which stakeholder should the network architect discuss the technical detail of the legacy system and any chall
A network architect is working with a customer to implement a new network design. The network
architect has learned that the company has a legacy application hosted on a number of legacy
servers. The legacy application must remain intact and after the new network implementation. As
the company plans to continue using it indefinitely.
With which stakeholder should the network architect discuss the technical detail of the legacy
system and any challenges or specifics about maintaining interoperability?
What is most appropriate plan for oversubscription in the new access layer?
A customer is seeking an upgrade for their campus LAN network. Currently, the customer has
access layer switches that support 18.10/100/1000 Mbps ports and one Gigabit uplink. The
customer wants better performance in the upgrade but also wants to minimize costs.
The network architect has used the Network Traffic Analyzer (NTA) for Intelligent Management
Center (IMC) to collect information about the access layer uplinks. These are the results:
For switches on Floor1,the peak utilization is650 Mbpson a Gigabit uplink. Onmost days, the
utilizationpeaks at about 400 Mbps. Peaksusually occur briefly.
For switches on Floo2,the peak utilization is800Mbpson a Gigabit Uplink. Duringactiveperiods,
the utilization often remainnear 800.
What is most appropriate plan for oversubscription in the new access layer? (For this question,
think only about oversubscription and not customer needs for redundancy)
What should the architect suggest?
A customer requires high availability for wireless services at branches. The customer also wants to
centralize management and traffic distribution as much as possible. What should the architect
suggest?
Which security solution would help prevent this type of attack?
An employer takes the company laptops offsite and connects it to an insecure network. A hacker is
able to deploy a malware application to the laptop. The employer takes the laptop back to the
office, where the malware uses the credentials of the employee to eavesdrop and to implement
denial of service (DoS) attacks.
Which security solution would help prevent this type of attack?
what is the availability that this link currently provides?
A network architect is designing a redundancy solution for a customer and has learned that there
is a single link between two critical network components. During the past 4000 hours of operation,
the link has failed twice. The customer estimates that each failure has taken two hours to resolve.
Given this information, what is the availability that this link currently provides?
What is one reason for using two Hp Wired-WLAN controllers for this solution?
An architect is planning an HP Wired-WLAN solution for an office with approximately 4000 users
who will use the wireless network rather heavily and also need to roam seamlessly. The solution
will have 256 MSM 460 access points (APs). What is one reason for using two Hp Wired-WLAN
controllers for this solution?
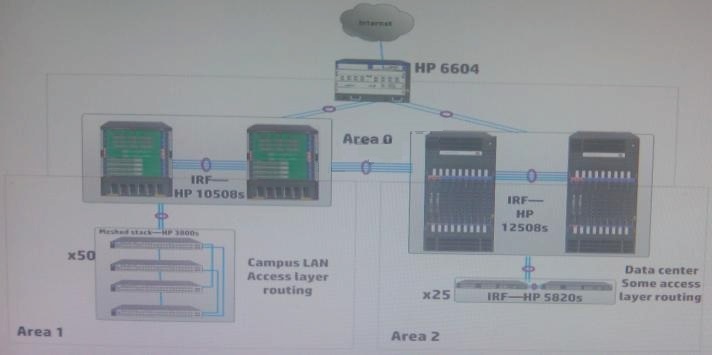
When would a network architect recommend an HP HSR6800 Router for a campus LAN?
When would a network architect recommend an HP HSR6800 Router for a campus LAN? (Select
two)
What is an appropriate method for the HP 6604 router to advertise routes to the internet to the other routing
A network architect is proposing an HP 6600 series router at the core of this enterprise customer
network. The router runs Border Gateway Protocol (BGP) and announces the customer networks
to the internet service provider (ISP). The router also runs Open Shortest Path First (OSPF) to
communicate with the rest of the customer network.
What is an appropriate method for the HP 6604 router to advertise routes to the internet to the
other routing switches?
Which factors affect the choice?
A network architect is choosing fabric module for an HP 10500 Series Switch. Which factors affect
the choice?