Which of the following MOST likely happened in this sit…
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the web proxy generated an alert regarding the same indicator. The threat intelligence analyst states that related sites were not visited but were searched for in a search engine. Which of the following MOST likely happened in this situation?
Which of the following recommendations would meet the n…
The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
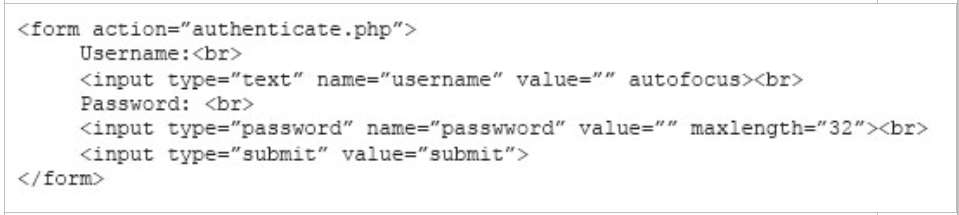
Which of the following ACLs, if implemented, will preve…
Which of the following can be employed to allow this?
Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company
A’s conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company
B’s network. The security architect for Company A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company
A internal network from those same ports. Which of the following can be employed to allow this?
Which of the following would be an indicator of a likel…
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
Which of the following BEST describes the type of threa…
An HR employee began having issues with a device becoming unresponsive after attempting to open an email attachment. When informed, the security analyst became suspicious of the situation, even though there was not any unusual behavior on the IDS or any alerts from the antivirus software. Which of the following BEST describes the type of threat in this situation?
Which of the following types of information should be c…
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)
Which of the following commands would a security analys…
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
Which of the following courses of action would ONLY ide…
An alert has been distributed throughout the information security community regarding a critical Apache vulnerability. Which of the following courses of action would ONLY identify the known vulnerability?