Which of the following items represents a document that…
Which of the following items represents a document that includes detailed information on when an incident was detected, how impactful the incident was, and how it was remediated, in addition to incident response effectiveness and any identified gaps needing improvement?
which of the following represents the MOST likely cause?
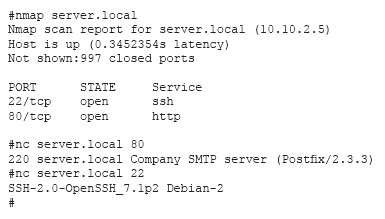
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
Which of the following is the BEST logical control to a…
An analyst finds that unpatched servers have undetected vulnerabilities because the vulnerability scanner does not have the latest set of signatures. Management directed the security team to have personnel update the scanners with the latest signatures at least 24 hours before conducting any scans, but the outcome is unchanged. Which of the following is the BEST logical control to address the failure?
Which of the following should the analyst implement?
An analyst has received unusual alerts on the SIEM dashboard. The analyst wants to get payloads that the hackers are sending toward the target systems without impacting the business operation. Which of the following should the analyst implement?
Which of the following can a system administrator infer…
Which of the following actions is the BEST approach for…
A cybersecurity analyst has several SIEM event logs to review for possible APT activity. The analyst was given several items that include lists of indicators for both IP addresses and domains. Which of the following actions is the BEST approach for the analyst to perform?
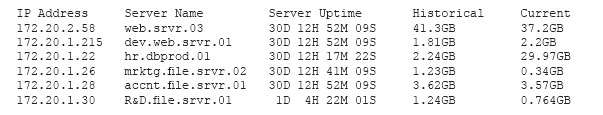
Which of the following servers needs further investigation?
which of the following should be remediated FIRST?
A recent vulnerability scan found four vulnerabilities on an organization’s public Internet-facing IP addresses.
Prioritizing in order to reduce the risk of a breach to the organization, which of the following should be remediated FIRST?
Which of the following steps should be taken to prevent…
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media.
The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
which phase of the SDLC should this occur?
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur?
(Select two.)