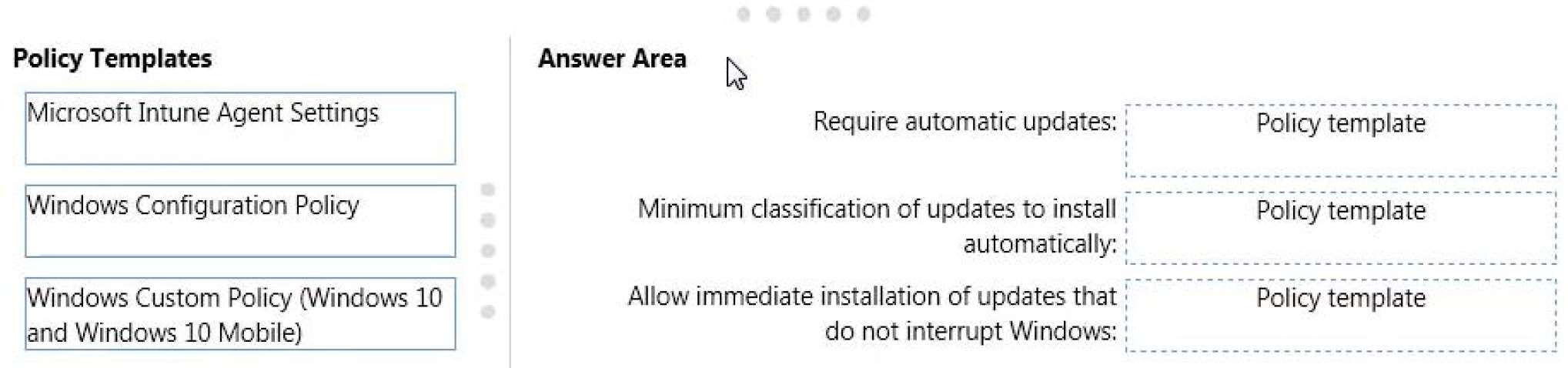
Which policy template should you use to configure each software updates setting?
You manage Microsoft Intune for a company named Contoso. You have 200 computers that run Windows 10.
The computers are Intune clients.
You need to configure software updates for the clients.
Which policy template should you use to configure each software updates setting? To answer, drag the
appropriate policy templates to the correct settings. Each policy template may be used once, more than once, or
not at all. You may need to drag the split bar between panes or scroll to view content.
You need to configure the user’s computer to prevent possible user data loss in the future
You support Windows 10 Enterprise computers that are members of an Active Directory domain. Recently,
several domain user accounts have been configured with super-mandatory user profiles.
A user reports that she has lost all of her personal data after a computer restart.
You need to configure the user’s computer to prevent possible user data loss in the future.
What should you do?
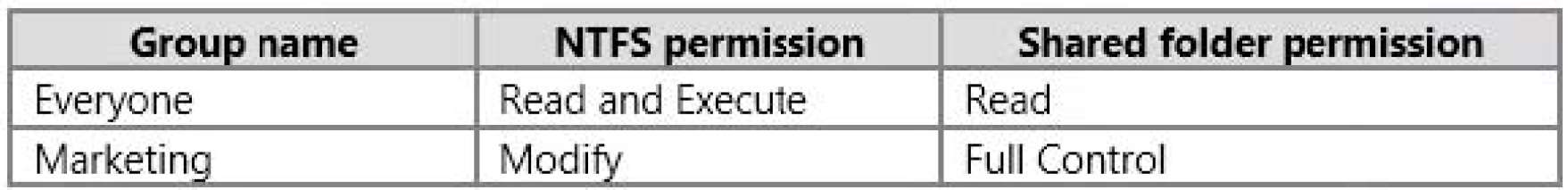
What permission should you identify?
You have a Windows 10 Enterprise computer.
The computer has a shared folder named C:\\Marketing. The shared folder is on an NTFS volume.
The current NTFS and share permissions are configured as follows.
UserA is a member of both the Everyone group and the Marketing group.
UserA must access C:\\Marketing from across the network. You need to identify the effective permissions of
UserA to the C:\\Marketing folder.
What permission should you identify?
