Which of the following wireless security measures can a…
Which of the following wireless security measures can an attacker defeat by spoofing certain properties of their
network interface card?
Which of the following will help prevent smurf attacks?
Which of the following will help prevent smurf attacks?
Which of the following BEST describes the type of attac…
which of the following types of attacks?
Timestamps and sequence numbers act as countermeasures against which of the following types of attacks?
Session tokens were deployed to mitigate this issue and…
A network analyst received a number of reports that impersonation was taking place on the network.
Session tokens were deployed to mitigate this issue and defend against the following attacks:
Which of the following attacks could be used to initiat…
Which of the following attacks could be used to initiate a subsequent man-in-the-middle attack?
Which of the following is the MOST likely cause?
An administrator is assigned to monitor servers in a data center. A web server connected to the Internet
suddenly experiences a large spike in CPU activity. Which of the following is the MOST likely cause?
Which of the following will BEST mitigate the risk if i…
A security technician at a small business is worried about the Layer 2 switches in the network suffering from a
DoS style attack caused by staff incorrectly cabling network connections between switches.
Which of the following will BEST mitigate the risk if implemented on the switches?
The administrator suspects that:
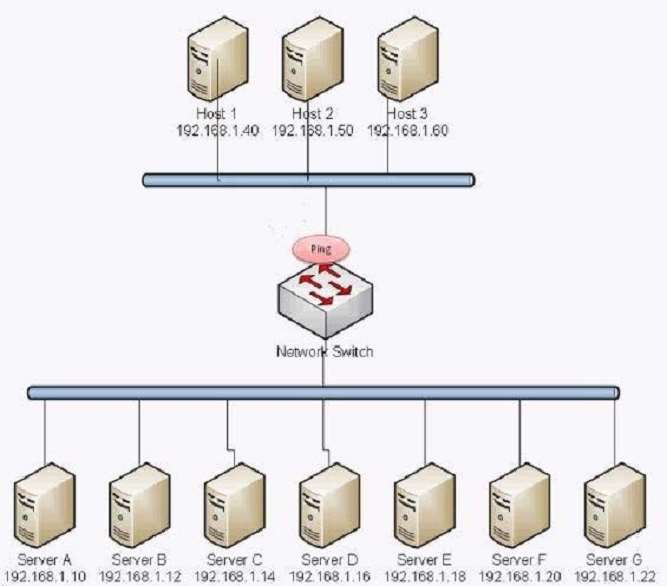
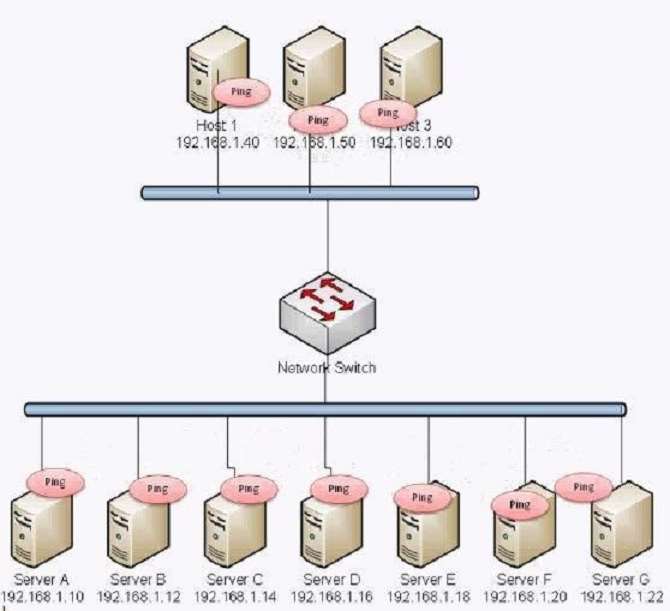
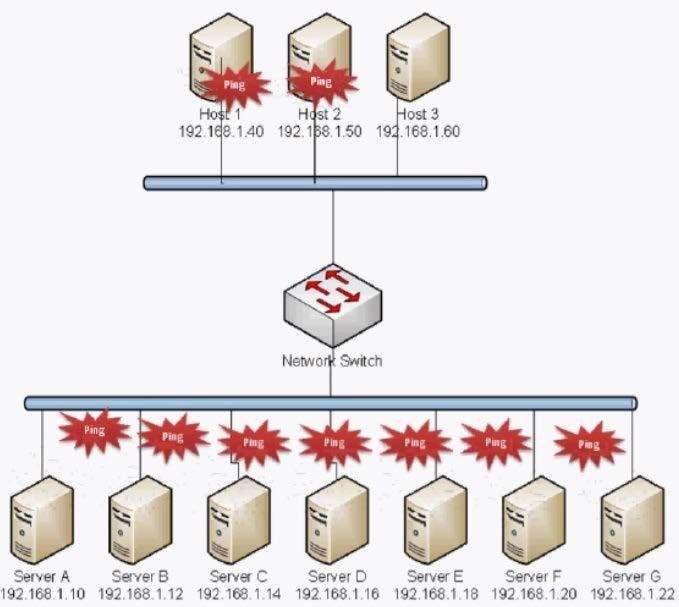
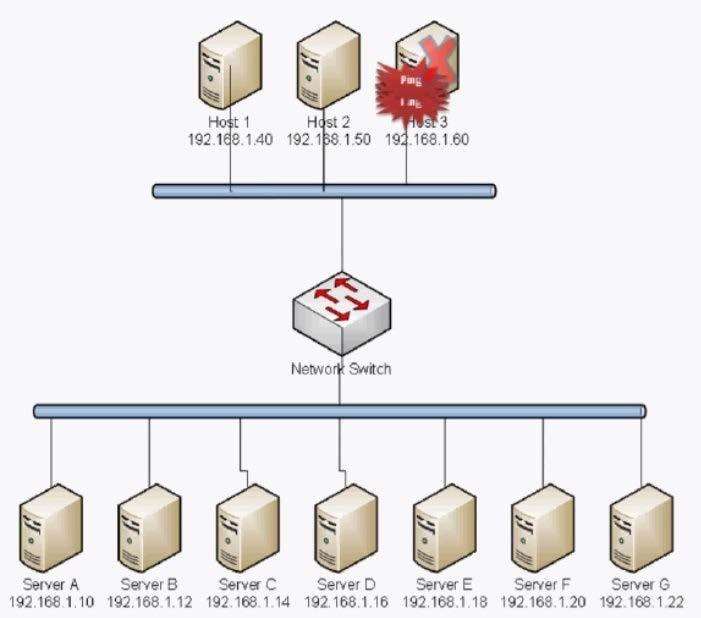
An administrator notices an unusual spike in network traffic from many sources. The administrator suspects
that:
A distributed denial of service attack can BEST be desc…
A distributed denial of service attack can BEST be described as: