What surge-suppressor rating describes how quickly its protective circuitry can react to change in the incomin
What surge-suppressor rating describes how quickly its protective circuitry can react to change in the
incoming line and limit the amount of change that passes through?
Instructions The last install that is completed will be the final submission
Drag and Drop the following information types on to the appropriate CIA category
Which of the following procedures should be run in order to make sure that there are no crosslinked files?
Which of the following procedures should be run in order to make sure that there are no crosslinked files?
CORRECT TEXT To perform the necessary tasks, please modify the DST port, protocol
what type of fire extinguisher should you have on hand?
When working around electrical equipment, including computers, what type of fire extinguisher should you
have on hand?
Which of the following is the cause of this?
A monitor is running at a high resolution, but the image is somewhat blurred. Which of the following
is the cause of this?
Which of the following designs is BEST suited for this purpose?
A startup company offering software on demand has hired a security consultant to provide
expertise on data security. The company’s clients are concerned about data confidentiality. The
security consultant must design an environment with data confidentiality as the top priority, over
availability and integrity. Which of the following designs is BEST suited for this purpose?
Modify the network diagram to prevent SQL injections. XSS attacks, smurf attacks, e-mail spam, downloaded malw
DRAG DROP
Company A has experienced external attacks on their network and wants to minimize the attacks
from reoccurring. Modify the network diagram to prevent SQL injections. XSS attacks, smurf
attacks, e-mail spam, downloaded malware. viruses and ping attacks. The company can spend a
MAXIMUM of 550.000 USD. A cost list for each item is listed below
1. Anti-Virus Server- $10,000
2 Firewall-$15,000
3 Load Balanced Server – $10,000
4 NIDS/NIPS-$10,000
5. Packet Analyzer-55.000
6 Patch Server-$15,000
7 Proxy Server-$20,000 8. Router – S10.000
9 Spam Filter – S5 000
10 Traffic Shaper – $20,000
11. Web Application Firewall – $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once.

Based on this information, the following tasks need to be completed:
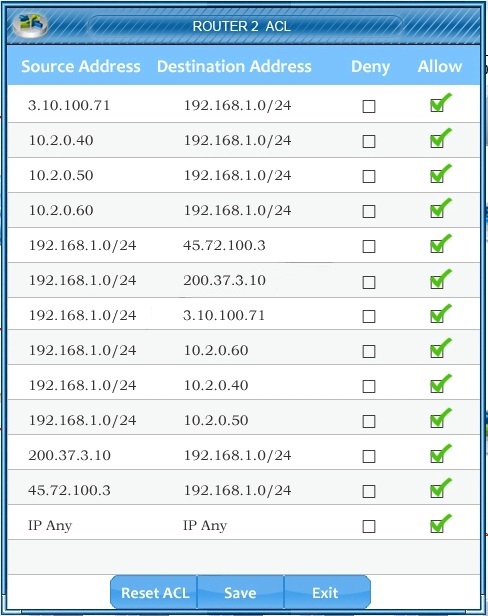
CORRECT TEXT
The IDS has detected abnormal behavior on this network Click on the network devices to view
device information Based on this information, the following tasks need to be completed:
1. Select the server that is a victim of a SQL injection attack.
2 Select the source of the buffer overflow attack.
3. Modify the access control list (ACL) on the router(s) to ONLY block the buffer overflow attack.
Instructions: Simulations can be reset at any time to the initial state: however, all selections will be deleted.