Which statement accurately describes this vulnerability?
A company CEO hears about Hole 196 and is concerned that WPA/WPA2 will not protect the
company’s wireless communications from eavesdroppers.
Which statement accurately describes this vulnerability?
Which 802.11 frames can be sent at any supported rate (as opposed to the basic rate)?
Which 802.11 frames can be sent at any supported rate (as opposed to the basic rate)?
Which adjustment would cause the ACS to function more efficiently?
The MSM APs in an MSM solution are configured to use Automatic Channel Selection (ACS) on
their 2.4 GHz radios. Which adjustment would cause the ACS to function more efficiently?
Which EAP method requires the supplicant and the authentication server to mutually authenticate with digital c
Which EAP method requires the supplicant and the authentication server to mutually authenticate
with digital certificates?
What is the primary difference between AES-CCMP and TKIP?
What is the primary difference between AES-CCMP and TKIP?
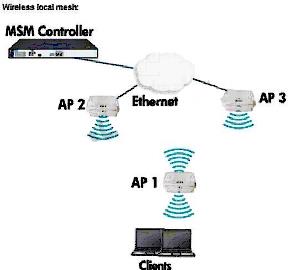
What are appropriate roles for the three APs?
Refer to the exhibit.
A network administrator needs to configure a dynamic wireless mesh to connect HP MSM AP 1 to
the network.
AP 1 will be installed outdoors where Ethernet is not available. It will connect to AP2ortoAP3; one
of which will provide the primary link and one of which will act as backup. Both AP 2 and AP 3
have connections to the Ethernet network and should not connect to each other.
What are appropriate roles for the three APs?
How will the MSM APs find the MSM Controller?
The MSM APs are deployed on a separate subnet from the controller and network administrators
want to set up Layer 3 DHCP discovery.
How will the MSM APs find the MSM Controller?
How should the network administrator configure authentication in the VSC?
A company has an HP MSM solution that consists of an HP MSM760 Controller and controlled HP
MSM APs. The solution supports a VSC that enforces HTML-based user login (Wet>-Auth) using
the controller’s internal login pages. The company wants users to see the login page, read a legal
agreement, and then click a button to receive free access. For this purpose, the company Web
designer customizes the appearance of the login page but does not alter the underlying code.
How should the network administrator configure authentication in the VSC?
Which 802.11n technology involves a radio transmitting the same data on more than one antenna’?
Which 802.11n technology involves a radio transmitting the same data on more than one
antenna’?
Which teaming solution meets the customer’s needs?
A customer has 600 APs and requires N+1 redundancy for the wireless services.
Which teaming solution meets the customer’s needs?