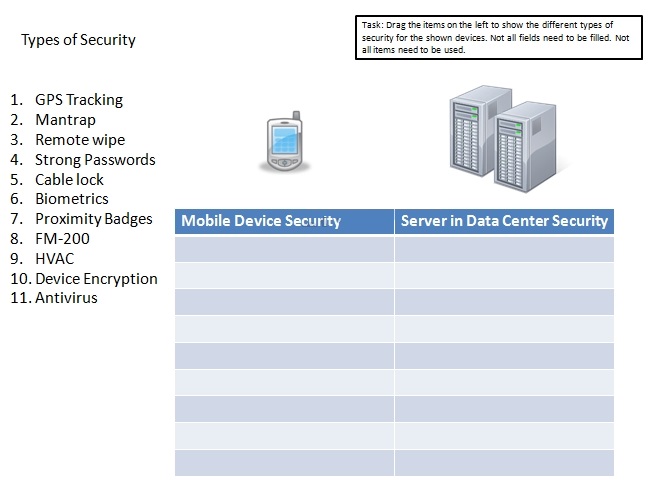
Drag the items “Types of Security” to appropriate Security devices.
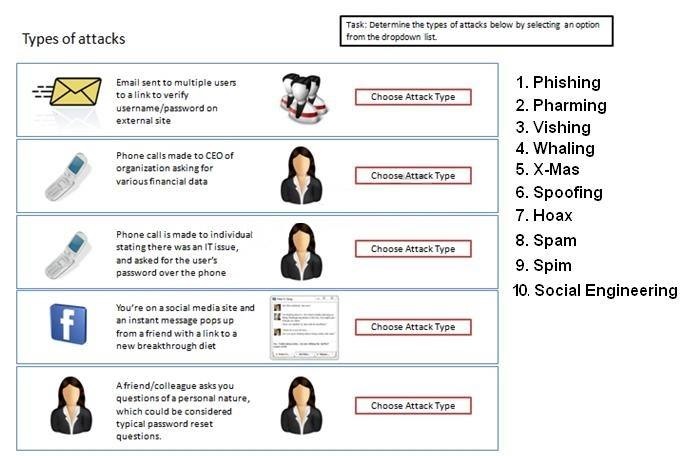
Determine the types of Attacks from right to specific action.
Drag and Drop the applicable controls to each asset type.
DRAG DROP
A Security administrator wants to implement strong security on the company smart phones and
terminal servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all placeholders needs to be filled. When
you have completed the simulation, Please select Done to submit.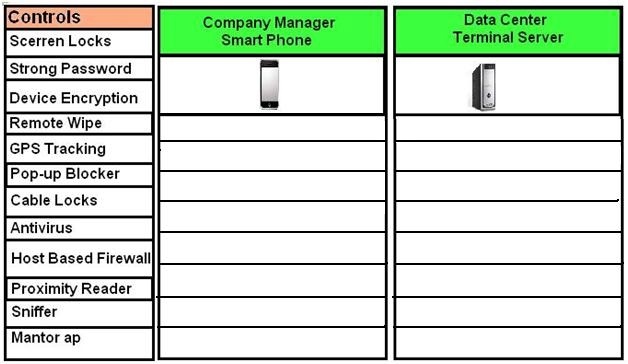
Which of the following does Kerberos require for correct operation?
A real estate company recently deployed Kerberos authentication on the network. Which of the
following does Kerberos require for correct operation? (Select TWO).
Which of the following devices could be selected to provide security to the network segment?
An administrator is selecting a device to secure an internal network segment from traffic external
to the segment. Which of the following devices could be selected to provide security to the network
segment?
Which of the following are MOST likely to be analyzed by Internet filter appliances/servers?
401.Which of the following are MOST likely to be analyzed by Internet filter appliances/servers?
(Select THREE).401.Which of the following are MOST likely to be analyzed by Internet filter
appliances/servers? (Select THREE).
Which of the following provides the BEST security and accountability for a Data Center?
Which of the following provides the BEST security and accountability for a Data Center?
Which of the following VPN implementations consists of taking IPv6 security features and porting them to IPv4?
Which of the following VPN implementations consists of taking IPv6 security features and porting
them to IPv4?
Which of the following slots, if available, would offer the highest bandwidth?
Which of the following slots, if available, would offer the highest bandwidth?
which of the following types of access control models?
A user is assigned access rights based on the function within the organization. This is a feature of
which of the following types of access control models?