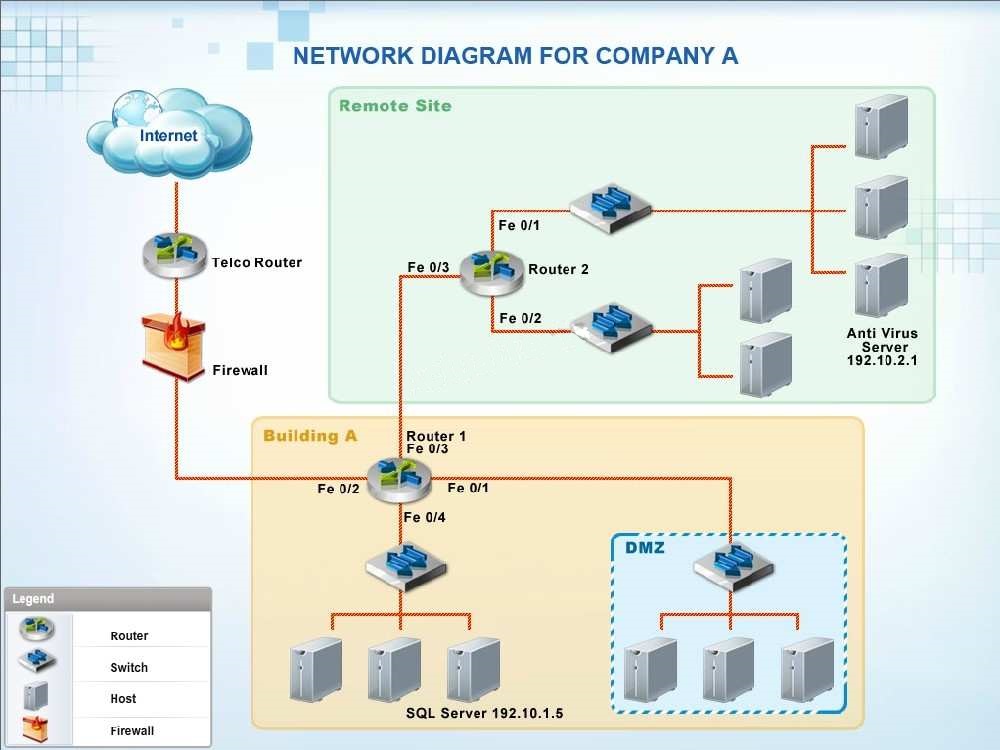
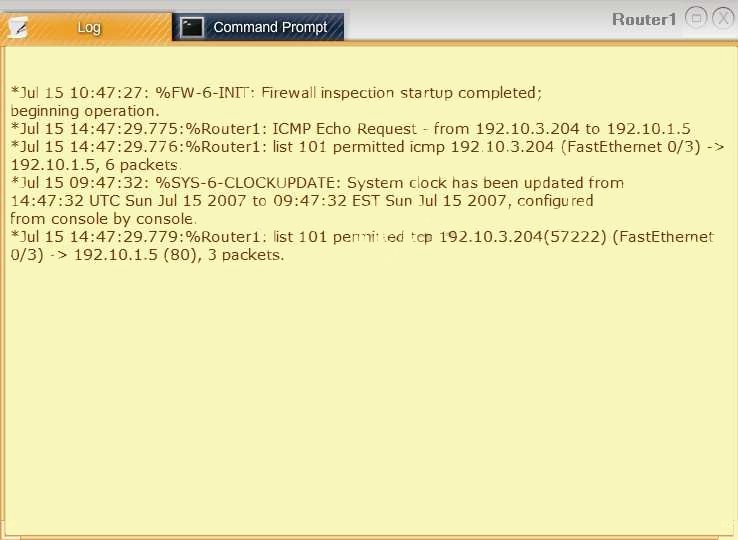
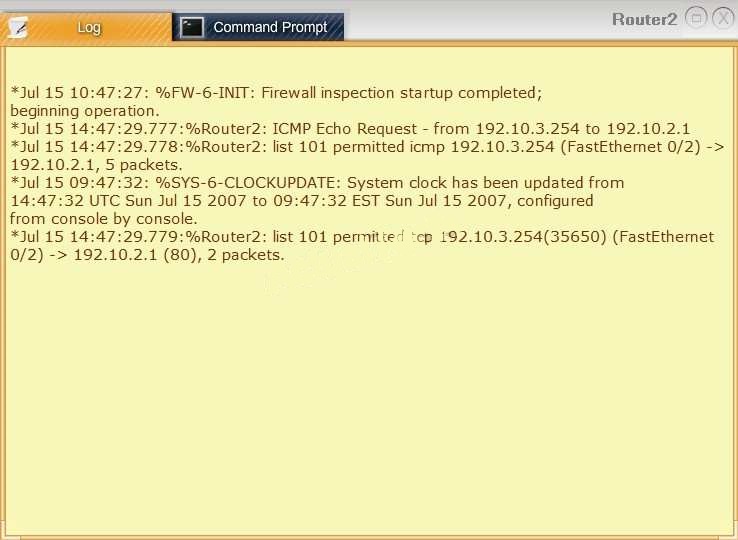
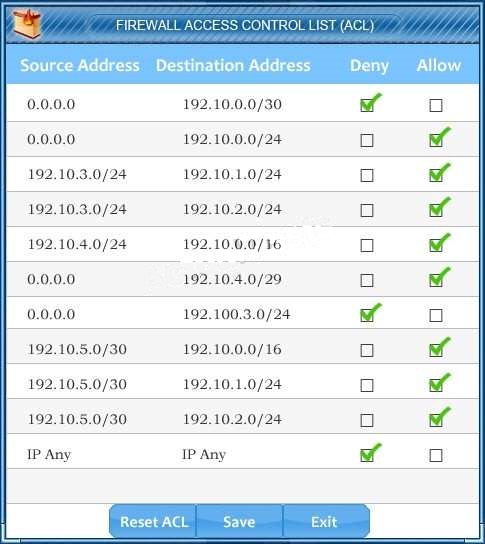
Company A has noticed abnormal behavior targeting their SQL server on the network…
CORRECT TEXT
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address
ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
which of the following type of calculations is needed?
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on
their network. Vendors were authenticating directly to the retailer’s AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where
credit card servers were kept. The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that
because the vendors were required to have site to site VPN’s no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
Which of the following is the BEST time to make them ad…
A security administrator was recently hired in a start-up company to represent the interest of security and to assist the network team in improving security in the
company. The programmers are not on good terms with the security team and do not want to be distracted with security issues while they are working on a major
project. Which of the following is the BEST time to make them address security issues in the project?
Which of the following selections represent the BEST op…
A company Chief Information Officer (CIO) is unsure which set of standards should govern the company’s IT policy. The CIO has hired consultants to develop use
cases to test against various government and industry security standards. The CIO is convinced that there is large overlap between the configuration checks and
security controls governing each set of standards. Which of the following selections represent the BEST option for the CIO?
Which of the following are needed to implement these re…
A network engineer wants to deploy user-based authentication across the company’s wired and wireless infrastructure at layer 2 of the OSI model. Company
policies require that users be centrally managed and authenticated and that each user’s network access be controlled based on the user’s role within the company.
Additionally, the central authentication system must support hierarchical trust and the ability to natively authenticate mobile devices and workstations. Which of the
following are needed to implement these requirements? (Select TWO).
Which of the following implementations addresses the …
