which of the following steps in system authorizationhas…
A security engineer is a new member to a configuration board at the request of management. The company
has two new major IT projects starting this year and wants to plan security into the application deployment. The
board is primarily concerned with the applications’ compliance with federal assessment and authorization
standards. The security engineer asks for a timeline to determine when a security assessment of both
applications should occur and does not attend subsequent configuration board meetings. If the security
engineer is only going to perform a security assessment, which of the following steps in system authorizationhas the security engineer omitted?
which of the following media will need to utilized?
The human resource department has been moved to an area which is more than 60 meters away from the
nearest IDF. In order to comply with the SLA which requires that 10Gb speeds be provided, which of the
following media will need to utilized?
Which of the following will reduce this attack in the n…
There has been an increased amount of successful social engineering attacks at a corporate office. Which of
the following will reduce this attack in the near future?
Which of the following topologies is in use?
A network administrator noticed that when one computer goes down, all the other computers in the office will
not work. Which of the following topologies is in use?
which of the following did the administrator forget to …
The administrator modifies a rule on the firewall, and now all the FTP users cannot access the server any
longer. The manager calls the administrator and asks what caused the extreme downtime for the server. In
regards to the manager’s inquiry, which of the following did the administrator forget to do FIRST?
Which of the following DNS records need to be configure…
A company installs a new mail server. Which of the following DNS records need to be configured to allow the
organization to receive email?
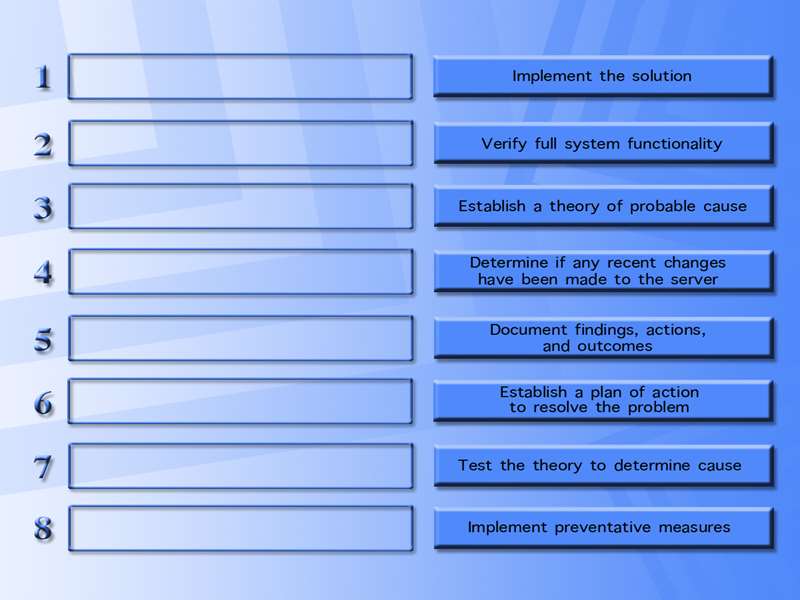
Arrange the troubleshooting steps in the order the tech…
Select and Place:
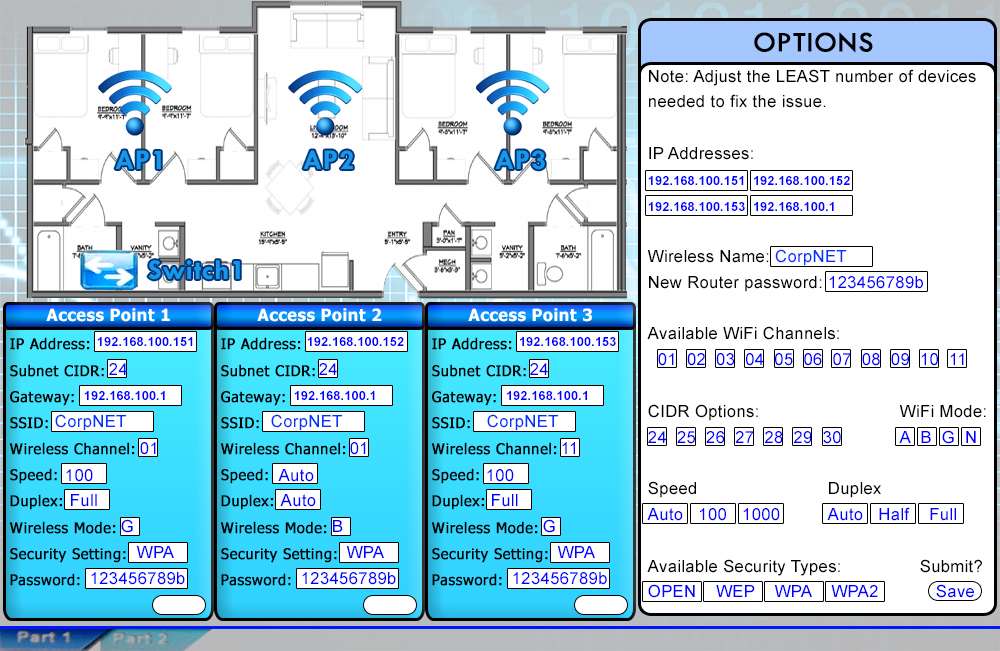
Wireless network users recently began experiencing speed and performance issues after access point 2 (AP2)
was replaced due to faulty hardware. The original network was installed according to a consultant’s
specifications and has always worked without a problem.
