Which of the following could be utilized to notify the …
Recently, the desktop support group has been performing a hardware refresh and has replaced numerous
computers. An auditor discovered that a number of the new computers did not have the company’s antivirus
software installed on them. Which of the following could be utilized to notify the network support group when
computers without the antivirus software are added to the network?
Which of the following can be mitigated with proper sec…
Which of the following can be mitigated with proper secure coding techniques?
Which of the following types of malware MOST likely cau…
An employee reports work was being completed on a company-owned laptop using a public wireless hot-spot.
A pop-up screen appeared, and the user closed the pop-up. Seconds later, the desktop background was
changed to the image of a padlock with a message demanding immediate payment to recover the data. Which
of the following types of malware MOST likely caused this issue?
which of the following sets of permissions should have …
During a Linux security audit at a local college, it was noted that members of the dean’s group were able to
modify employee records in addition to modifying student records, resulting in an audit exception. The college
security policy states that the dean’s group should only have the ability to modify student records. Assuming
that the correct user and group ownerships are in place, which of the following sets of permissions should have
been assigned to the directories containing the employee records?
Which of the following should the security manager impl…
A security manager received reports of several laptops containing confidential data stolen out of a lab
environment. The lab is not a high security area and is secured with physical key locks. The security manager
has no information to provide investigators related to who may have stolen the laptops. Which of the following
should the security manager implement to improve legal and criminal investigations in the future?
Which of the following options will BEST accomplish thi…
A security administrator would like to ensure that some members of the building’s maintenance staff are only
allowed access to the facility during weekend hours. Access to the facility is controlled by badge swipe and a
man trap. Which of the following options will BEST accomplish this goal?
Which of the following sections of the proposal would b…
A project manager is evaluating proposals for a cloud commuting project. The project manager is particularly
concerned about logical security controls in place at the service provider’s facility. Which of the following
sections of the proposal would be MOST important to review, given the project manager’s concerns?
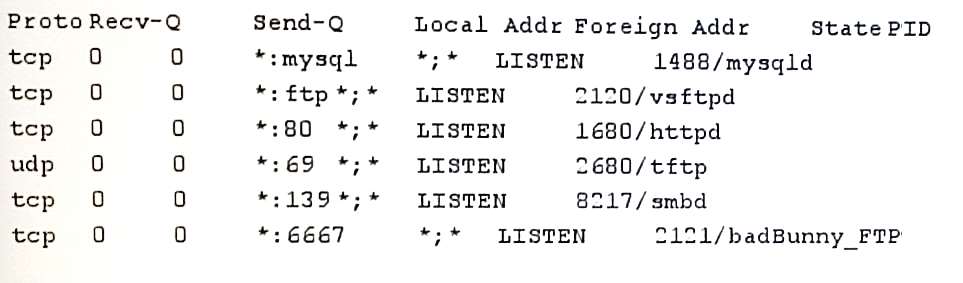
Which of the following processes can the administrator …
An administrator is hardening systems and wants to disable unnecessary services. One Linux server hosts files
used by a Windows web server on another machine. The Linux server is only used for secure file transfer, but
requires a share for the Windows web server as well. The administrator sees the following output from a netstat
-1p command:
Which of the following processes can the administrator kill without risking impact to the purpose and function of
the Linux or Windows servers? (Choose Three)
Which of the following can be implemented to provide sy…
A new employee has been hired to perform system administration duties across a large enterprise comprised of
multiple separate security domains. Each remote location implements a separate security domain. The new
employee has successfully responded to and fixed computer issues for the main office. When the new
employee tries to perform work on remote computers, the following messages appears. You need permission
to perform this action. Which of the following can be implemented to provide system administrators with the
ability to perform administrative tasks on remote computers using their uniquely assigned account?
which of the following system components FIRST?
A security administrator working for a law enforcement organization is asked to secure a computer system at
the scene of a crime for transport to the law enforcement forensic facility. In order to capture as much evidence
as possible, the computer system has been left running.
The security administrator begins information by image which of the following system components FIRST?