Which cmdlets should you use to meet each requirement?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain
contains servers named Server1 and Server2. Both servers have the DFS Replication role
service installed.
You need to configure the DFS Replication environment to meet the following requirements:
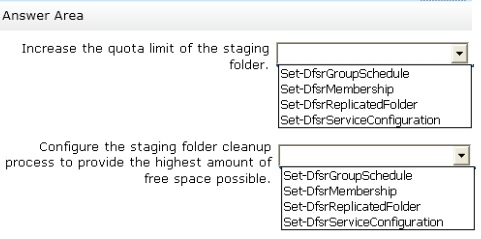
Increase the quota limit of the staging folder.
Configure the staging folder cleanup process to provide the highest amount of free space
possible.
Which cmdlets should you use to meet each requirement?
To answer, select the appropriate options in the answer area.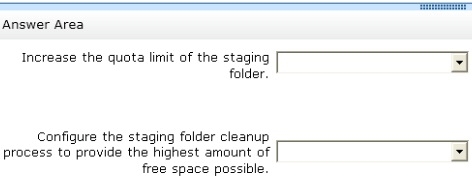
What should you install on Server2?
Your network contains an Active Directory domain named contoso.com. The domain
contains a file server named Server1 that runs Windows Server 2012 R2. Server1 has a
share named Share1.
When users without permission to Share1 attempt to access the share, they receive the
Access Denied message as shown in the exhibit. (Click the Exhibit button.)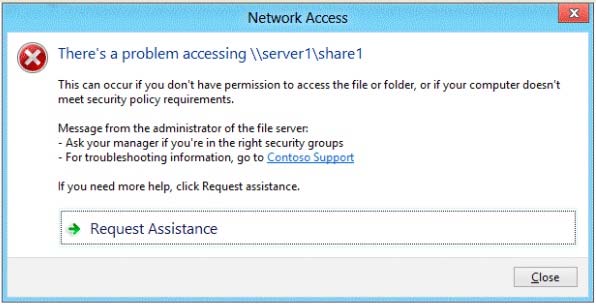
You deploy a new file server named Server2 that runs Windows Server 2012 R2.
You need to configure Server2 to display the same custom Access Denied message as
Server1.
What should you install on Server2?
You need to ensure that when a user receives an access-denied message while attempting to access Folder1, an e
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File
Server Resource Manager role service installed.
Each time a user receives an access-denied message after attempting to access a folder on
Server1, an email notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS
permissions for Folder1.
You need to ensure that when a user receives an access-denied message while attempting
to access Folder1, an email notification is sent to a distribution list named DL2. The solution
must not prevent DL1 from receiving notifications about other access-denied messages.
What should you do?
Which two nodes should you configure?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the File
Server Resource Manager role service installed.
You need to configure Server1 to meet the following requirements:
Ensure that old files in a folder named Folder1 are archived automatically to a folder named Archive1.
Ensure that all storage reports are saved to a network share.
Which two nodes should you configure?
To answer, select the appropriate two nodes in the answer area.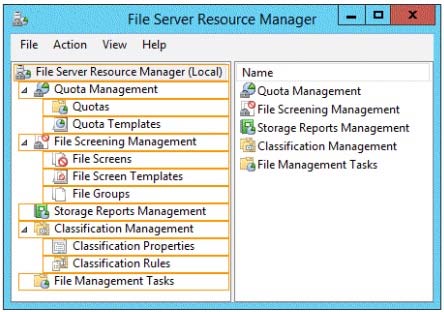
You need to identify the setspn.exe command that you must run to configure the appropriate Service Principal N
DRAG DROP
You are a network administrator of an Active Directory domain named contoso.com.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Web
Server (IIS) server role installed.
Server1 will host a web site at URL https: //secure.contoso.com. The application pool identity
account of the web site will be set to a domain user account named AppPool1.
You need to identify the setspn.exe command that you must run to configure the appropriate
Service Principal Name (SPN) for the web site.
What should you run?
