Which of the following technologies meet the compatibil…
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions. Which of the following technologies meet the compatibility requirement? (Select three.)
Which of the following is MOST likely to be incorporate…
A company wants to update its acceptable use policy (AUP) to ensure it relates to the newly implemented password standard, which requires sponsored authentication of guest wireless devices. Which of the following is MOST likely to be incorporated in the AUP?
Which of the following steps should be taken to assist …
An organization is requesting the development of a disaster recovery plan. The organization has grown and so has its infrastructure. Documentation, policies, and procedures do not exist. Which of the following steps should be taken to assist in the development of the disaster recovery plan?
Which of the following is the MOST secure solution to r…
A cybersecurity professional typed in a URL and discovered the admin panel for the e-commerce application is accessible over the open web with the default password. Which of the following is the MOST secure solution to remediate this vulnerability?
Which of the following techniques would BEST help the a…
An analyst has initiated an assessment of an organization’s security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally. Which of the following techniques would BEST help the analyst accomplish this goal? (Select two.)
Which of the following actions should be taken to remed…
A cybersecurity analyst is conducting a security test to ensure that information regarding the web server is protected from disclosure. The cybersecurity analyst requested an HTML file from the web server, and the response came back as follows: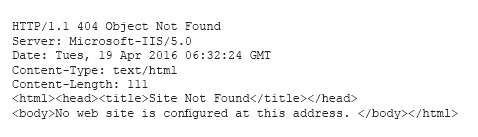
Which of the following actions should be taken to remediate this security issue? ref: http://www.acunetix.com/blog/articles/configure-web-server-disclose-identity/
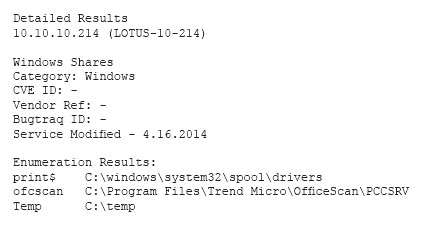
Which of the following describes the meaning of these r…
Which of the following software development best practi…
External users are reporting that a web application is slow and frequently times out when attempting to submit information. Which of the following software development best practices would have helped prevent this issue?
Which of the following attacks may be occurring?
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
what the analyst should do NEXT?
A security analyst has created an image of a drive from an incident. Which of the following describes what the analyst should do NEXT?