Which of the following should the programmer use?
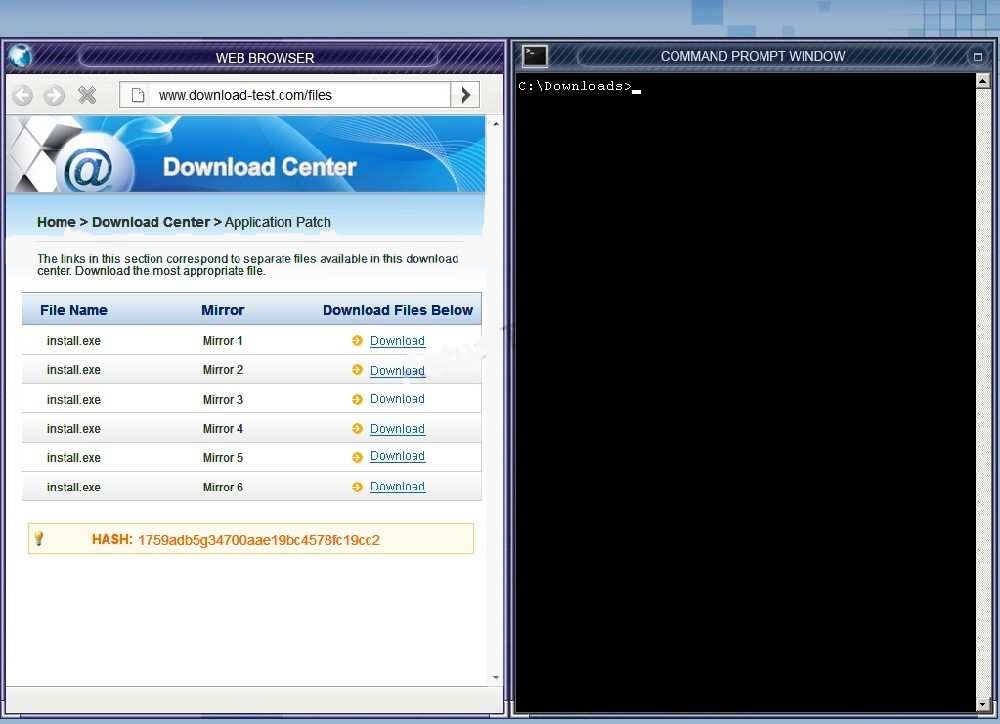
A Company transfers millions of files a day between their servers. A programmer for the company has created a program that indexes and verifies the integrity of
each file as it is replicated between servers. The programmer would like to use the fastest algorithm to ensure integrity. Which of the following should the
programmer use?
which multiple TCP flags are set to 1?
Which of the following attacks initiates a connection by sending specially crafted packets in which multiple TCP flags are set to 1?
Which of the following describes how the switch in the …
A classroom utilizes workstations running virtualization software for a maximum of one virtual machine per working station. The network settings on the virtual
machines are set to bridged. Which of the following describes how the switch in the classroom should be configured to allow for the virtual machines and host
workstation to connect to network resources?
Which of the following is Joe attempting to complete?
Joe, a security analyst, is attempting to determine if a new server meets the security requirements of his organization. As a step in this process, he attempts to
identify a lack of security controls and to identify common misconfigurations on the server. Which of the following is Joe attempting to complete?
To do this, the security analyst will perform a:
A company is rolling out a new e-commerce website. The security analyst wants to reduce the risk of the new website being comprised by confirming that system
patches are up to date, application hot fixes are current, and unneeded ports and services have been disabled. To do this, the security analyst will perform a:
Drag and drop the BEST security solution to meet the given requirements.
DRAG DROP
An organization is implementing a project to simplify the management of its firewall network flows and implement security controls. The following requirements
exist. Drag and drop the BEST security solution to meet the given requirements. Options may be used once or not at all. All placeholders must be filled.