To answer, drag the appropriate objects to the correct location. Each object may be used
once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.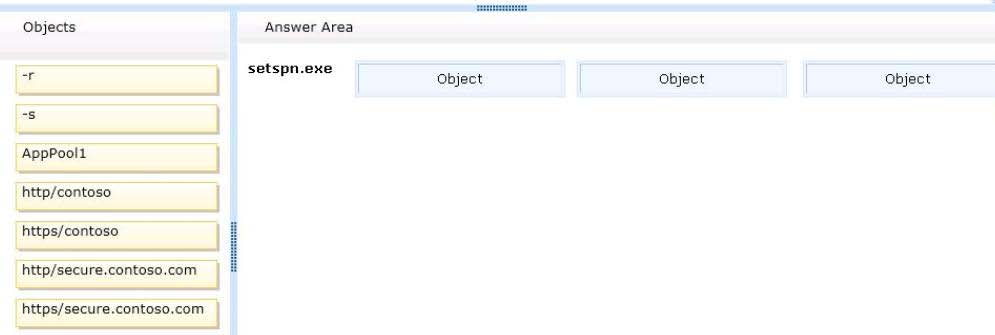
You need to identify the names of the users who were members of Group1 prior to its deletion
Your network contains an Active Directory domain named contoso.com. The domain
contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 is backed
up daily.
The domain has the Active Directory Recycle Bin enabled.
During routine maintenance, you delete 500 inactive user accounts and 100 inactive groups.
One of the deleted groups is named Group1. Some of the deleted user accounts are
members of some of the deleted groups.
For documentation purposes, you must provide a list of the members of Group1 before the
group was deleted.
You need to identify the names of the users who were members of Group1 prior to its
deletion.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you do first?
Which FSMO role should you transfer to DC2?
Your network contains an Active Directory domain named contoso.com. The domain
contains six domain controllers. The domain controllers are configured as shown in the
following table.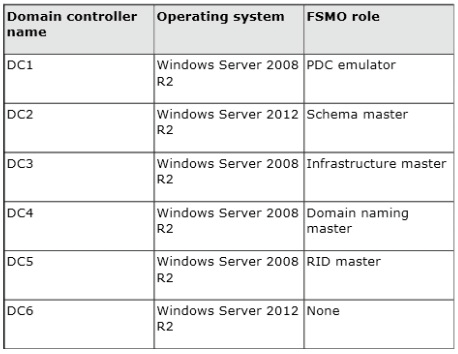
The network contains a server named Server1 that has the Hyper-v server role installed.
DC6 is a virtual machine that is hosted on Server1.
You need to ensure that you can clone DC6.
Which FSMO role should you transfer to DC2?
You need to ensure that you can create PSOs from Active Directory Administrative Center
Your network contains an Active Directory domain named contoso.com. All domain
controllers run either Windows Server 2008 or Windows Server 2008 R2.
You deploy a new domain controller named DC1 that runs Windows Server 2012 R2.
You log on to DC1 by using an account that is a member of the Domain Admins group.
You discover that you cannot create Password Settings objects (PSOs) by using Active
Directory Administrative Center.
You need to ensure that you can create PSOs from Active Directory Administrative Center.
What should you do?
What should you tell User1?
Your network contains an Active Directory forest named contoso.com. The functional level of
the forest is Windows Server 2008 R2.
All of the user accounts in the marketing department are members of a group named
Contoso\MarketingUsers. All of the computer accounts in the marketing department are
members of a group named Contoso\MarketingComputers.
A domain user named User1 is a member of the Contoso\MarketingUsers group. A
computer named Computer1 is a member of the Contoso\MarketingComputers group.
You have five Password Settings objects (PSOs). The PSOs are defined as shown in the
following table.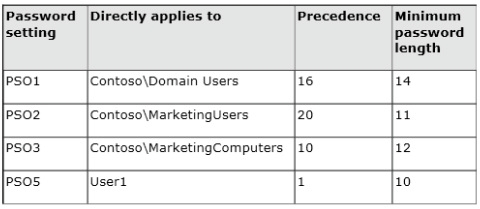
When User1 logs on to Computer1 and attempts to change her password, she receives an
error message indicating that her password is too short.
You need to tell User1 what her minimum password length is.
What should you tell User1?
Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The Active Directory
Recycle bin is enabled for contoso.com.
A support technician accidentally deletes a user account named User1. You need to restore
the User1 account.
Which tool should you use?

