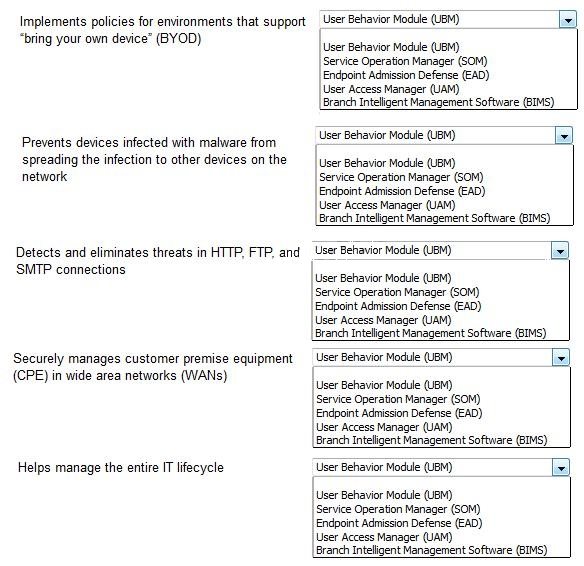
HOTSPOT
Match each IMC module to the correct description.

Answer: <a href=”//cdn.briefmenow.org/wp-content/uploads/hp0-y46/2.jpg”><img class=”aligncenter size-full” src=”//cdn.briefmenow.org/wp-content/uploads/hp0-y46/2.jpg” alt=”” /></a>
Explanation:
Implements policies for environments that support ‘bring your own device’ (BYOD) – User access
manager (UAM)
Prevents devices infected with malware from spreading the infection to other devices on the
network – Endpoint Admission Defense (EAD)
Detects and eliminates threats in HTTP, FTP, SMTP connections – User Behavior Module
Securely manages customer premise equipment (CPE) in wide area networks (WANs) – Branch
Intelligent Management Software (BIMS)
Helps manage the entire IT lifecycle – Service operation Manager (SOM)