which level can the administrator set an alarm to notify the storage team?
A group of virtual machines has been deployed using thin disks because of limited storage
space availability. The storage team has expressed concern about extensive use of this
type of provisioning. At which level can the administrator set an alarm to notify the storage
team?
How can you verify that vStorage APIs for Array Integration (VAAI) functionality is enabled for a storage arra
How can you verify that vStorage APIs for Array Integration (VAAI) functionality is enabled
for a storage array in a vSphere 5.x implementation?
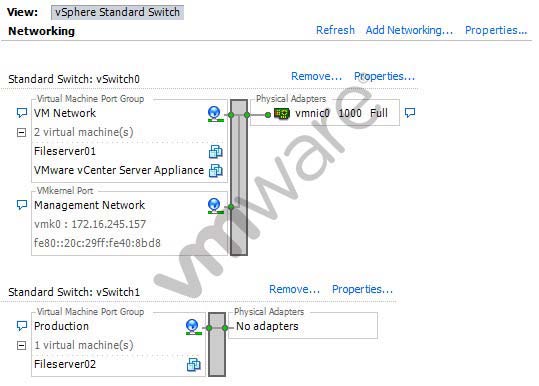
what step does the administrator need to take, assuming that vSwitch1 will still be needed for further configu
The vSphere administrator needs to remove the Production virtual
machine port group from an ESXi host. The ESXi host’s Networking Configuration tab is
shown in the exhibit. After disconnecting the Fileserver02 VM, what step does the
administrator need to take, assuming that vSwitch1 will still be needed for further
configuration?
what limit will be reached first?
When designing a storage infrastructure to support ESXi 5.x hosts what limit will be reached
first?
How can this information be retrieved?
An administrator needs to audit all of the events of the last 24 hours in the vCloud
infrastructure that is used across the company. How can this information be retrieved?
Which two statements are true about the inclusion of this driver in the image?
An administrator has purchased a new 10GB Converged Network Adapter (CNA) for
installation in a system that is running ESXi 5.x. The administrator has downloaded the
latest driver from the hardware vendor and wants to include the driver in an image. The
image profile acceptance level is set to VMwareSupported. The acceptance level of the
driver is VMwareSupported. Which two statements are true about the inclusion of this driver
in the image? (Choose two.)
Which is the most secure method of connecting to an iSCSI storage array using an independent hardware iSCSI ad
Which is the most secure method of connecting to an iSCSI storage array using an
independent hardware iSCSI adapter?
what are two valid states in which an administrator can place the uplinks?
A vSphere Standard Switch is configured with two uplinks. When adjusting the failover order
of the uplinks, what are two valid states in which an administrator can place the uplinks?
(Choose two.)
Which are the correct parameters to specify when adding an iSCSI target to an ESXi 5.x host using the Static D
Which are the correct parameters to specify when adding an iSCSI target to an ESXi 5.x
host using the Static Discovery tab?
What are the three service offerings provided by a VMware-powered public cloud?
What are the three service offerings provided by a VMware-powered public cloud? (Choose
three.)