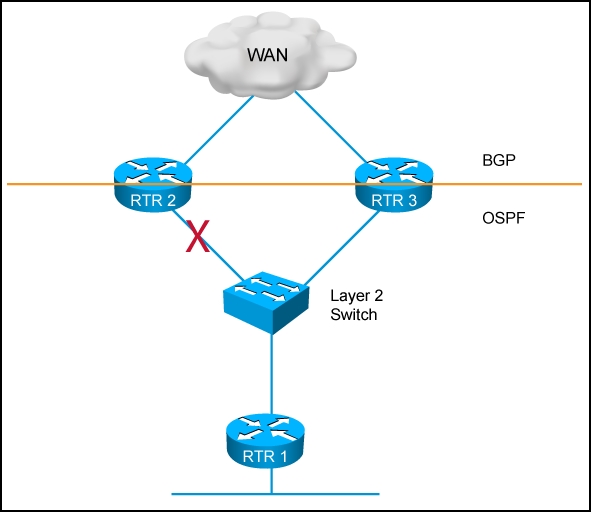
Refer to the exhibit.
RTR 1 uses RTR 2 as the primary WAN exit point. When a failure occurs in the link connected to
RTR 2 LAN, it takes about 40 seconds for RTR 1 to use the backup path via RTR 3. Which two
mechanisms can be used independently to improve the failure detection time to 1 second or
less when RTR 1 failover to RTR3? (Choose two.)

A.
Configure EEM on RTR 2.
B.
Change OSPF throttling timer.
C.
Use BFD with OSPF between RTR 1 and RTR 2.
D.
Use BFD with OSPF between RTR 2 and RTR 3.
E.
Tune OSPF fast hello on all the routers.


New questions:
QUESTION
What is a key role for the access layer in a hierarchical network design?
A. The access layer provides a security, QoS, and policy trust boundary.
B. The access layer provides an aggregation point for services and applications.
C. The access layer serves as a distribution point for services and applications.
D. The access layer can be used to aggregate remote users.
Answer: A
QUESTION
You have been asked to deploy BGP across a satellite link system to a small number of retail stores.
What must you do to successfully deploy BGP in this situation?
A. configure all the BGP peering sessions across the satellite links as EBGP
B. set the BGP hold timer to under one second
C. configure the initial window size, maximum MTU, and TCP keepalive parameters
D. manually configure static routes to back up BGP across the satellite link
Answer: C
QUESTION
Among the design criteria for a network is the requirement that bandwidth capacity be managed proactively. Which two techniques would most effectively support the proactive management of network bandwidth capacity? (Choose two.)
A. analyze network bandwidth utilization to establish a baseline
B. implement QoS to increase available bandwidth and overall throughput
C. implement utilization measurement and tracking measures in the network
D. configure SNMP MIB collectors to trigger at utilization thresholds
Answer: AC
QUESTION
What are the two preferred mechanisms for detecting Layer 2 link failures quickly? (Choose two.)
A. BFD
B. fast RSVP hellos
C. LDP keepalives
D. loss of signal
Answer: AD
QUESTION
Which IPv4 addressing and routing scheme can increase the availability of a network service during a DoS attack?
A. unicast
B. broadcast
C. anycast
D. multicast
Answer: C
QUESTION
Which network management tool should a network manager consult in order to pinpoint the cause of a routing recursion error?
A. debug (for BGP output)
B. syslog (for BGP errors)
C. RMON events group
D. SNMP routing traps
Answer: A
QUESTION
Which resource does a TCP SYN flood attack target?
A. connection tables on the target host
B. send buffers on transit routers
C. shared memory on the routers closest to the target
D. SYN cookies on the target host
Answer: A
0
0
More: https://drive.google.com/drive/folders/0B75b5xYLjSSNSUNBNi1aYkpfOTQ?usp=sharing
0
0