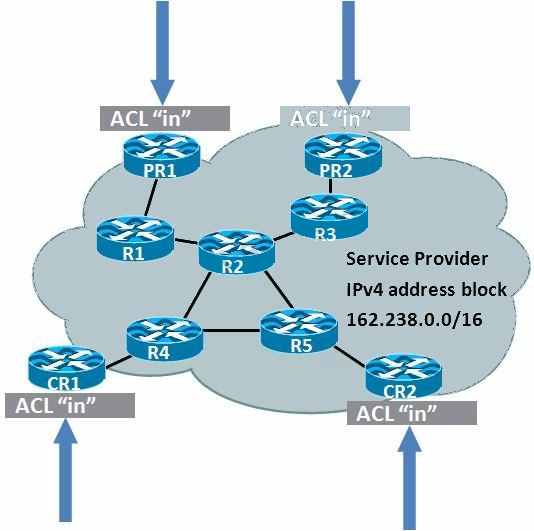
Inbound infrastructure ACLs are configured to protect the SP network. Which two types of traffic
should be permitted in the infrastructure ACL? (Choose two.)

A.
traffic destined for network of 172.30.0.0/16
B.
traffic source from network of 172.30.0.0/16
C.
traffic destined for network of 162.238.0.0/16
D.
traffic source from network of 162.238.0.0/16
E.
traffic destined for network of 232.16.0.0/16