SIMULATION
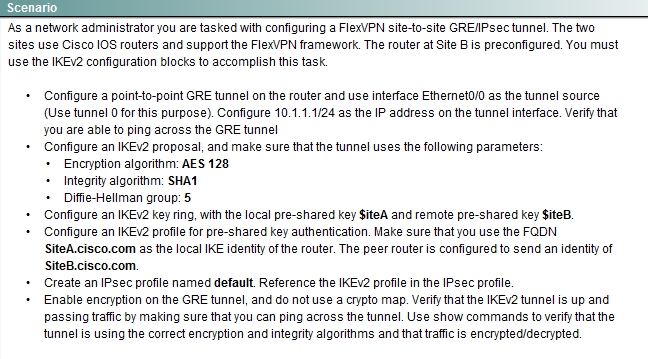
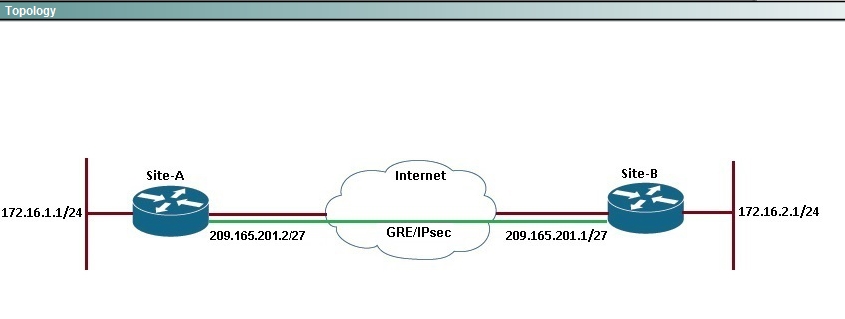
Configure a FlexVPN site-to-site GRE/IP sec tunnel.

Answer: See the explanation
Explanation:
Here are the steps as below:
Step 1: configure key ring
crypto ikev2 keyring mykeys
peer SiteB.cisco.com
address 209.161.201.1
pre-shared-key local $iteA
pre-shared key remote $iteB
Step 2: Configure IKEv2 profile
Crypto ikev2 profile default
identity local fqdn SiteA.cisco.com
Match identity remote fqdn SiteB.cisco.com
Authentication local pre-share
Authentication remote pre-share
Keyring local mykeys
Step 3: Create the GRE Tunnel and apply profile
crypto ipsec profile default
set ikev2-profile default
Interface tunnel 0
ip address 10.1.1.1 255.255.255.0
Tunnel source eth 0/0
Tunnel destination 209.165.201.1
tunnel protection ipsec profile default
end


The question is also asking for an IKEv2 proposal that is not shown with the current answer.
0
0
Missed Part:
crypto ikev2 proposal Propposal-2
encryption aes-cbc-128
integrity sha1
group 5
0
0
We need to add a ikev2 policy to call the proposal otherwise it’s using the default proposal.
R1#sh crypto ikev2 proposal
IKEv2 proposal: Propposal-2
Encryption : AES-CBC-128
Integrity : SHA96
PRF : SHA1
DH Group : DH_GROUP_1536_MODP/Group 5
IKEv2 proposal: default
Encryption : AES-CBC-256 AES-CBC-192 AES-CBC-128
Integrity : SHA512 SHA384 SHA256 SHA96 MD596
PRF : SHA512 SHA384 SHA256 SHA1 MD5
DH Group : DH_GROUP_1536_MODP/Group 5 DH_GROUP_1024_MODP/Group 2
crypto ikev2 policy test
proposal Propposal-2
I suggest don’t add the policy at first, at the end if they are using default proposal add the test policy to call the Propposal-2.
0
0
BTW, part of that new 307Q 300-209 dumps are available here:
https://drive.google.com/open?id=0B-ob6L_QjGLpVTNFVTRPdC0zTnM
Best Regards!
0
0