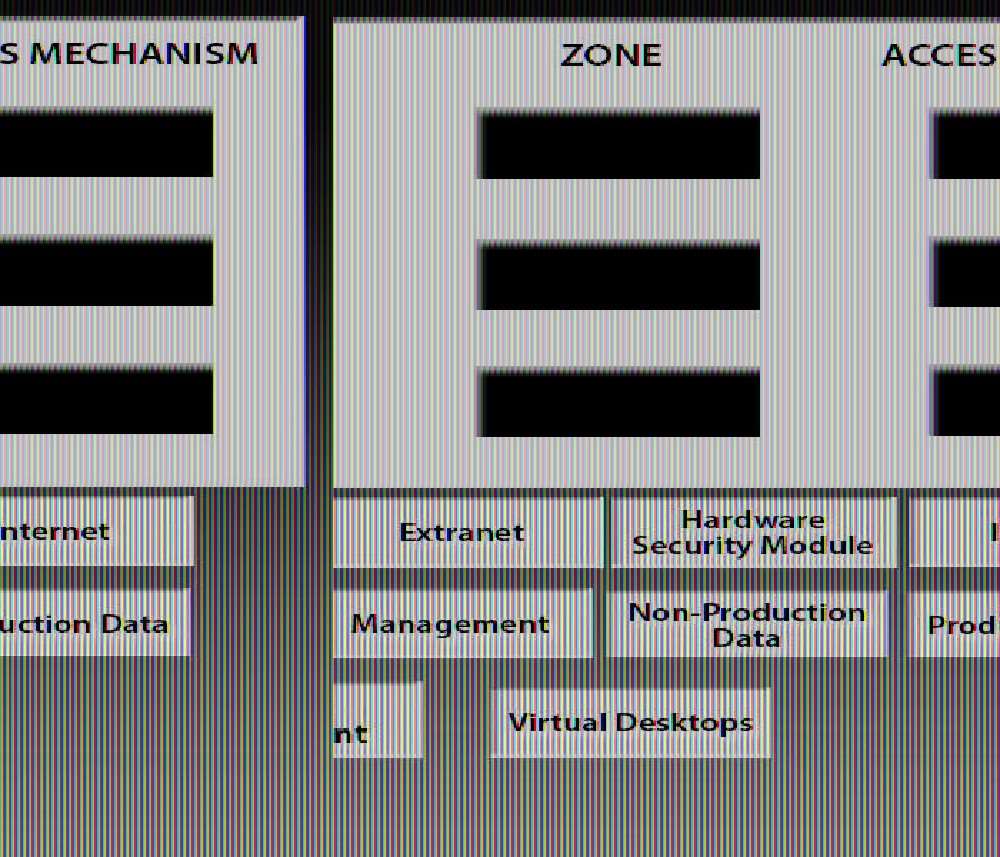
A manufacturer is planning to build a segregated network.
DRAG DROP
A manufacturer is planning to build a segregated network. There are requirements to segregate development
and test infrastructure from production and the need to support multiple entry points into the network depending
on the service being accessed. There are also strict rules in place to only permit user access from within the
same zone. Currently, the following access requirements have been identified:
1. Developers have the ability to perform technical validation of development applications.
2. End users have the ability to access internal web applications.
3. Third-party vendors have the ability to support applications. In order to meet segregation and access
requirements, drag and drop the appropriate network zone that the user would be accessing and the access
mechanism to meet the above criteria. Options may be used once or not at all. All placeholders must be filled.
Which of the following recommendations would BEST meet …
A security administrator has been asked to select a cryptographic algorithm to meet the criteria of a new
application. The application utilizes streaming video that can be viewed both on computers and mobile devices.
The application designers have asked that the algorithm support the transport encryption with the lowest
possible performance overhead. Which of the following recommendations would BEST meet the needs of the
application designers? (Select TWO).
Company A has experienced external attacks on their network…
DRAG DROP
Company A has experienced external attacks on their network and wants to minimize the attacks from
reoccurring. Modify the network diagram to prevent SQL injections, XSS attacks, smurf attacks, e-mail spam,
downloaded malware, viruses and ping attacks. The company can spend a MAXIMUM of $50,000 USD. A cost
list for each item is listed below:
1. Anti-Virus Server – $10,000
2. Firewall-$15,000
3. Load Balanced Server – $10,000 4. NIDS/NIPS-$10,000
5. Packet Analyzer – $5,000
6. Patch Server-$15,000
7. Proxy Server-$20,000 8. Router-$10,000
9. Spam Filter-$5,000
10. Traffic Shaper – $20,000
11. Web Application Firewall – $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once. If you place
an object on the network diagram, you can remove it by clicking the (x) in the upper right-hand of the object.