Use the drop-down menus to select the answer choice that completes each statement…
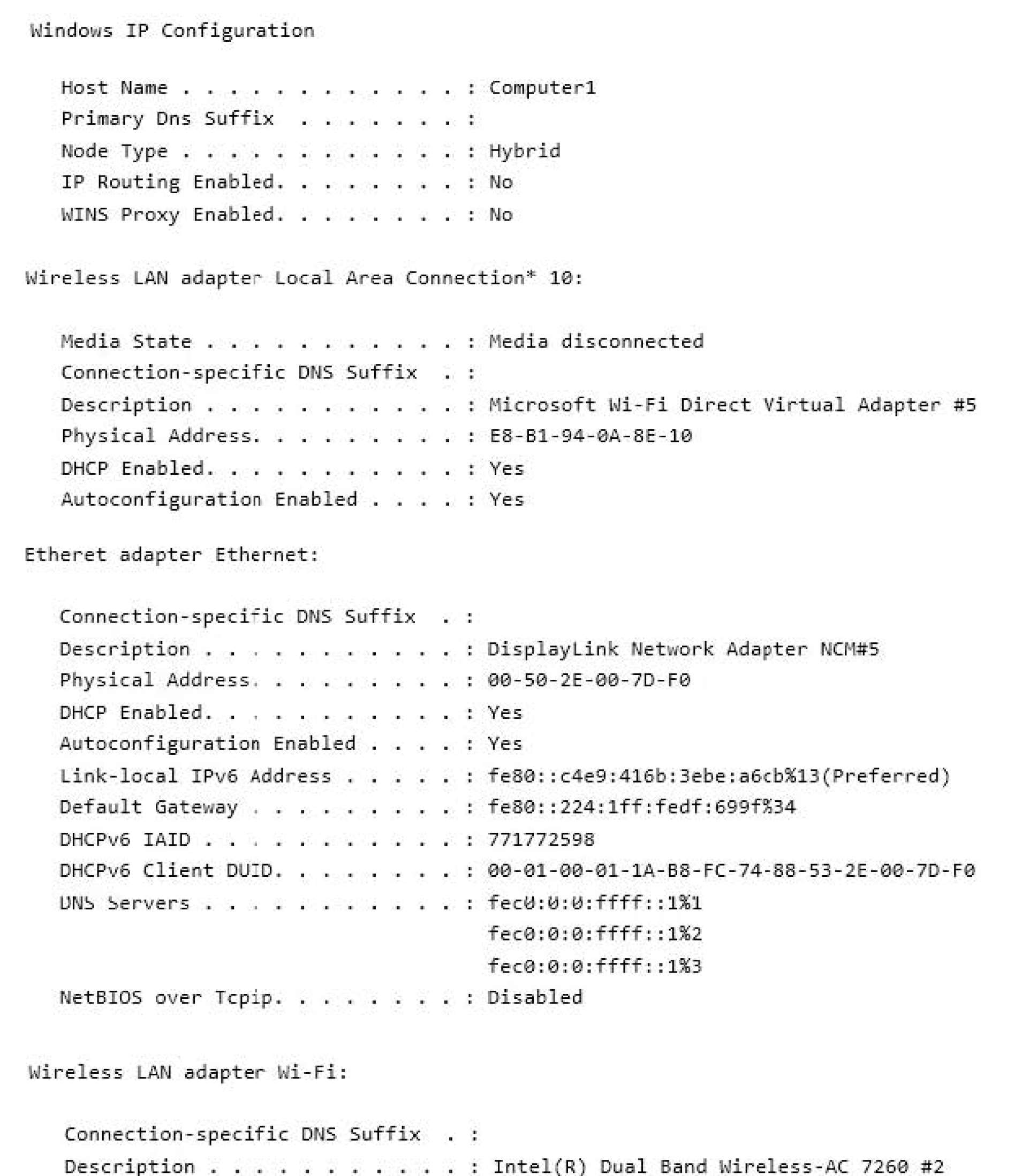
