Which of the following is MOST likely blocking Pete’s access to this site?
Pete, an employee, attempts to visit a popular social networking site but is blocked. Instead, a page is
displayed notifying him that this site cannot be visited. Which of the following is MOST likely blocking
Pete’s access to this site?
Which of the following is suited for this purpose?
A review of the company’s network traffic shows that most of the malware infections are caused by users
visiting gambling and gaming websites. The security manager wants to implement a solution that will
block these websites, scan all web traffic for signs of malware, and block the malware before it enters the
company network. Which of the following is suited for this purpose?
Which of the following is BEST at blocking attacks and providing security at layer 7 of the OSI model?
Which of the following is BEST at blocking attacks and providing security at layer 7 of the OSI model?
Which of the following should the security administrator implement to limit web traffic based on country of or
Which of the following should the security administrator implement to limit web traffic based on country
of origin? (Select THREE).
Which of the following technologies was MOST likely being used to generate this log?
A security engineer is reviewing log data and sees the output below:
POST: /payload.php HTTP/1.1
HOST: localhost
Accept: */*
Referrer: http://localhost/
*******
HTTP/1.1 403 Forbidden
Connection: close
Log: Access denied with 403. Pattern matches form bypass Which of the following technologies was
MOST likely being used to generate this log?
Which of the following would be the BEST place to start?
An administrator would like to review the effectiveness of existing security in the enterprise. Which of the
following would be the BEST place to start?
Which of the following should be implemented to secure the devices without risking availability?
A company has proprietary mission critical devices connected to their network which are configured
remotely by both employees and approved customers. The administrator wants to monitor device
security without changing their baseline configuration. Which of the following should be implemented to
secure the devices without risking availability?
Which of the following firewall rules only denies DNS zone transfers?
Which of the following firewall rules only denies DNS zone transfers?
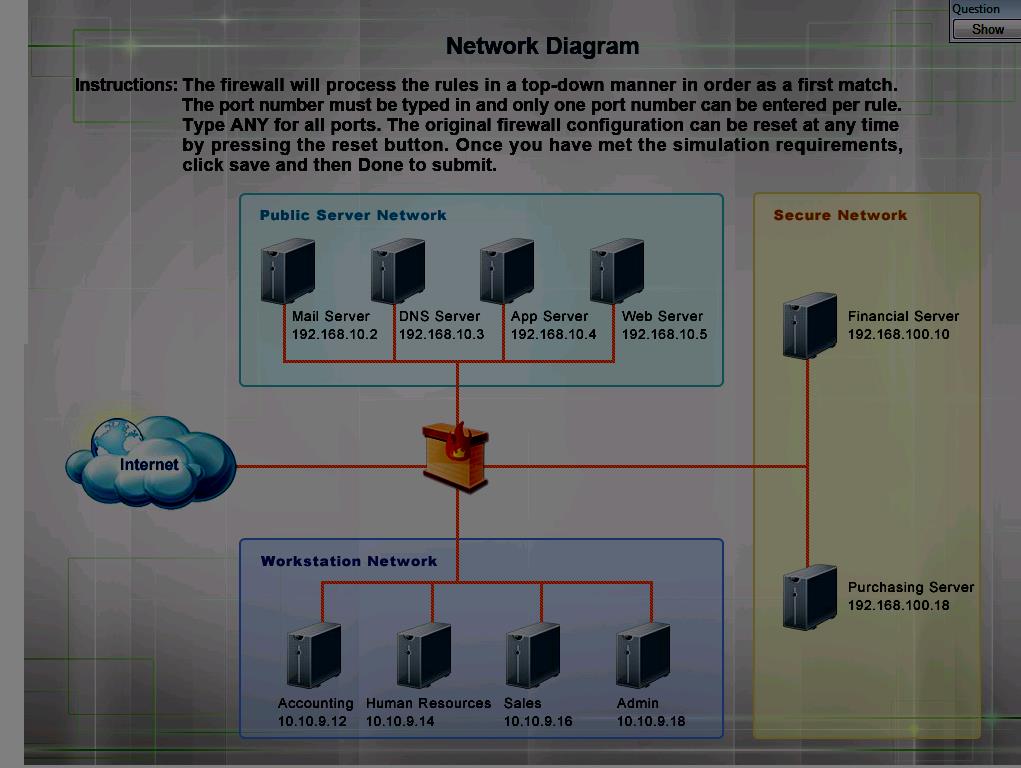
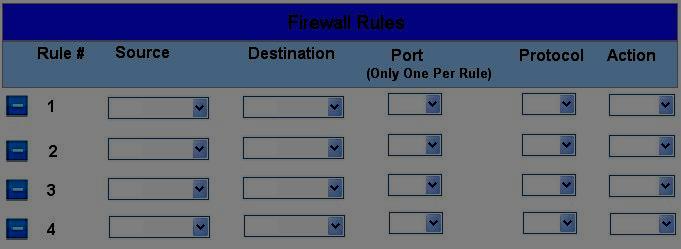
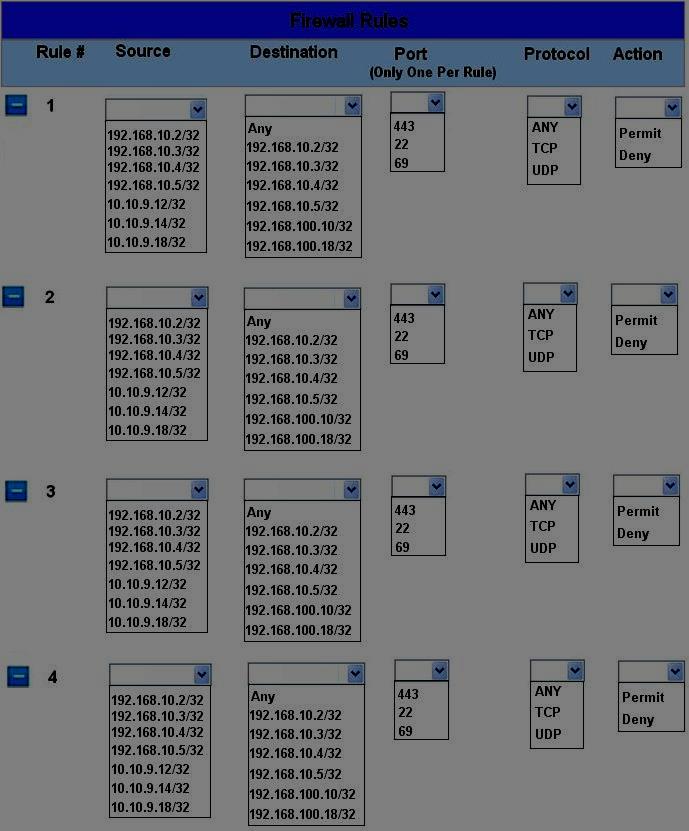
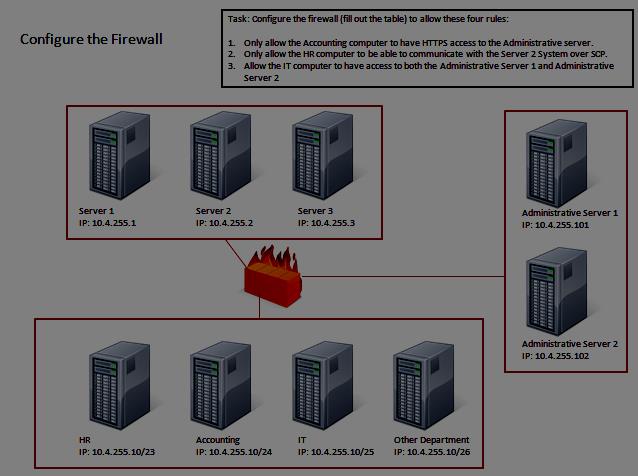
Click on the firewall and configure it to allow ONLY the following communication.
HOTSPOT
The security administrator has installed a new firewall which implements an implicit DENY policy by
default. Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default
HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the
default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the
default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port
number must be typed in and only one port number can be entered per rule Type ANY for all ports. The
original firewall configuration can be reset at any time by pressing the reset button. Once you have met
the simulation requirements, click save and then Done to submit.