Which of the following configuration files does sudo read when determining if a user is permitted to run appli
Which of the following configuration files does sudo read when determining if a user is
permitted to run applications with root privileges?
Which of the following tools should be used to determine the listening port of the web server?
A web server is running correctly but sending a RST packet to any client trying to connect
using HTTP on TCP port 80. Which of the following tools should be used to determine the
listening port of the web server?
Which of the following is the process ID number of the init program?
Which of the following is the process ID number of the init program?
Which of the following is the purpose of ISL?
Which of the following is the purpose of ISL?
Which of the following is BEST utilized to identify common misconfigurations throughout the enterprise?
Which of the following is BEST utilized to identify common misconfigurations throughout the
enterprise?
Which of the following can be utilized in order to provide temporary IT support during a disaster…?
Which of the following can be utilized in order to provide temporary IT support during a disaster,
where the organization sets aside funds for contingencies, but does not necessarily have a
dedicated site to restore those services?
Which of the following storage device uses SRAM or DRAM?
Which of the following storage device uses SRAM or DRAM?
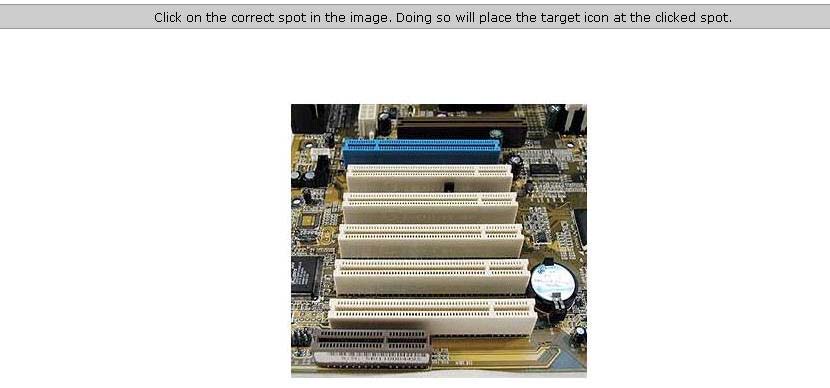
Identify the CNR slot in the image given below.
Which of the following should be recommended to isolate the VMs from one another?
A technician is deploying virtual machines for multiple customers on a single physical host to
reduce power consumption in a data center. Which of the following should be recommended to
isolate the VMs from one another?
Which of the following are components of a predictive wireless audit?
The mobility team has been tasked with placing Wi-Fi access points in a conference room. They
have been provided with a floor plan by the building architect. Which of the following are
components of a predictive wireless audit? (Select TWO).