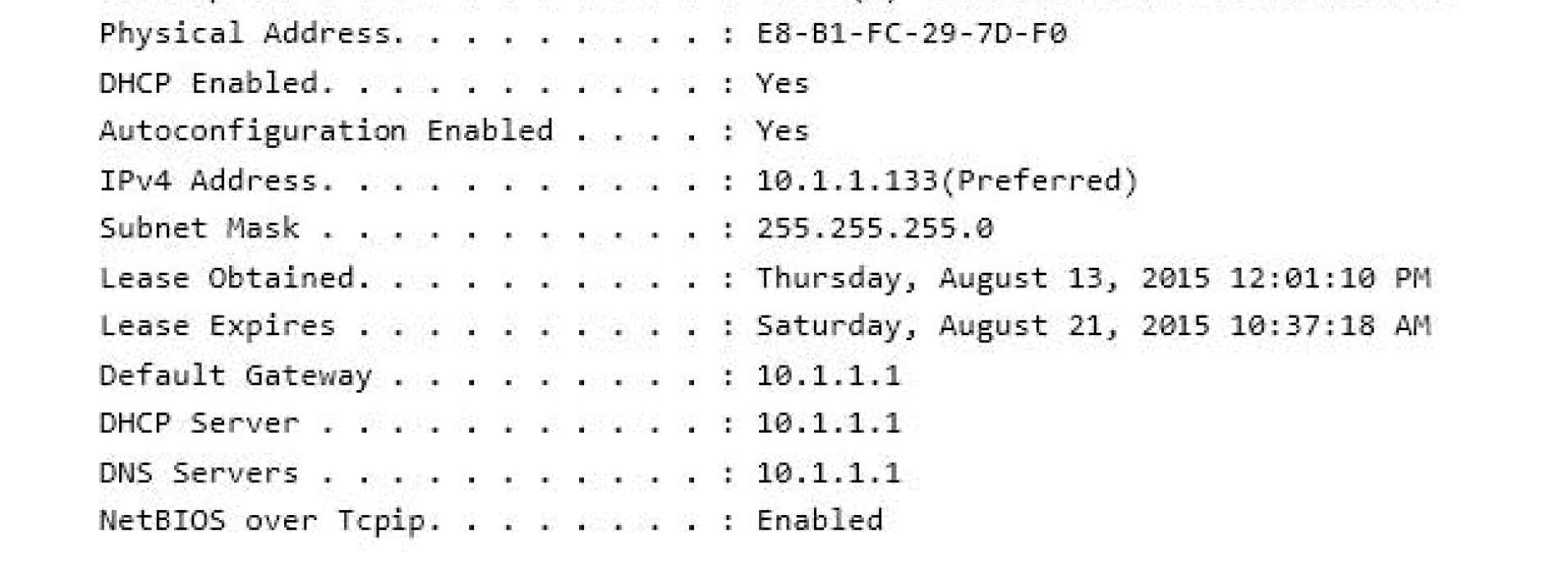
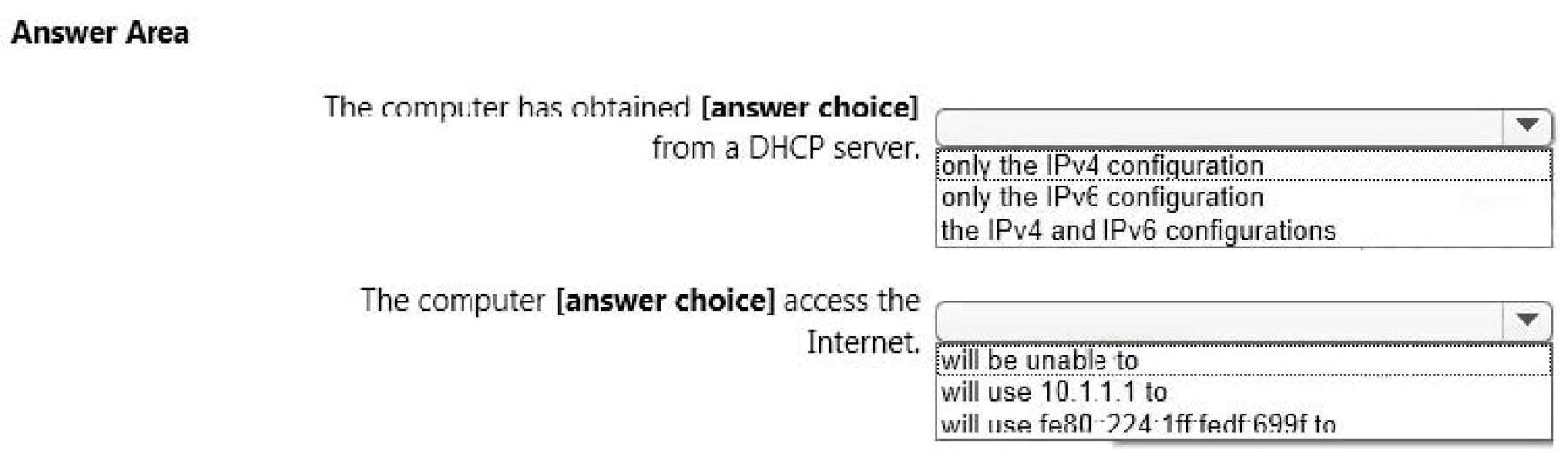
You have a network that contains Window 10 Enterprise computers.
