Which tool should you use?
Note: This question is part of a series of questions that use the same similar answer choices.
An answer choice may be correct for more than one question in the series. Each question
is independent of the other questions in this series. Information and details provided in a
question apply only to that question.
You have a Hyper-V host named Server1 that runs Windows Server 2016 and a two-node scaleout file server cluster named Cluster1. A virtual machine named VM1 runs on Server1. You need
to migrate the storage on VM1 to Cluster1. Which tool should you use?
Which command should you run?
Note: This question is part of a series of questions that use the same scenario. For your
convenience, the scenario is repeated in each question. Each question presents a different
goal and answer choices, but the text of the scenario is exactly the same in each question
in this series.
Start of Repeated Scenario:
A company named Contoso, ltd. has several servers that run Windows Server 2016. Contoso has
a Hyper V environment that uses failover clustering and Windows Server Update Services (WSUS).
The environment contains several Windows containers and several virtual machines. The WSUS
deployment contains one upstream server that is located on the company’s perimeter network and
several downstream servers located on the internal network. A firewall separates the upstream
server from the downstream servers. You plan to deploy a human resources application to a new
server named HRServer5. HRServer5 contains a FAT32-formatted data volume. The CIO of
Contoso identifies the following requirements for the company’s IT department:
– Deploy failover cluster to two new virtual machines.
– Store all application databases by using Encrypted File System (EFS).
– Ensure that each Windows container has a dedicated IP address assigned
by a DHCP server.
– Produce a report that lists the processor time used by all of the
processes on a server named Server 1 for five hour.
– Encrypt all communication between the internal network and the perimeter
network, including all WSUS communications.
– Automatically load balance the virtual machines hosted in the Hyper-V
cluster when processor utilization exceeds 70 percent.
End of Repeated Scenario.
You need to modify the Hyper V cluster to meet the load balancing requirement for the virtual
machine. Which command should you run?
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution. After you answer a question in this section, you will NOT be able to return
to it. As a result, these questions will not appear in the review screen.
You have two servers that run Windows Server 2016. You plan to create a Network Load Balancing
(NLB) cluster that will contain both servers. You need to configure the network cards on the servers
for the planned NLB configuration.
Solution: You configure the network cards to be on the same subnet and to have static IP addresses.
You configure the cluster to use multicast.
Does this meet the goal?
Does this meet the goal?
In this section, you’ll see one or more sets of questions with the same scenario and problem.
Each question presents a unique solution to the problem, and you must determine whether
the solution meets the stated goals. Any of the solutions might solve the problem. It is also
possible that none of the solutions solve the problem.
Once you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution. Determine whether the solution meets the
stated goals.
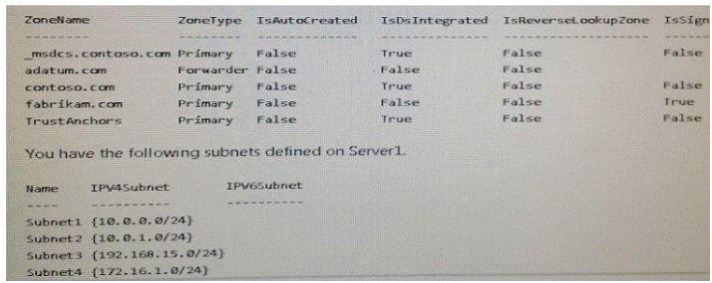
Your network contains an Active Directory domain named contoso.com. The domain contains a
DNS server named Server1. All client computers run Windows 10. On Server1, you have the
following zone configuration:
You need to prevent Server1 from resolving queries from DNS clients located on Subnet4. Server1
must resolve queries from all other DNS clients.
Solution: From the Security setting of each zone on Server1, you modify the permissions.
Does this meet the goal?
Does this meet the goal?
In this section, you’ll see one or more sets of questions with the same scenario and problem.
Each question presents a unique solution to the problem, and you must determine whether
the solution meets the stated goals. Any of the solutions might solve the problem. It is also
possible that none of the solutions solve the problem.
Once you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution. Determine whether the solution meets the
stated goals.
