Which of the following will allow the company to contin…
A company wants to create highly available datacenters. Which of the following will allow the company to continue to maintain an Internet presence at all sites in the
event that a WAN circuit at one site goes down?
which of the following?
Allowing unauthorized removable devices to connect to computers increases the risk of which of the following?
which of the following address types?
A host has been assigned the address 169.254.0.1. This is an example of which of the following address types?
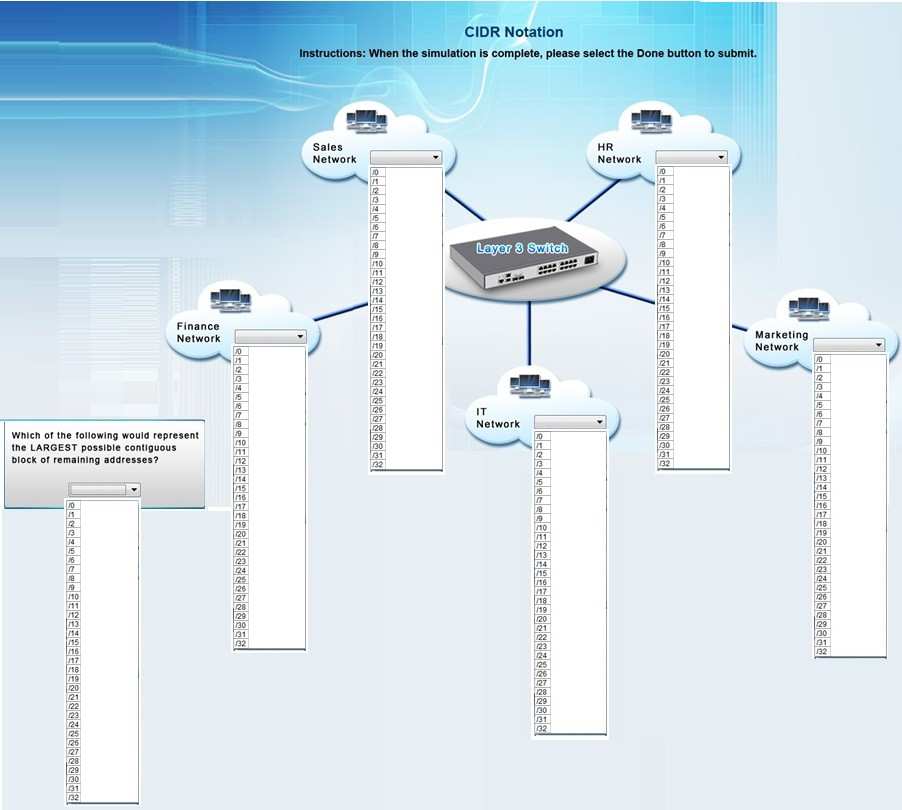
identify the unused portion of the subnet by responding to the question on the graphic.
HOTSPOT
Corporate headquarters provided your office a portion of their class B subnet to use at a new office location. Allocate the minimum number of addresses (using
CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic. All drop downs must be filled.
Instructions: When the simulation is complete, please select the Done button to submit.
All Networks have the range from /0 to/32
Hot Area:
Which of the following BEST meets this need?
Jane, an IT security technician, needs to create a way to secure company mobile devices. Which of the following BEST meets this need?
which of the following subnet masks should Joe use for …
A technician, Joe, has been tasked with assigning two IP addresses to WAN interfaces on connected routers. In order to conserve address space, which of the
following subnet masks should Joe use for this subnet?
Which of the following technical controls helps to prev…
Which of the following technical controls helps to prevent Smartphones from connecting to a corporate network?
Which of the following is a valid IPv4 loopback address?
A technician, Joe, needs to troubleshoot a recently installed NIC. He decides to ping the local loopback address. Which of the following is a valid IPv4 loopback
address?
Which of the following BEST meets the requirements?
The chief Risk officer is concerned about the new employee BYOD device policy and has requested the security department implement mobile security controls to
protect corporate data in the event that a device is lost or stolen. The level of protection must not be compromised even if the communication SIM is removed from
the device. Which of the following BEST meets the requirements? (Select TWO)
Which of the following is an example of an IPv4 address?
Which of the following is an example of an IPv4 address?