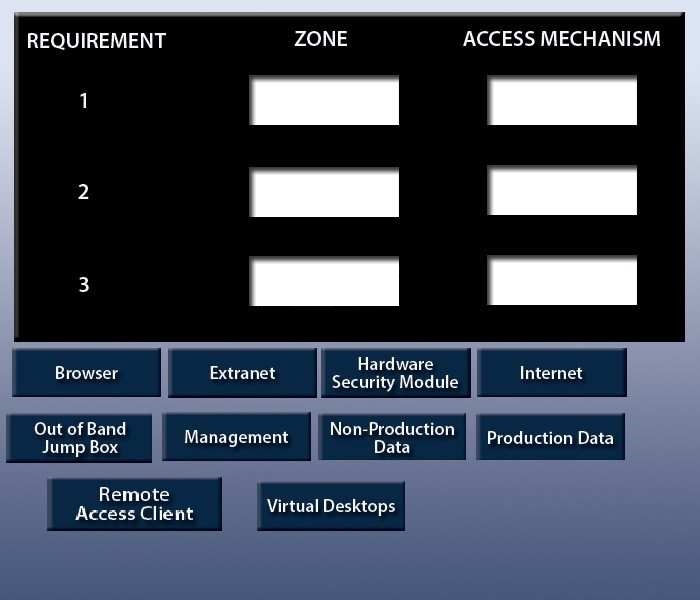
drag and drop the appropriate network zone that the user would be accessing…
DRAG DROP
A manufacturer is planning to build a segregated network. There are requirements to segregate development and test infrastructure from production and the need
to support multiple entry points into the network depending on the service being accessed. There are also strict rules in place to only permit user access from within
the same zone. Currently, the following access requirements have been identified:
1. Developers have the ability to perform technical validation of development applications.
2. End users have the ability to access internal web applications.
3. Third-party vendors have the ability to support applications.
In order to meet segregation and access requirements, drag and drop the appropriate network zone that the user would be accessing and the access mechanism
to meet the above criteria. Options may be used once or not at all. All placeholders must be filled.
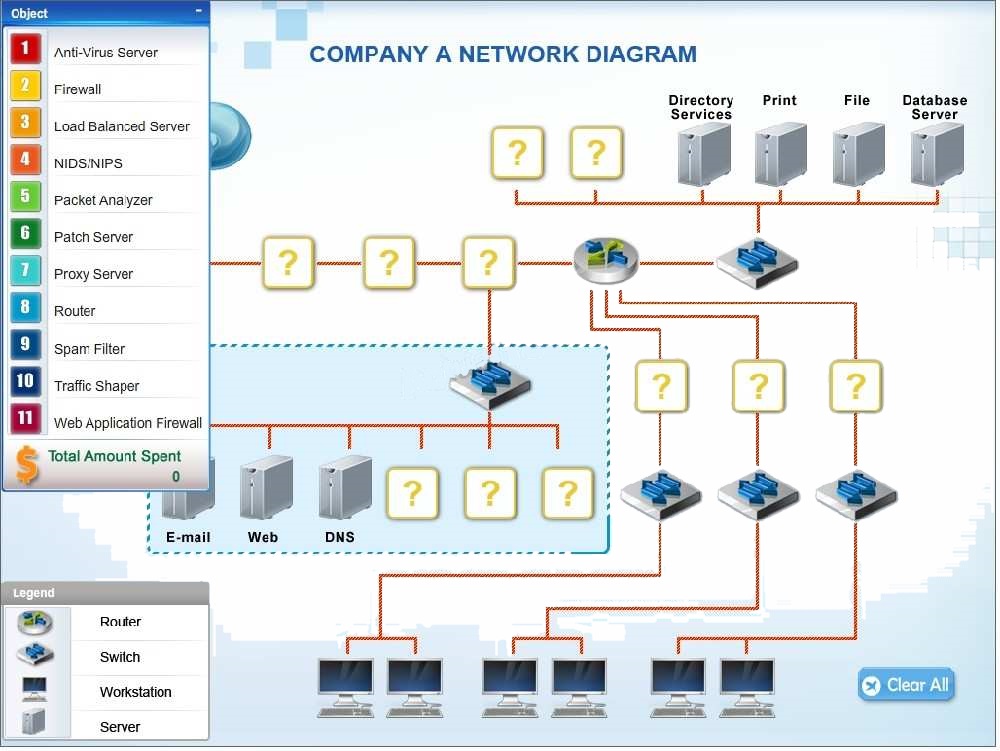
Company A has experienced external attacks on their network and wants to minimize…
DRAG DROP
Company A has experienced external attacks on their network and wants to minimize the attacks from reoccurring. Modify the network diagram to prevent SQL
injections, XSS attacks, smurf attacks, e-mail spam, downloaded malware, viruses and ping attacks. The company can spend a MAXIMUM of $50,000 USD. A cost
list for each item is listed below:
1. Anti-Virus Server – $10,000
2. Firewall-$15,000
3. Load Balanced Server – $10,000
4. NIDS/NIPS-$10,000
5. Packet Analyzer – $5,000
6. Patch Server-$15,000
7. Proxy Server-$20,000
8. Router-$10,000
9. Spam Filter-$5,000
10. Traffic Shaper – $20,000
11. Web Application Firewall – $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once.
If you place an object on the network diagram, you can remove it by clicking the (x) in the upper right-hand of the object.