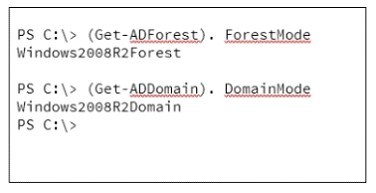
Your network contains an Active Directory forest named contoso.com. The forest contains a
member server named Server1 that runs Windows Server 2016. All domain controllers run
Windows Server 2012 R2. Contoso.com has the following configuration:
You plan to deploy an Active Directory Federation Services (AD FS) farm on Served and to
configure device registration. You need to configure Active Directory to support the planned
deployment.
Solution: You upgrade a domain controller to Windows Server 2016.
Does this meet the goal?
Which two inbound TCP ports should you open on the firewall?
Your network contains an Active Directory forest named contoso.com. The forest contains a
member server named Server1 that runs Windows Server 2016. Server1 is located in the perimeter
network. You install the Active Directory Federation Services server role on Server1. You create
an Active Directory Federation Services (ADFS) farm by using a certificate that has a subject name
of sts.contoso com. You need to enable certificate authentication from the Internet on Server1.
Which two inbound TCP ports should you open on the firewall? Each correct answer presents part
of the solution.
Does this meet the goal?
In this section, you’ll see one or more sets of questions with the same scenario and problem.
Each question presents a unique solution to the problem, and you must determine whether
the solution meets the stated goals. Any of the solutions might solve the problem. It is also
possible that none of the solutions solve the problem.
Once you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution. Determine whether the solution meets the
stated goals.
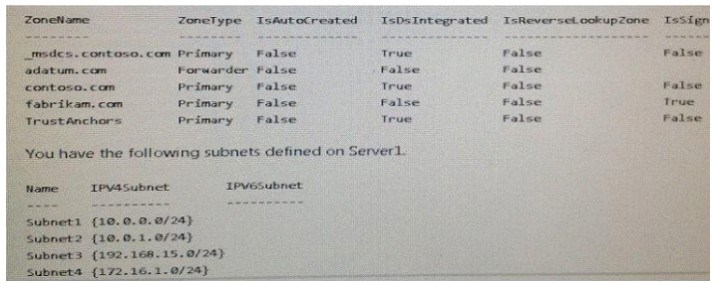
Your network contains an Active Directory domain named contoso.com. The domain contains a
DNS server named Server1. All client computers run Windows 10. On Server1, you have the
following zone configuration:
You need to prevent Server1 from resolving queries from DNS clients located on Subnet4. Server1
must resolve queries from all other DNS clients.
Solution: From a Group Policy object (GPO) in the domain, you modify the Network List Manager
Policies (NLMP).
Does this meet the goal?
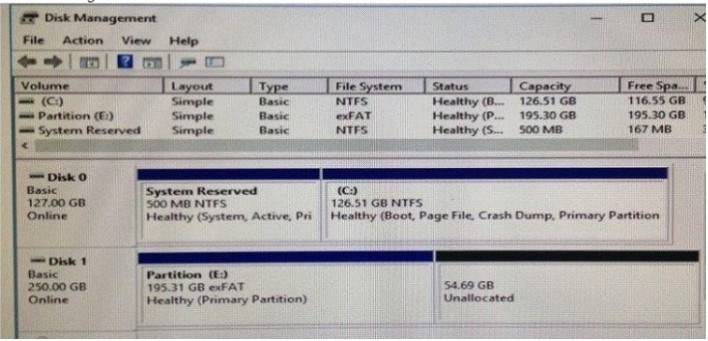
You need to ensure that you can use Disk1 (or Storage S…
You need to ensure that you can perform the migration o…
You have an Active Director domain named Contoso.com. The domain contains servers named
Server1, Server2 and Server3 that run Windows Server 2016. Server1 and Server2 are nodes in a
Hyper V cluster named Cluster1. You add a Hyper V Replica Broker role named Broker 1 to
Cluster1. Server3 is a Hyper-V server. A virtual machine named VM1 runs on Server3. Live
Migration is enabled on all three servers and it is configured to use Kerberos authentication only.
You need to ensure that you can perform the migration of VM1 to Server2. What should you do?
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
You have a server named Server1 that runs Windows Server 2016. Server1 hosts a line-ofbusiness application named App1. App1 has a memory leak that occasionally causes the
application to consume an excessive amount of memory. You need to log an event in the
Application event log whenever App1 consume more than 4 GB of memory.
Solution: You create a performance counter data collector.
Does this meet the goal?