The network configuration of one of the computers is shown in the following output.
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the output.
NOTE: Each correct selection is worth one point.
What should you include in the configuration file?
You plan to deploy a Microsoft Azure RemoteApp collection by using a custom template image. The image will
contain Microsoft Office 365 ProPlus apps.
You need to ensure that multiple users can run Office 365 ProPlus from the custom template image
simultaneously.
What should you include in the configuration file?
Which policy template should you use?
You manage Microsoft Intune for a company named Contoso. Intune client computers run
Windows 10 Enterprise.
You notice that there are 25 mandatory updates listed in the Intune administration console.
You need to prevent users from receiving prompts to restart Windows following the installation of mandatory
updates.
Which policy template should you use?
What should you identify?
You manage a Microsoft Azure RemoteApp deployment. The deployment consists of a cloud collection named
CloudCollection1 and a hybrid collection named HybridCollection1. Both collections reside in a subscription
named Subscription1. Subscription1 contains two Active Directory instances named AzureAD1 and AzureAD2.
AzureAD1 is the associated directory of Subcsription1.
AzureAD1 is synchronized to an on-premises Active Directory forest named constoso.com. Passwords are
synchronized between AzureAD1 and the on-premises Active Directory.
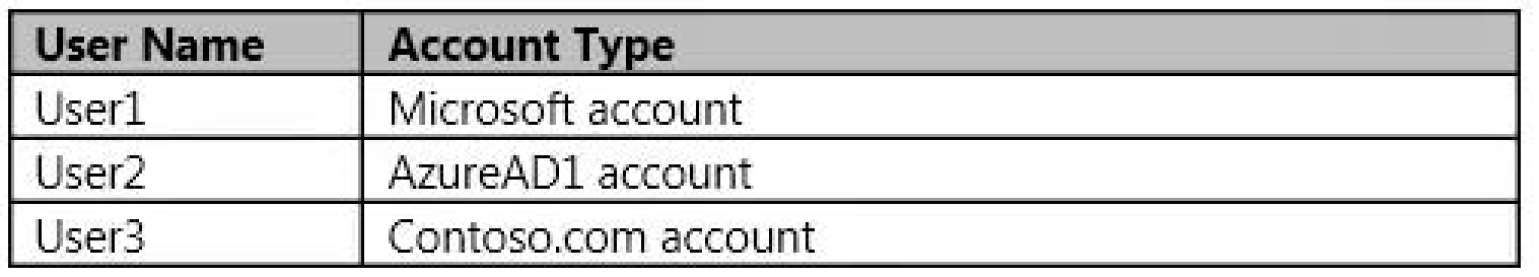
You have the following user accounts:
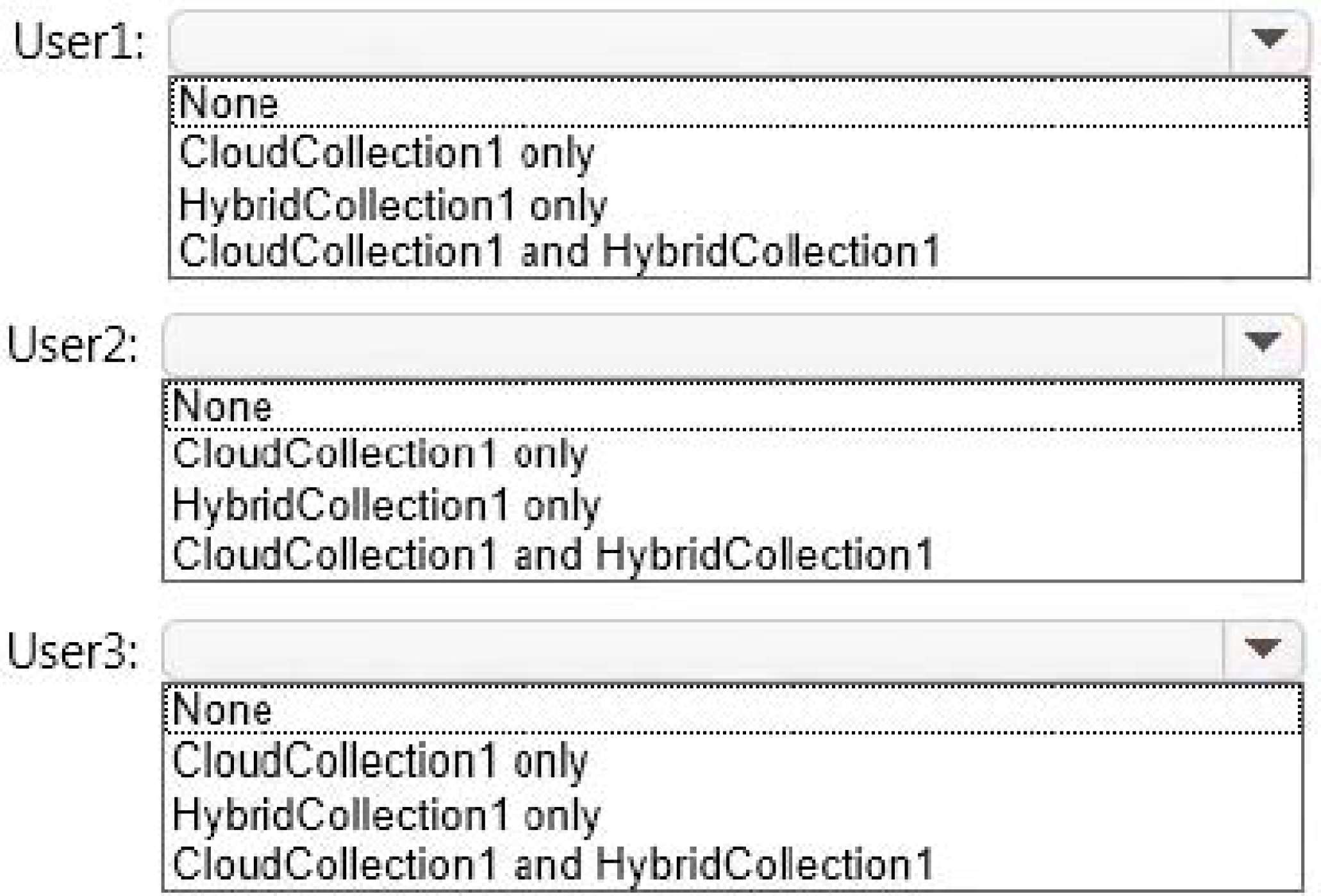
You need to identify to which collections each user can be assigned access.
What should you identify? To answer, select the appropriate options in the answer area.