Which of the following logs and vulnerabilities would M…
A security manager looked at various logs while investigating a recent security breach in the data center from
an external source. Each log below was collected from various security devices compiled from a report through
the company’s security information and event management server.
Logs: Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets
Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has
disconnected the client
Log 4:
Encoder oe = new OracleEncoder ();
String query = “Select user_id FROM user_data WHERE user_name = ` ” + oe.encode ( req.getParameter
(“userID”) ) + ” ` and user_password = ` ” + oe.encode ( req.getParameter(“pwd”) ) +” ` “;
Vulnerabilities Buffer overflow SQL injection ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select
TWO).
Which of the following should Ann perform to test wheth…
Ann is testing the robustness of a marketing website through an intercepting proxy. She has intercepted the
following HTTP request:
POST /login.aspx HTTP/1.1 Host: comptia.org
Content-type: text/html
txtUsername=ann&txtPassword=ann&alreadyLoggedIn=false&submit=true Which of the following should Ann
perform to test whether the website is susceptible to a simple authentication bypass?
Which of the following are security weaknesses in this …
A penetration tester is inspecting traffic on a new mobile banking application and sends the following web
request:
POST http://www.example.com/resources/NewBankAccount HTTP/1.1 Content-type:
application/json
{
“account”: [
{ “creditAccount”:”Credit Card Rewards account”}
{ “salesLeadRef”:”www.example.com/badcontent/exploitme.exe”} ],
“customer”: [
{ “name”:”Joe Citizen”} { “custRef”:”3153151″}
]}
The banking website responds with: HTTP/1.1 200 OK {
“newAccountDetails”: [
{ “cardNumber”:”1234123412341234″} { “cardExpiry”:”2020-12-31″} { “cardCVV”:”909″}
],
“marketingCookieTracker”:”JSESSIONID=000000001″ “returnCode”:”Account added successfully”
}
Which of the following are security weaknesses in this example? (Select TWO).
Which of the following are the MOST appropriate courses…
Customers are receiving emails containing a link to malicious software. These emails are subverting spam
filters. The email reads as follows:
Delivered-To: customer@example.com Received: by 10.14.120.205 Mon, 1 Nov 2010 11:15:24 -0700 (PDT)
Received: by 10.231.31.193
Mon, 01 Nov 2010 11:15:23 -0700 (PDT)
Return-Path: <IT@company.com>
Received: from 127.0.0.1 for <customer@example.com>; Mon, 1 Nov 2010 13:15:14 -0500 (envelope-from
<IT@company.com>)
Received: by smtpex.example.com (SMTP READY) with ESMTP (AIO); Mon, 01 Nov 2010
13:15:14 -0500
Received: from 172.18.45.122 by 192.168.2.55; Mon, 1 Nov 2010 13:15:14 -0500 From: Company
<IT@Company.com>
To: “customer@example.com” <customer@example.com> Date: Mon, 1 Nov 2010 13:15:11 – Subject: New
Insurance Application Thread-Topic: New Insurance Application Please download and install software from the
site below to maintain full access to your account.
www.examplesite.comAdditional information: The authorized mail servers IPs are 192.168.2.10 and 192.168.2.11. The network’s
subnet is 192.168.2.0/25. Which of the following are the MOST appropriate courses of action a security
administrator could take to eliminate this risk? (Select TWO).
Which of the following iscritical to ensure the success…
A bank has decided to outsource some existing IT functions and systems to a third party service provider. The
third party service provider will manage the outsourced systems on their own premises and will continue to
directly interface with the bank’s other systems through dedicated encrypted links. Which of the following iscritical to ensure the successful management of system security concerns between the two organizations?
Which of the following preventative controls would MOST…
The Chief Information Security Officer (CISO) at a large organization has been reviewing some security-related
incidents at the organization and comparing them to current industry trends. The desktop security engineerfeels that the use of USB storage devices on office computers has contributed to the frequency of security
incidents. The CISO knows the acceptable use policy prohibits the use of USB storage devices. Every user
receives a popup warning about this policy upon login. The SIEM system produces a report of USB violations
on a monthly basis; yet violations continue to occur. Which of the following preventative controls would MOST
effectively mitigate the logical risks associated with the use of USB
storage devices?
Which of the following preventative controls would MOST…
The Chief Information Security Officer (CISO) at a large organization has been reviewing some security-related
incidents at the organization and comparing them to current industry trends. The desktop security engineerfeels that the use of USB storage devices on office computers has contributed to the frequency of security
incidents. The CISO knows the acceptable use policy prohibits the use of USB storage devices. Every user
receives a popup warning about this policy upon login. The SIEM system produces a report of USB violations
on a monthly basis; yet violations continue to occur. Which of the following preventative controls would MOST
effectively mitigate the logical risks associated with the use of USB
storage devices?