Which type of trust policy should you create?
Your network contains an Active Directory forest named adatum.com.
The forest contains an Active Directory Rights Management Services (AD RMS) cluster.
A partner company has an Active Directory forest named litwareinc.com.
The partner company does not have AD RMS deployed.
You need to ensure that users in litwareinc.com can consume rights-protected content from adatum.com.
Which type of trust policy should you create?
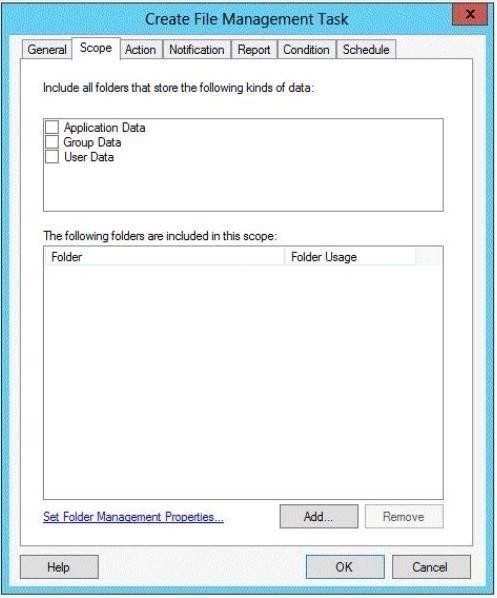
You need to ensure that the Include all folders that st…
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the File Server Resource Manager role service installed.
You are creating a file management task as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that the Include all folders that store the following kinds of data list displays an entry named Corporate Data.
What should you do?
What should you identify?
Your network contains a perimeter network and an internal network.
The internal network contains an Active Directory Federation Services (AD FS) 2.1 infrastructure.
The infrastructure uses Active Directory as the attribute store.
You plan to deploy a federation server proxy to a server named Server2 in the perimeter network.
You need to identify which value must be included in the certificate that is deployed to Server2.
What should you identify?
What should you identify?
Your network contains a perimeter network and an internal network.
The internal network contains an Active Directory Federation Services (AD FS) 2.1 infrastructure.
The infrastructure uses Active Directory as the attribute store.
You plan to deploy a federation server proxy to a server named Server2 in the perimeter network.
You need to identify which value must be included in the certificate that is deployed to Server2.
What should you identify?
Which command should you run?
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named File1 that runs a Server Core Installation of Windows Server 2012 R2.
File1 has a volume named D that contains home folders. File1 creates a shadow copy of volume D twice a day.
You discover that volume D is almost full.
You add a new volume named H to File1.
You need to ensure that the shadow copies of volume D are stored on volume H.
Which command should you run?
You need to ensure that the virtual machines on Server1…
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Server1 is a file server that has the Hyper-V server role installed. Server1 hosts several virtual machines.
The virtual machine configuration files are stored on drive D and the VHD files are stored on drive E.
You plan to replace drive E with a larger volume. You need to ensure that the virtual machines on Server1 remain available while drive E is being replaced.
What should you do?
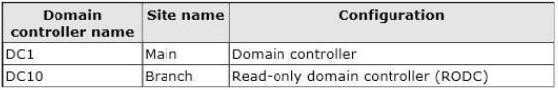
You need to identify which domain controller authentica…
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2. The domain contains two domain controllers.
The domain controllers are configured as shown in the following table.
The Branch site contains a member server named Server1 that runs Windows Server 2012 R2.
You need to identify which domain controller authenticated the computer account of Server1.
What should you do?
Which Windows PowerShell cmdlets should you run on each…
You have 30 servers that run Windows Server 2012 R2.
All of the servers are backed up daily by using Windows Azure Online Backup.
You need to perform an immediate backup of all the servers to Windows Azure Online Backup.
Which Windows PowerShell cmdlets should you run on each server?
Which Windows PowerShell cmdlets should you run on each…
You have 30 servers that run Windows Server 2012 R2.
All of the servers are backed up daily by using Windows Azure Online Backup.
You need to perform an immediate backup of all the servers to Windows Azure Online Backup.
Which Windows PowerShell cmdlets should you run on each server?
Which tool should you use?
Your company recently deployed a new Active Directory forest named contoso.com.
The forest contains two Active Directory sites named Site1 and Site2.
The first domain controller in the forest runs Windows Server 2012 R2.
You need to force the replication of the SYSVOL folder from Site1 to Site2.
Which tool should you use?