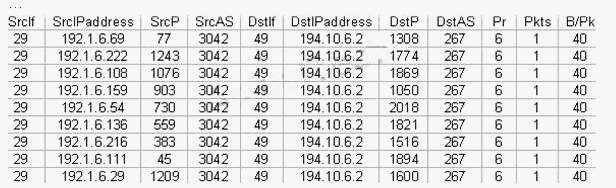
A network administrator issues the command “show ip cache flow” and finds the shown output.
What can be concluded? (Choose two.)

A.
It is normal traffic.
B.
There is a potential sacrificed host located at network 192.1.6.0 generating attacks.
C.
There is a potential DOS attack on device of 194.10.6.2.
D.
It is multicast traffic source from 194.10.6.2
E.
It is multicast traffic destined for 194.10.6.2