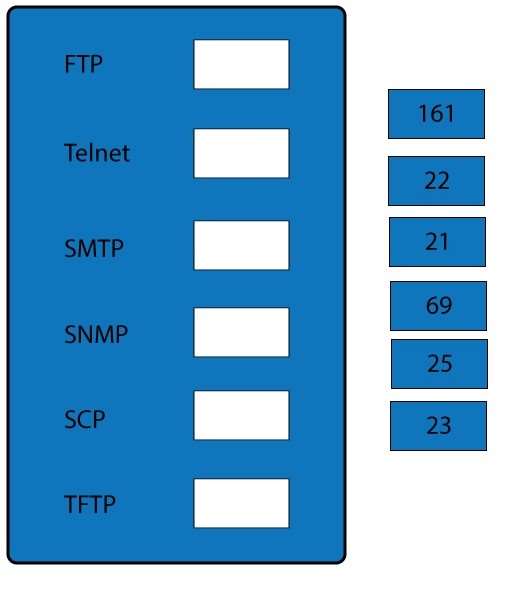
Drag and drop the correct protocol to its default port.
Which of the following authentication services should b…
An information bank has been established to store contacts, phone numbers and other records. A UNIXapplication needs to connect to the index server using port 389. Which of the following authentication services
should be used on this port by default?
Which of the following protocols would have been affect…
A malicious program modified entries in the LMHOSTS file of an infected system. Which of the following
protocols would have been affected by this?
Which of the following was the colleague performing?
A security analyst noticed a colleague typing the following command:
`Telnet some-host 443’
Which of the following was the colleague performing?
Which of the following, by default, would be the BEST c…
A network consists of various remote sites that connect back to two main locations. Pete, the security
administrator, needs to block TELNET access into the network. Which of the following, by default, would be the
BEST choice to accomplish this goal?
Which of the following is the default port for TFTP?
Which of the following is the default port for TFTP?
Which of the following is a difference between TFTP and FTP?
Which of the following is a difference between TFTP and FTP?
Which of the following protocols is the BEST choice to use?
A network administrator is asked to send a large file containing PII to a business associate.
Which of the following protocols is the BEST choice to use?
Which of the following ports and protocol types must be…
Which of the following ports and protocol types must be opened on a host with a host-based firewall to allow
incoming SFTP connections?
Which of the following protocols must he allow through …
Pete, a network administrator, is implementing IPv6 in the DMZ. Which of the following protocols must he allow
through the firewall to ensure the web servers can be reached via IPv6 from an IPv6 enabled Internet host?