Which of the following MUST be prevented in order for t…
Datacenter access is controlled with proximity badges that record all entries and exits from the datacenter. The
access records are used to identify which staff members accessed the data center in the event of equipment
theft. Which of the following MUST be prevented in order for this policy to be effective?
Which of the following controls will allow the organiza…
A datacenter requires that staff be able to identify whether or not items have been removed from the facility.
Which of the following controls will allow the organization to provide automated notification of item removal?
Which of the following security measures can be put in …
Key cards at a bank are not tied to individuals, but rather to organizational roles. After a break in, it becomes
apparent that extra efforts must be taken to successfully pinpoint who exactly enters secure areas. Which of
the following security measures can be put in place to mitigate the issue until a new key card system can be
installed?
Which of the following does this describe?
A company is installing a new security measure that would allow one person at a time to be authenticated to an
area without human interaction. Which of the following does this describe?
Which of the following is being described?
Visitors entering a building are required to close the back door before the front door of the same entry room is
open. Which of the following is being described?
Which of the following mitigation methods would provide…
Pete, an IT Administrator, needs to secure his server room. Which of the following mitigation methods would
provide the MOST physical protection?
Which of the following BEST meets their goal?
A company is trying to implement physical deterrent controls to improve the overall security posture of their data
center. Which of the following BEST meets their goal?
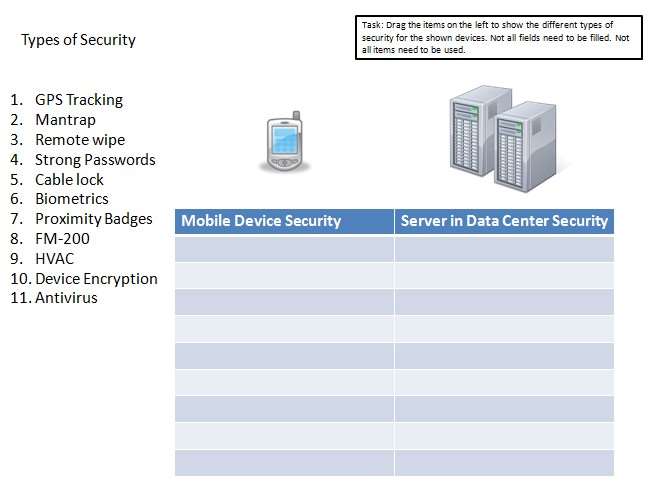
Drag the items on the left to show the different types of security…
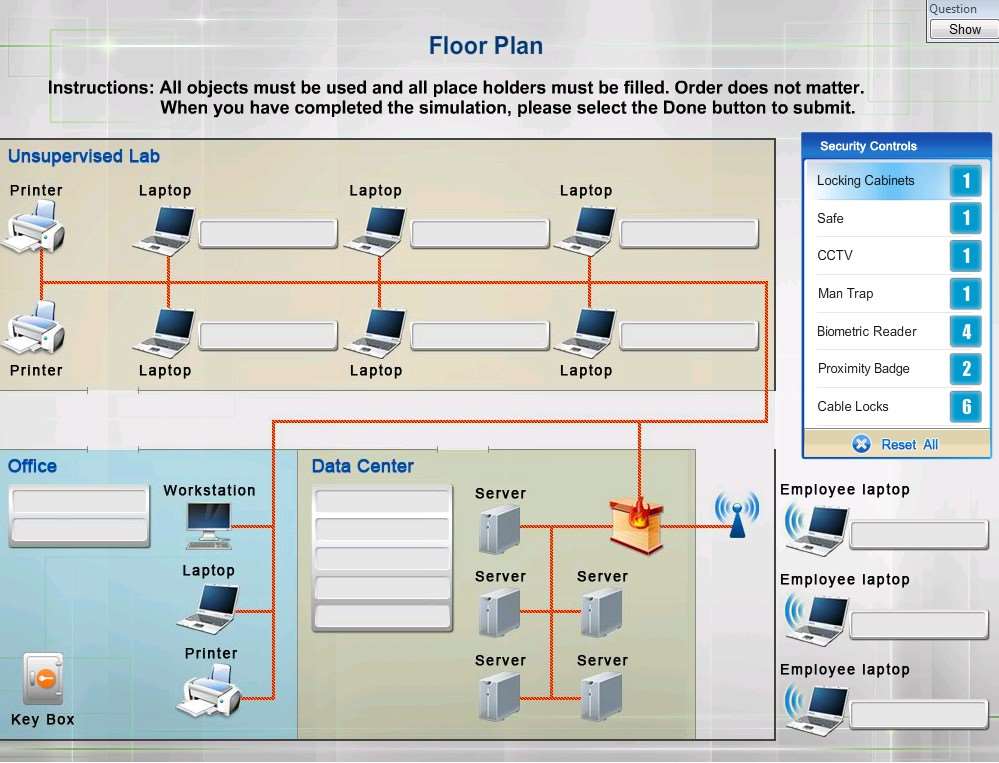
Drag and drop the appropriate security controls on the floor…
DRAG DROP
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security
controls on the floor plan-Instructions: All objects must be used and all place holders must be filled. Order does
not matter. When you have completed the simulation, please select the Done button to submit.
Select and Place:
This caused the electronic locks on the datacenter door…
A malicious person gained access to a datacenter by ripping the proximity badge reader off the wall near the
datacenter entrance. This caused the electronic locks on the datacenter door to release because the: