Which command should you include in the batch file?
You administer a company network that includes a wireless network infrastructure and computers that run
Windows 8 Enterprise.
You are planning to add a guest wireless network.
You need to collect information about nearby wireless networks, including their encryption methods.
Which command should you include in the batch file?
Which three actions should you perform in sequence?
DRAG DROP
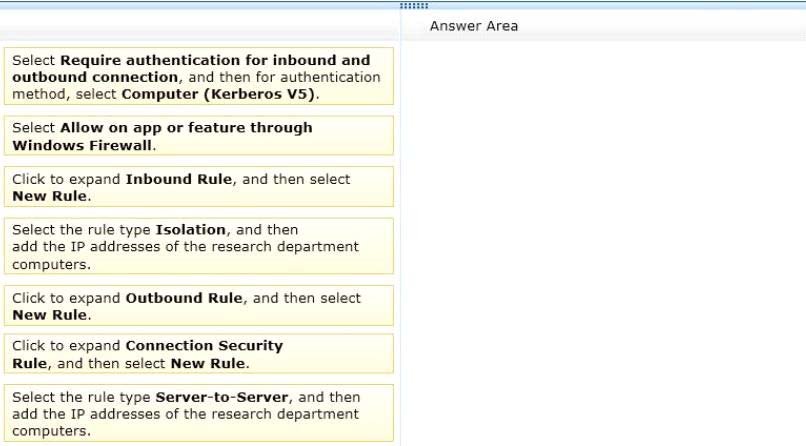
You administer desktop computers in your company’s research department. The computers run Windows 8
Enterprise and are members of a workgroup.
A new security policy states that all traffic between computers in the research department must be encrypted
and authenticated.
You need to configure the requested traffic authentication settings by using Windows Firewall with Advanced
Security.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list
of actions to the answer area and arrange them in the correct order.)
Which two actions should you perform?
You administer computers that run Windows 8 Enterprise and are members of an Active Directory domain.
Some volumes on the computers are encrypted with BitLOcker. The BitLocker recovery passwords are stored
in Active Directory. A user forgets the BitLocker password to local drive E: and is unable to access the
protected volume.
You need to provide a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Which two actions should you perform?
You have a desktop computer that runs Windows 8 Enterprise.
You add three new 3-terabyte disks.
You need to create a new 9-terabyte volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
You need to configure the network to support the required remote administration access
You support computers that run Windows 8 Pro and are members of an Active Directory domain. Several
desktop computers are located in a subnet that is protected by a firewall. The firewall allows incoming TCP
connections only to ports 80 and 443.
You want to manage disk volumes on the desktop computers from your computer, which is located outside the
protected subnet.
You need to configure the network to support the required remote administration access.
What should you do?
Which three actions should you perform in sequence?
DRAG DROP
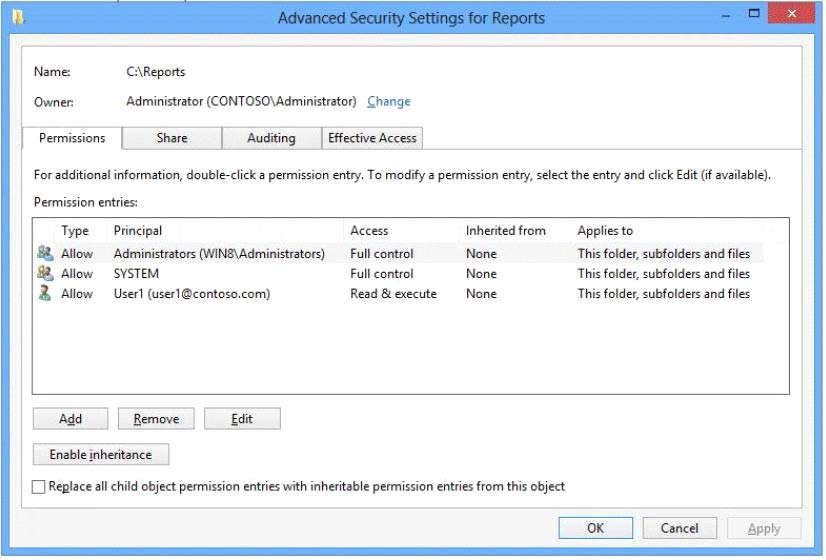
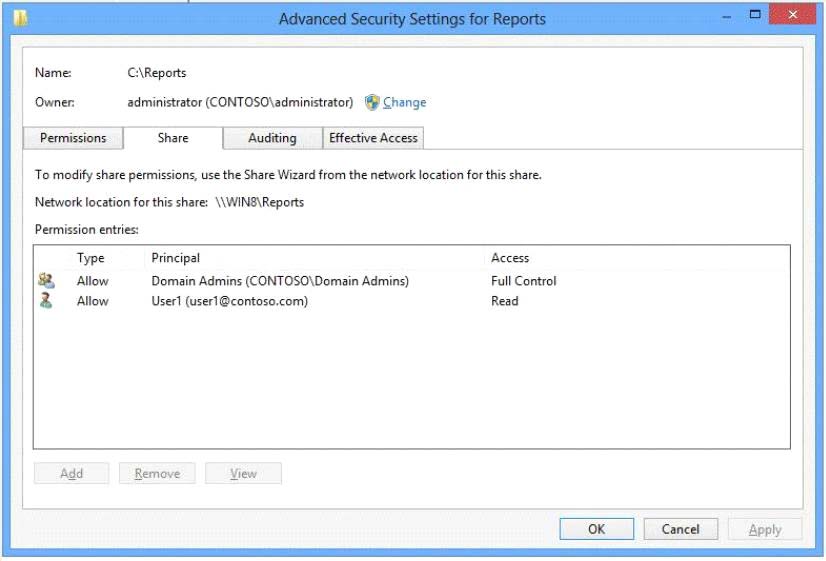
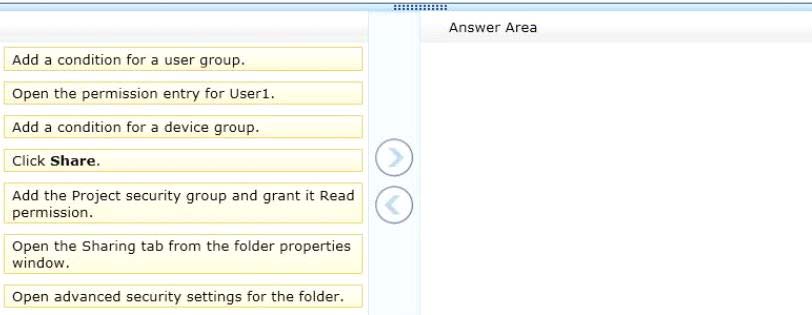
You administer a computer that runs Windows 8 Enterprise and is a member of an Active Directory domain.
You create a folder named C:\Reports and assign NTFS permissions as shown in Exhibit 1. (Click the Exhibit
button.)
You share the folder over the network with Read permission for a domain user account named User1 as shown
in Exhibit 2. (Click the Exhibit button.)
You want to provide access to the shared folder only for the time that User1 is a member of the domain
security group named Project.
You need to assign the required permissions.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list
of actions to the answer area and arrange them in the correct order.)
You need to reconfigure the new computer in order to access the HomeGroup resources
You are a systems administrator of a small branch office. Computers in the office are joined to a Windows 8
HomeGroup. The HomeGroup includes one shared printer and several shared folders.
You join a new computer to the HomeGroup and try to access the HomeGroup shared folders. You discover
that the shared folders are unavailable, and you receive an error message that indicates the password is
incorrect.
You need to reconfigure the new computer in order to access the HomeGroup resources.
What should you do?
Which three actions should you perform in sequence?