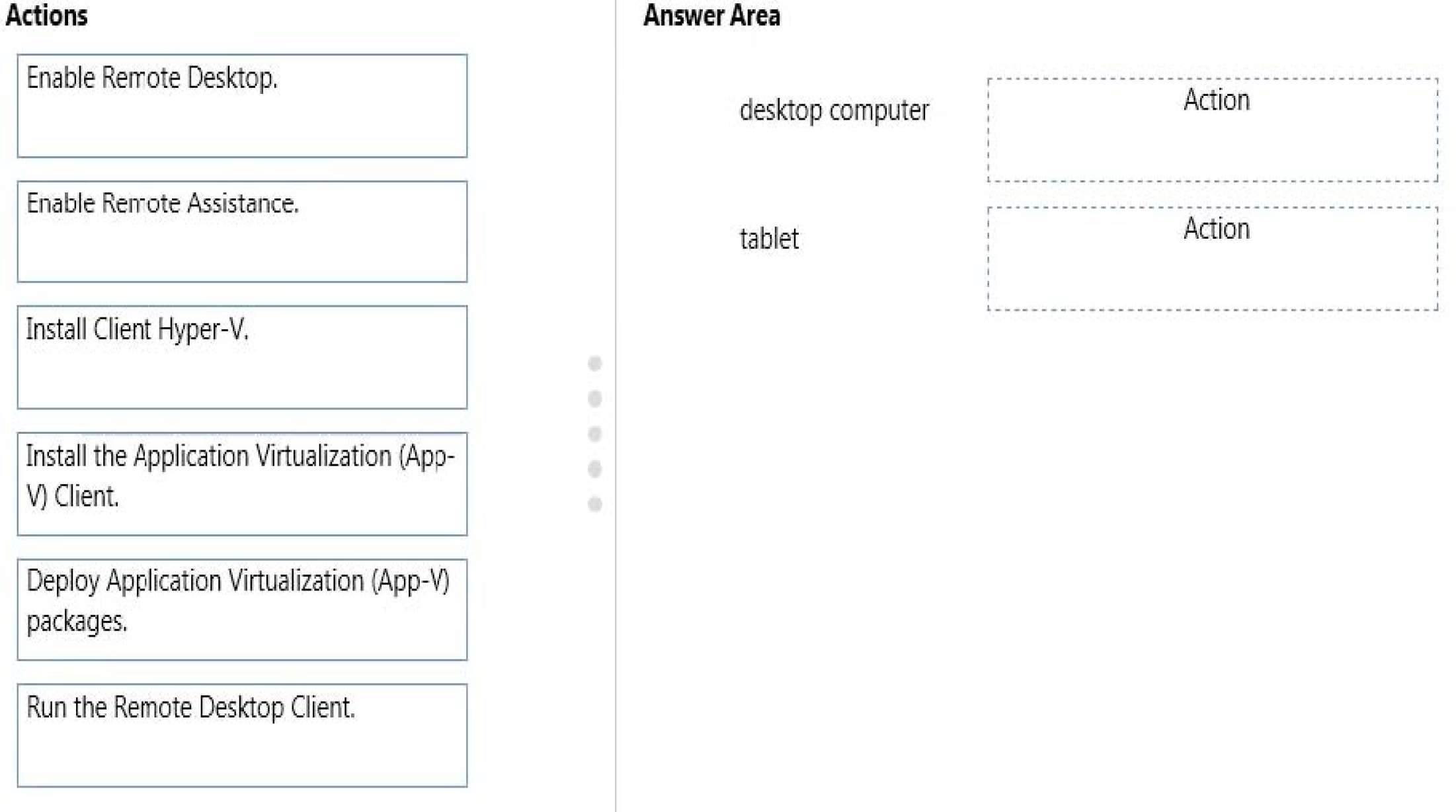
Which actions should you perform on each computer?
You have a desktop computer and a tablet that both run Windows 10 Enterprise.
The desktop computer is located at your workplace and is a member of an Active Directory domain.
The network contains an Application Virtualization (App-V) infrastructure. Several App-V applications are
deployed to all desktop computers.
The tablet is located at your home and is a member of a workgroup. Both locations have Internet connectivity.
You need to be able to access all applications that run on the desktop computer from you tablet.
Which actions should you perform on each computer? To answer, drag the appropriate action to the correct
computer.
Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes
or scroll to view content.
you need to remotely execute Windows PowerShell cmdlets on VM1
You have a Windows 10 Enterprise computer named Computer1 that has the Hyper-V feature installed.
Computer1 hosts a virtual machine named VM1.
VM1 runs Windows 10 Enterprise. VM1 connects to a private virtual network switch.
From Computer1, you need to remotely execute Windows PowerShell cmdlets on VM1.
What should you do?
Which two actions should you perform?
Employees are permitted to bring personally owned portable Windows 10 Enterprise computers to the office.
They are permitted to install corporate applications by using the management infrastructure agent and access
corporate email by using the Mail app.
An employee’s personally owned portable computer is stolen.
You need to protect the corporate applications and email messages on the computer.
Which two actions should you perform? Each correct answer presents part of the solution.