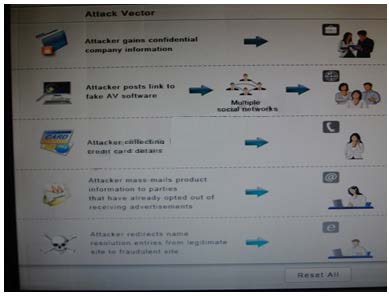
Select the appropriate attack from each drop down list to label the corresponding illustrated attack.
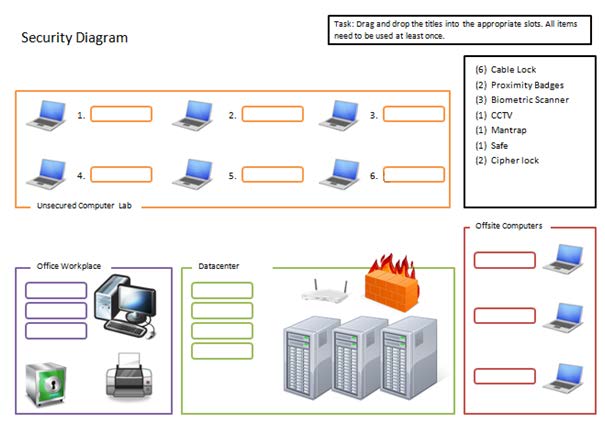
Drag and drop the appropriate security controls on the floor plan.
DRAG DROP
You have been tasked with designing a security plan for your company. Drag and drop the
appropriate security controls on the floor plan.
Instructions:All objects must be used and all place holders must be filled. Order does not
matter. When you have completed the simulation, please select the Done button to submit.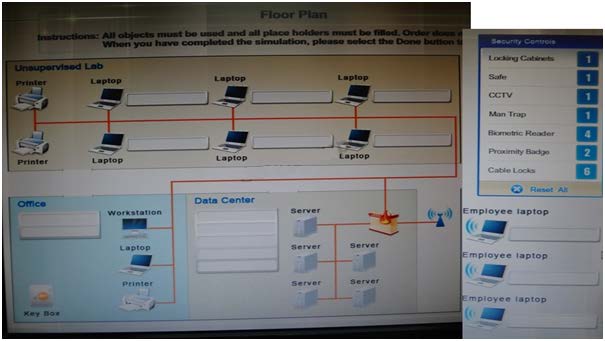
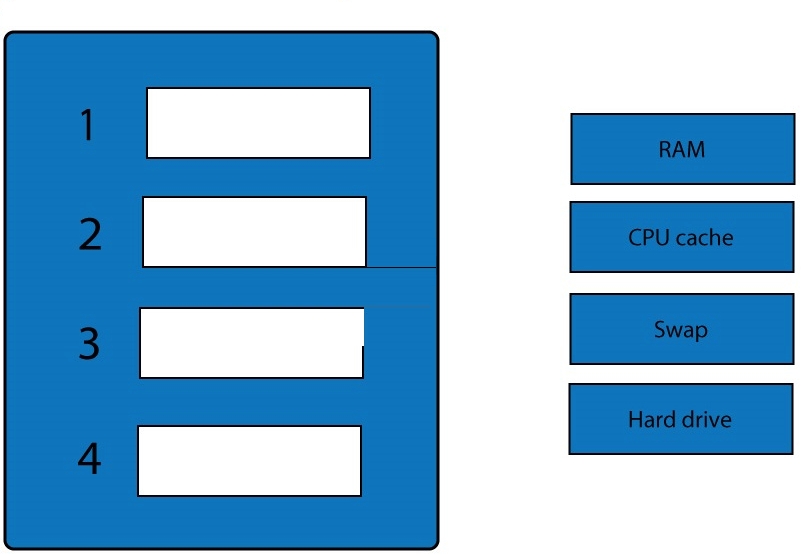
Place the items in the list below in the correct order in which the forensic analyst should preserve them.
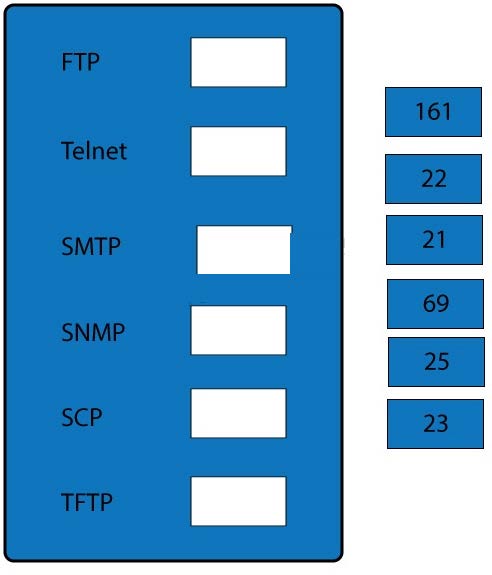
Drag and drop the correct protocol to its default port.
Which of the following helps to prevent virus infections from USB flash drives?
Which of the following helps to prevent virus infections from USB flash drives?
Which of the following expansion cards would MOST likely have the requirements of utilizing a direct auxiliary
Which of the following expansion cards would MOST likely have the requirements of utilizing a direct
auxiliary 6-pin power plug to operate properly?
Which of the following protocols operates at the HIGHEST level of the OSI model?
Which of the following protocols operates at the HIGHEST level of the OSI model?