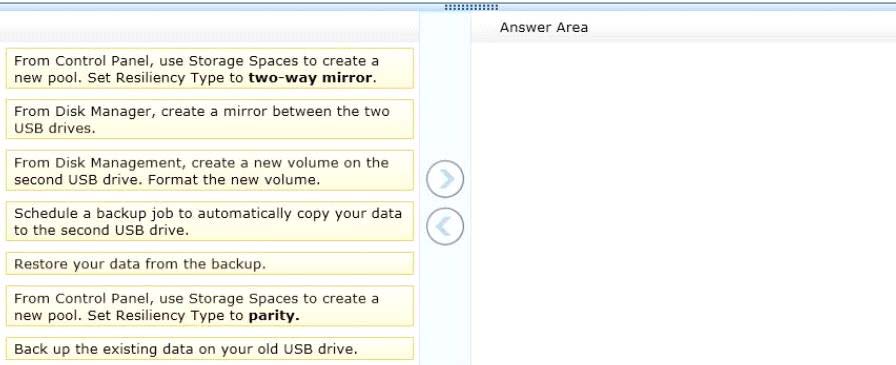
DRAG DROP
You have a computer that runs Windows 8. You have a 1-terabyte external hard drive. You purchase a second
1-terabyte external hard drive.
You need to create a fault-tolerant volume that includes both external hard drives. You also need to ensure
that additional external hard drives can be added to the volume.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list
of actions to the answer area and arrange them in the correct order.)
You need to recommend a solution that prevents this warning message from appearing, without compromising the s
You are a systems administrator for your company. The company has employees who work remotely by using
a virtual private network (VPN) connection from their computers, which run Windows 8 Pro.
These employees use an application to access the company intranet database servers. The company recently
decided to distribute the latest version of the application through using a public cloud.
Some users report that every time they try to download the application by using Internet Explorer, they
receive a warning message that indicates the application could harm their computer.
You need to recommend a solution that prevents this warning message from appearing, without
compromising the security protection of the computers.
What should you do?
Which four actions should you perform in sequence?
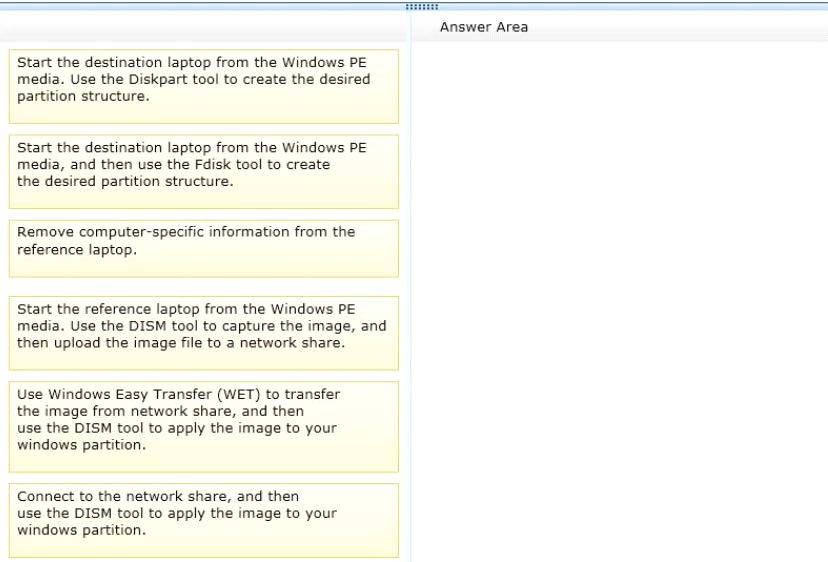
DRAG DROP
Your company recently purchased 25 new laptops. All 25 laptops have the same hardware configuration and
do not have any operating system installed.
You have been asked to deploy Windows 8 on these laptops. You have installed and configured Windows 8 on
a reference laptop.
You need to create an image and deploy it to the 25 new laptops.
Which four actions should you perform in sequence? (To answer, move the appropriate actions from the list of
actions to the answer area and arrange them in the correct order.)