Which of the following actions should the administrator take?
The security administrator notices a user logging into a corporate Unix server remotely as root.
Which of the following actions should the administrator take?
Which of the following should be in place?
A company has two server administrators that work overnight to apply patches to minimize
disruption to the company. With the limited working staff, a security engineer performs a risk
assessment to ensure the protection controls are in place to monitor all assets including the
administrators in case of an emergency. Which of the following should be in place?
Which of the following describes the disaster?
A company’s Chief Information Officer realizes the company cannot continue to operate after a
disaster. Which of the following describes the disaster?
Which of the following is MOST appropriate to use?
A company plans to expand by hiring new engineers who work in highly specialized areas. Each
engineer will have very different job requirements and use unique tools and applications in their
job. Which of the following is MOST appropriate to use?
Which of the following is the CTO concerned with?
Ann, the Chief Technology Officer (CTO), has agreed to allow users to bring their own device
(BYOD) in order to leverage mobile technology without providing every user with a company
owned device. She is concerned that users may not understand the company’s rules, and she
wants to limit potential legal concerns. Which of the following is the CTO concerned with?
Which of the following solutions provides the most flexibility when testing new security controls prior to imp
Which of the following solutions provides the most flexibility when testing new security controls
prior to implementation?
Which of the following should be modified to assure that Ann has read access to the file?
A file on a Linux server has default permissions of rw-rw-r–. The system administrator has verified
that Ann, a user, is not a member of the group owner of the file. Which of the following should be
modified to assure that Ann has read access to the file?
The security administrator has installed a new firewall which implements an implicit DENY policy by default
HOTSPOT
The security administrator has installed a new firewall which implements an implicit DENY policy
by default Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the
default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over
the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over
the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match
The port number must be typed in and only one port number can be entered per rule Type ANY for
all ports. The original firewall configuration can be reset at any time by pressing the reset button.
Once you have met the simulation requirements, click save and then Done to submit.
A security administrator is given the security and availability profiles for servers that are being deployed.
DRAG DROP
A security administrator is given the security and availability profiles for servers that are being
deployed.
1) Match each RAID type with the correct configuration and MINIMUM number of drives.
2) Review the server profiles and match them with the appropriate RAID type based on integrity,
availability, I/O, storage requirements. Instructions:
• All drive definitions can be dragged as many times as necessary
• Not all placeholders may be filled in the RAID configuration boxes
• If parity is required, please select the appropriate number of parity checkboxes
• Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset
button. When you have completed the simulation, please select the Done button to submit. Once
the simulation is submitted, please select the Next button to continue.
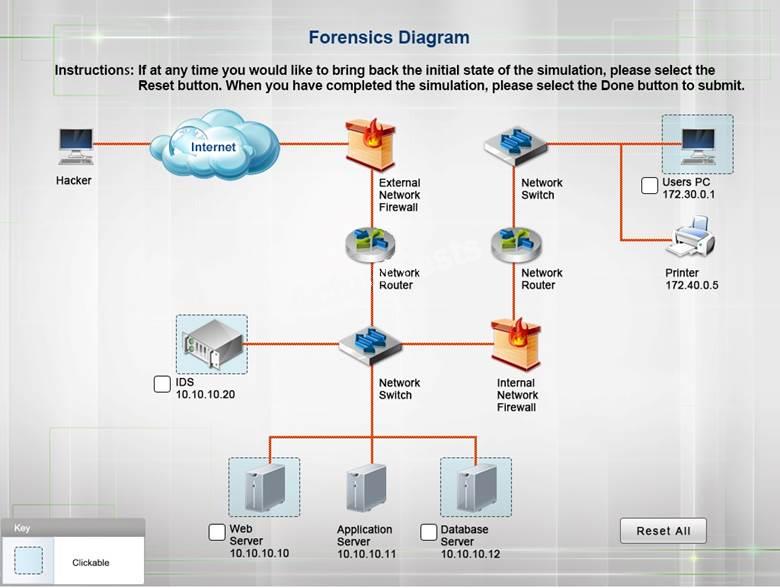
drag and drop the appropriate actions to complete the incident response on the network.
CORRECT TEXT
A security administrator discovers that an attack has been completed against a node on the
corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s)
that have been compromised and drag and drop the appropriate actions to complete the incident
response on the network. The environment is a critical production environment; perform the
LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of
the node(s) that have been compromised and drag and drop the appropriate actions to complete
the incident response on the network. Not all actions may be used, and order is not important. If at
anytime you would like to bring back the initial state of the simulation, please select the Reset
button. When you have completed the simulation, please select the Done button to submit. Once
the simulation is submitted, please select the Next button to continue.