Determine the types of Attacks from right to specific action.
Drag and Drop the applicable controls to each asset type.
DRAG DROP
A Security administrator wants to implement strong security on the company smart phones and
terminal servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all placeholders needs to be filled. When
you have completed the simulation, Please select Done to submit.
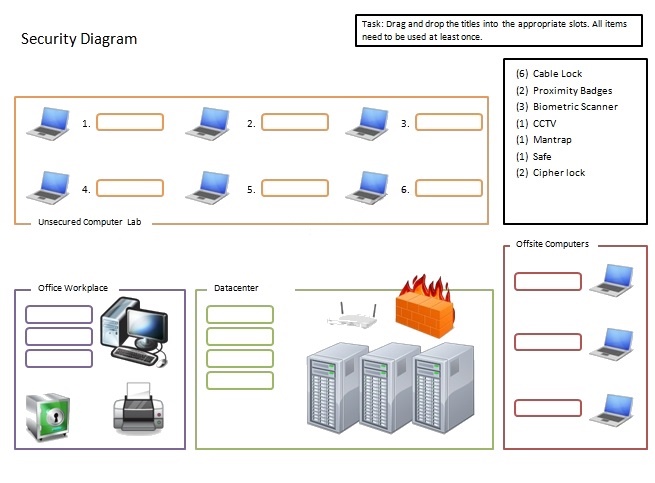
Drag the appropriates titles into the correct slots.
Which of the following is the BEST approach to perform risk mitigation of user access control rights?
Which of the following is the BEST approach to perform risk mitigation of user access control
rights?
Which of the following is the BEST approach to perform risk mitigation of user access control rights?
Which of the following is the BEST approach to perform risk mitigation of user access control
rights?
Which of the following devices is BEST suited for servers that need to store private keys?
Which of the following devices is BEST suited for servers that need to store private keys?
Which of the following devices is BEST suited for servers that need to store private keys?
Which of the following devices is BEST suited for servers that need to store private keys?
All of the following are valid cryptographic hash functions EXCEPT:
All of the following are valid cryptographic hash functions EXCEPT:
All of the following are valid cryptographic hash functions EXCEPT:
All of the following are valid cryptographic hash functions EXCEPT:
why is input validation important?
In regards to secure coding practices, why is input validation important?