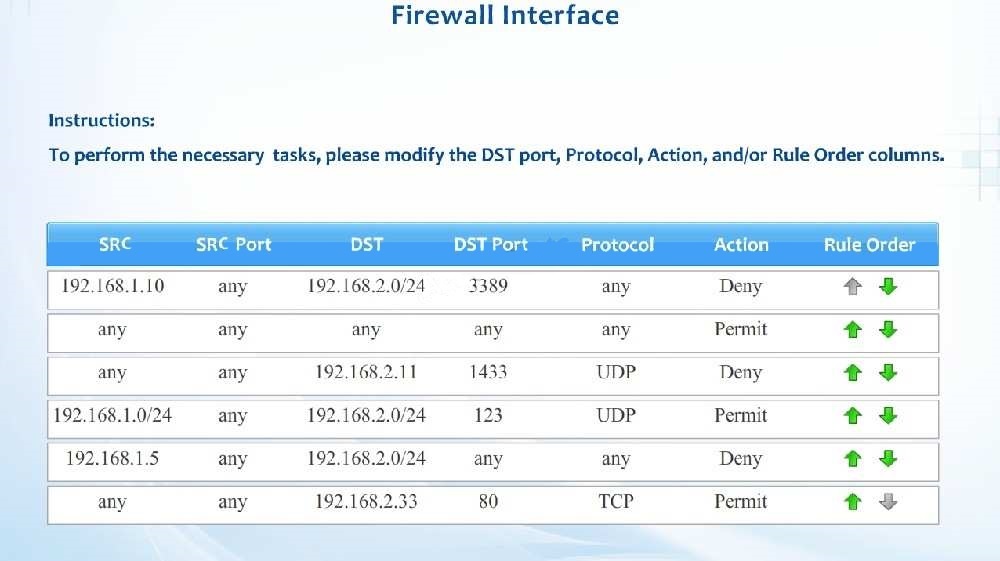
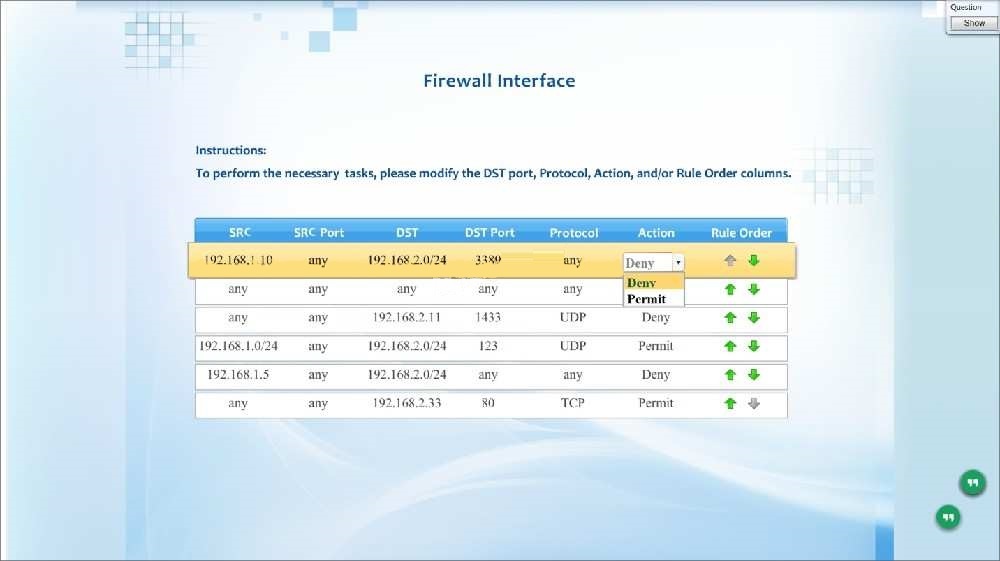
A new administrator is asked to conduct this review on the internal firewall sitting…
CORRECT TEXT
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting
between several Internal networks. The intent of this firewall is to make traffic more restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this
issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.