Which of the following BEST represents the goal of a vulnerability assessment?
Which of the following BEST represents the goal of a vulnerability assessment?
Which of the following protocols handles the reliable delivery of data?
Which of the following protocols handles the reliable delivery of data?
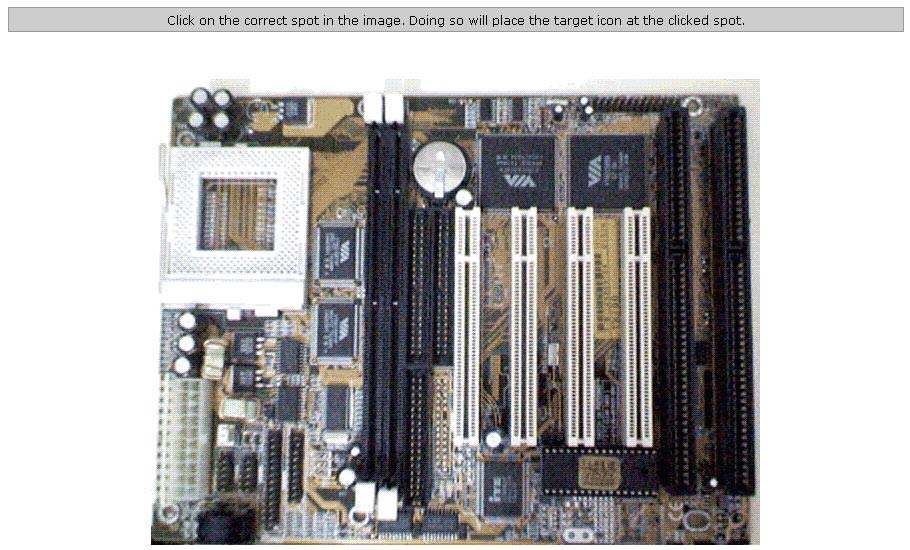
Identify the area showing the DIMM slots in the image of the motherboard.
Which of the following are Data Loss Prevention (DLP) strategies that address data in transit issues?
Which of the following are Data Loss Prevention (DLP) strategies that address data in transit
issues? (Select TWO).
Which of the following should be completed before allowing users to self provision their devices?
An organization is going to deploy a BYOD model to allow users to provision their personally
owned devices to receive email on their mobile devices. Which of the following should be
completed before allowing users to self provision their devices? (Select TWO).
Which of the following uses 802.1q?
Which of the following uses 802.1q?
Which of the following statements about crontab are true?
Which of the following statements about crontab are true? (Select TWO).
Which of the following tools would an administrator use to determine if a DNS server is answering authoritativ
Which of the following tools would an administrator use to determine if a DNS server is
answering authoritatively for a domain?
What command is used to display a file in octal format?
CORRECT TEXT
What command is used to display a file in octal format? (Please enter only a single command and do
not enter duplicate answers in this field.)
which of the following?
SAN zoning provides which of the following?