You a network technician, have been tasked with evaluating the situation and resolving the issues to improve
both performance and connectivity. Refer to the following exhibits and perform any necessary changes to the
wireless and wired infrastructure by adjusting devices. Note: Adjust the LEAST number of devices needed to fix
the issue.
Select and Place:
Select and Place:
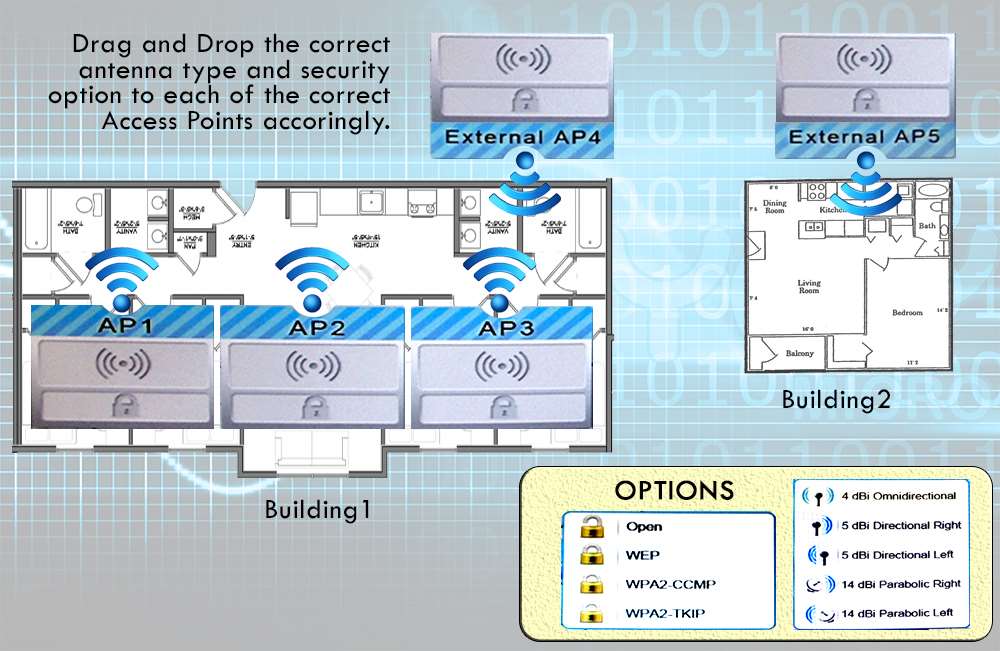
Your company recently purchased a new building down the street from the existing office.
For each of the tasks below, select the appropriate antenna type and encryption object for all wireless access
point (AP).
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation,
while maximizing security.
2. Restrict the wireless signal generated by the access points (AP’s) inside Building 1, so that it minimizes
broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1’s internal wireless network is for visitors only and must not require any special configuration on
the visitor’s device to connect.
Select and Place:
Select and Place:
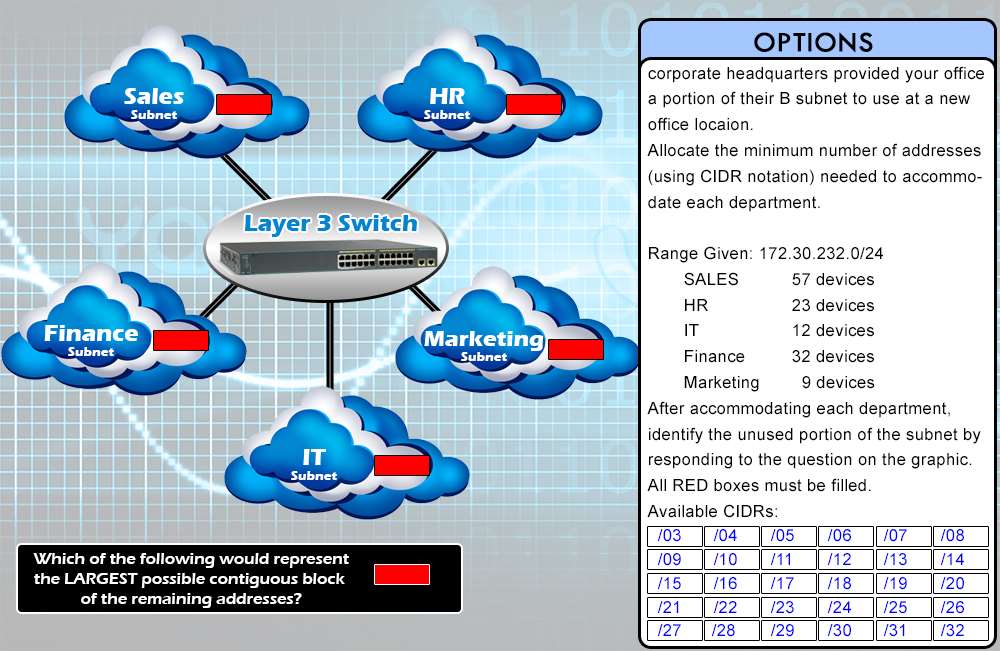
corporate headquarters provided your office a portion of their B subnet to use at a new office locaion.
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
Range Given: 172.30.232.0/24
SALES 57 devices
HR 23 devices
IT 12 devices
Finance 32 devicesMarketing 9 devices
After accommodating each department, identify the unused portion of the subnet by responding to the question
on the graphic. All RED boxes must be filled.
Select and Place: