Which of the following is best practice to put at the end of an ACL?
Which of the following is best practice to put at the end of an ACL?
Which of the following is best practice to put at the end of an ACL?
Which of the following is best practice to put at the end of an ACL?
Which of the following is blocking network printing?
Users report that they are unable to access network printing services. The security technician
checks the router access list and sees that web, email, and secure shell are allowed. Which of the
following is blocking network printing?
Which of the following is blocking network printing?
Users report that they are unable to access network printing services. The security technician
checks the router access list and sees that web, email, and secure shell are allowed. Which of the
following is blocking network printing?
Which of the following authentication methods is Sara using?
In order for Sara, a client, to logon to her desktop computer, she must provide her username,
password, and a four digit PIN. Which of the following authentication methods is Sara using?
Which of the following authentication methods is Sara using?
In order for Sara, a client, to logon to her desktop computer, she must provide her username,
password, and a four digit PIN. Which of the following authentication methods is Sara using?
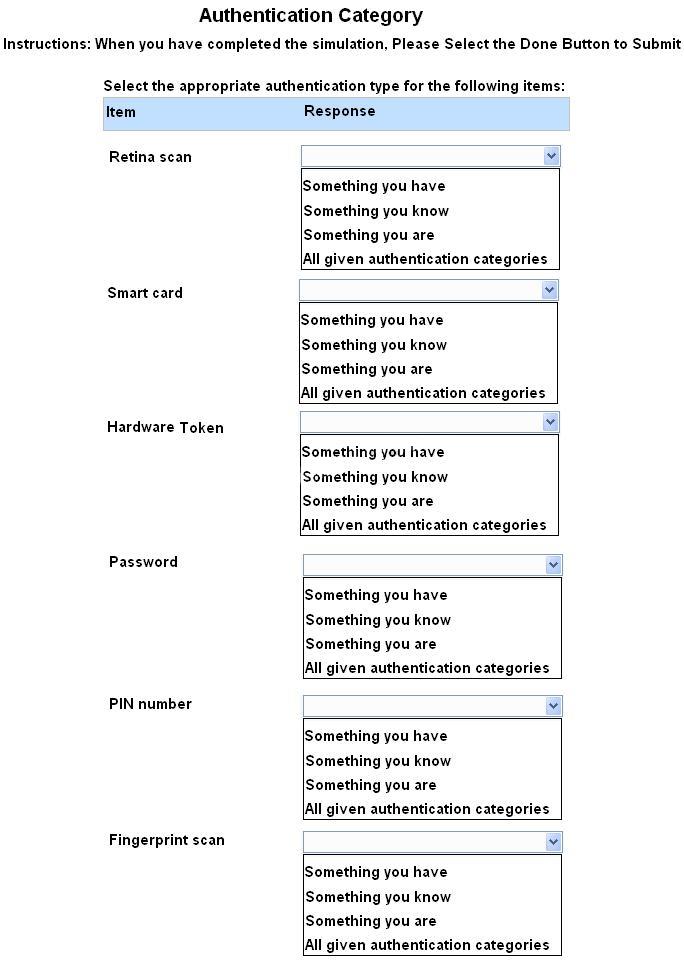
select the appropriate authentication category from the dropdown choices.
which of the following authentication types?
The security department has implemented a new laptop encryption product in the environment.
The product requires one user name and password at the time of boot up and also another
password after the operating system has finished loading. This setup is using which of the
following authentication types?
which rates the ability of a system to correctly authenticate an authorized user?
Which of the following is a measure of biometrics performance which rates the ability of a system
to correctly authenticate an authorized user?
which rates the ability of a system to correctly authenticate an authorized user?
Which of the following is a measure of biometrics performance which rates the ability of a system
to correctly authenticate an authorized user?