to increase processing power for an application. Which of the following does this
represent?
Which of the following can be implemented to increase security and prevent this from happening?
An administrator notices that former temporary employees’ accounts are still active on a domain.
Which of the following can be implemented to increase security and prevent this from happening?
The administrator should be looking for the presence of a/an:
A trojan was recently discovered on a server. There are now concerns that there has been a
security breach that allows unauthorized people to access data. The administrator should be
looking for the presence of a/an:
Which of the following concepts does this illustrate?
A technician has implemented a system in which all workstations on the network will receive
security updates on the same schedule. Which of the following concepts does this illustrate?
Which of the following protocols uses TCP instead of UDP and is incompatible with all previous versions?
Which of the following protocols uses TCP instead of UDP and is incompatible with all previous
versions?
Which of the following offers the LEAST amount of protection against data theft by USB drives?
Which of the following offers the LEAST amount of protection against data theft by USB drives?
Which of the following symmetric key algorithms are examples of block ciphers?
Which of the following symmetric key algorithms are examples of block ciphers? (Select THREE).
Which of the following should be done NEXT?
A security analyst has been informed that the development team has plans to develop an
application which does not meet the company’s password policy. Which of the following should be
done NEXT?