You have been asked to evaluate how EIGRP is functioning in a customer network.
Which key chain is being used for authentication of EIGRP adjacency between R4 and R2?

A.
CISCO
B.
EIGRP
C.
key
D.
MD5
Explanation:
R4 and R2 configs are as shown below:Clearly we see the actual key chain is named CISCO.



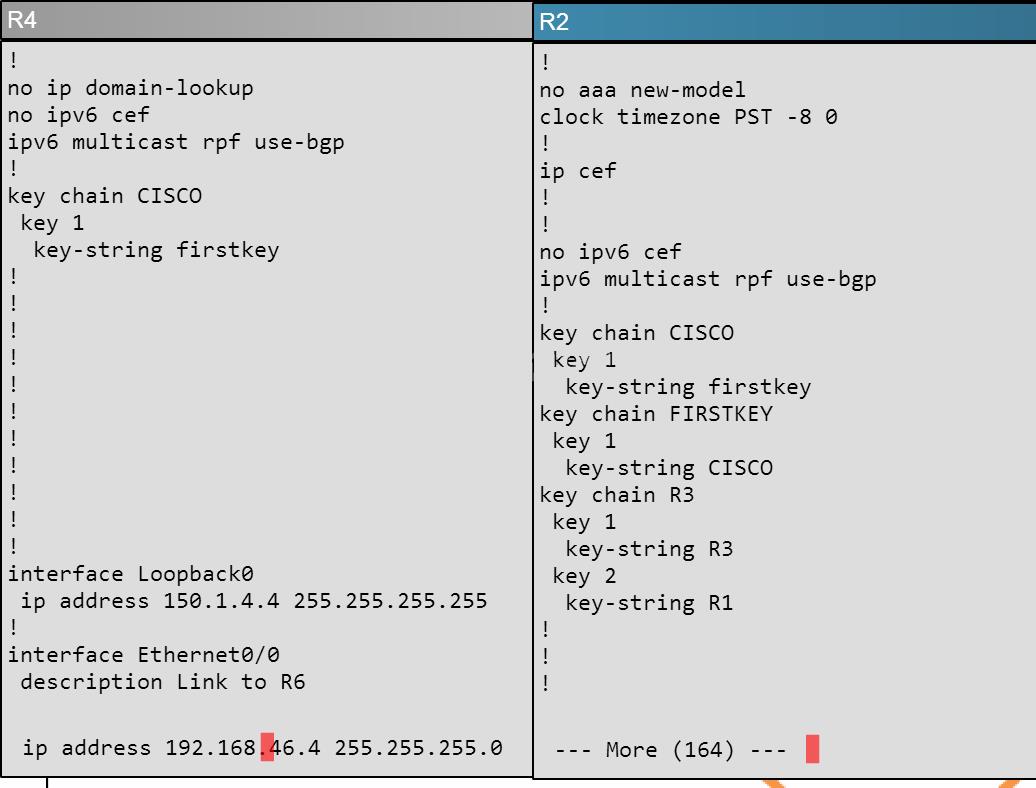
R4# show key chain
This command will show you if you don’t have access to “show run”
0
0