Which two actions should you perform?
Your company’s network is shown in the exhibit. (Refer to the Exhibit.)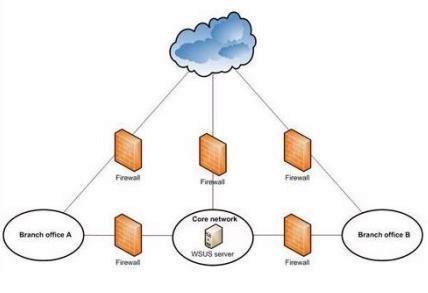
Each office is connected to the Internet through a high-bandwidth connection. The branch offices are
connected to the core network through low-bandwidthconnections.
Microsoft Windows Server Update Services (WSUS) must provide software updates for all offices.
You need to design the WSUS infrastructure to minimize traffic over the low-bandwidth connections.
Which two actions should you perform? (Each correctanswer presents part of the solution. Choose two.)
You need to plan a client computer licensing strategy that meets the requirements
Your network is configured as shown in the exhibit.(Refer to the Exhibit.)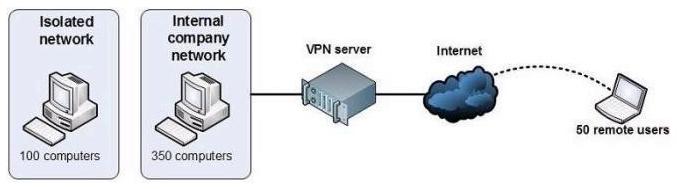
You are planning to deploy Windows 7.
You have the following requirements:
Use BitLocker on all computers in the isolated network.
Provide DirectAccess on all portable computers.
Use the Key Management Service (KMS) to activate all client computers.
You need to plan a client computer licensing strategy that meets the requirements.
What should you do?
You need to distribute a Microsoft Enterprise Desktop Virtualization (MED-V) virtual machine (VM) image that i
Your company has 1,000 client computers that run Windows 7. The company uses several custom line-of-business applications that are not compatible with Windows 7.
You need to distribute a Microsoft Enterprise Desktop Virtualization (MED-V) virtual machine (VM) image that
includes the custom applications to all Windows 7 client computers.
What should you do?
You need to ensure that the virtual machine (VM) images that contain sensitive data can be used only when the
Your company plans to upgrade all client computers to Windows 7.
The company uses a custom line-of-business application. The application contains sensitive data. The
application will not run on Windows 7
You establish that Microsoft Enterprise Desktop Virtualization (MED-V) is the appropriate technology to allow
your organization to continue to use the application.
You need to ensure that the virtual machine (VM) images that contain sensitive data can be used only when the
user is connected to the MED-V server.
What should you do?
You need to ensure that the application runs on theWindows XP client computers and that the Windows 7 client c
The client computers in your network run either Windows XP or Windows 7. All client computers are in asingle
Active Directory Domain Services (AD DS) organizational unit (OU) named MyClients.
You install Windows Software Update Services (WSUS). You create a Group Policy object (GPO) that enables
automatic updates from the WSUS server, and you link the GPO to the MyClients OU.
You place all client computers in a targeting groupnamed MyClients.
Testing reveals that a security update that is applicable to both Windows XP and Windows 7 causes a line-of-business application to fail on the Windows XP client computers.
You need to ensure that the application runs on theWindows XP client computers and that the Windows 7
client computers receive the security update.
What should you do?
You need to manage the software update process to meet the requirements
Your company uses Microsoft Windows Server Update Services (WSUS) to deploy software updates and
service packs. Microsoft releases a security updatefor Windows 7.
You have the following requirements:
The security update must be deployed by 5:00 P.M. on Friday.
Computers that are off when the security update is deployed must install the security update as soon as
they are turned on.
You need to manage the software update process to meet the requirements.
What should you do?
Which two actions should you perform?
Your company has a single Active Directory Domain Services (AD DS) domain named contoso.com that uses
Active Directory integrated DNS.
You deploy the Key Management Service (KMS) on a Windows 7 computer.
You need to ensure that Windows 7 client computers can locate the KMS host and perform activation.
Which two actions should you perform? (Each correctanswer presents part of the solution. Choose two.)
What should you include in the recommendations?
Your network contains 5 servers that have the Remote Desktop Session Host role service installed. The
servers host a Remote Desktop RemoteApp named App1.
You need to recommend a solution for App1 that meets the following requirements:
Must ensure that users can connect to any Remote Desktop Session Host server.
Must ensure that users are automatically reconnected to disconnected sessions.
What should you include in the recommendations?
You need to manage activation for client computers that are located in the high-security network segment
Your company has two network segments. The core network segment is where centralized management is
performed. The high-security network segment is an isolated network. A firewall between the core network
segment and the high-security network segment limits network communication between the segments.
These network segments are shown in the exhibit. (Refer to the Exhibit.)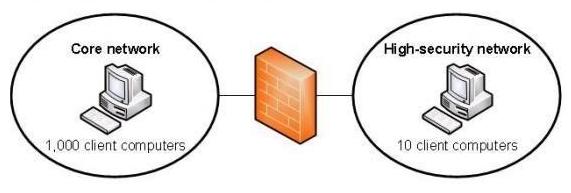
Your company plans to deploy Windows 7 to all client computers.
You need to manage activation for client computers that are located in the high-security network segment.
What should you do?
What are two possible ways to achieve this goal?
Your company has client computers that run Windows XP Professional.
You are planning to install Windows 7 Enterprise onthe existing client computers.
You need to ensure that the user state can be viewed after it has been collected and saved.
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose
two.)