Company XYZ finds itself using more cloud-based business tools, and password management is becoming onerous. Security is important to the company; as a
result, password replication and shared accounts are not acceptable. Which of the following implementations addresses the
distributed login with centralized authentication and has wide compatibility among SaaS vendors?
Which of the following preventative controls would MOST…
The Chief Information Security Officer (CISO) at a large organization has been reviewing some security-related incidents at the organization and comparing them to
current industry trends. The desktop security engineer feels that the use of USB storage devices on office computers has contributed to the frequency of security
incidents. The CISO knows the acceptable use policy prohibits the use of USB storage devices. Every user receives a popup warning about this policy upon login.
The SIEM system produces a report of USB violations on a monthly basis; yet violations continue to occur. Which of the following preventative controls would
MOST effectively mitigate the logical risks associated with the use of USB storage devices?
Which of the following is the FIRST step the analyst sh…
The IT Security Analyst for a small organization is working on a customer’s system and identifies a possible intrusion in a database that contains PII. Since PII is
involved, the analyst wants to get the issue addressed as soon as possible. Which of the following is the FIRST step the analyst should take in mitigating the impact
of the potential intrusion?
Which of the following capabilities is MOST likely to c…
An IT manager is working with a project manager from another subsidiary of the same multinational organization. The project manager is responsible for a new
software development effort that is being outsourced overseas, while customer acceptance testing will be performed in house. Which of the following capabilities is
MOST likely to cause issues with network availability?
How would a security engineer BEST interpret the financ…
A finance manager says that the company needs to ensure that the new system can “replay” data, up to the minute, for every exchange being tracked by the
investment departments. The finance manager also states that the company’s transactions need to be tracked against this data for a period of five years for
compliance. How would a security engineer BEST interpret the finance manager’s needs?