Which approach should you recommend?
You need to design a solution for ensuring that only users with the Administrators role have access to the Admin area of the Web application
Which approach should you recommend?
Which code segment should you insert at line 04?
You use Microsoft Visual Studio 2010 and Microsoft .NET Framework 4.0 to create an application.
The application contains the following XML document:
<bib>
<book title=”TCP/IP Illusrated” year=”1994″>
<author>Author1</author>
</book>
<book title=”Programming in UNIX” year=”1992″>
<author>Author1</author>
<author>Author2</author>
<author>Author3</author>
</book>
<book title=”Data on the web” year=”2000″>
<author>Author4</author>
<author>Author3</author>
</book>
</bib>
You add the following code fragment. (Line numbers are included for reference only.)
01 public IEnumerable<XElement> GetBooks(string xml)
02 {
03 XDocument doc = XDocument.Parse(xml);
04 …
05 }
You need to return a list of book XML element that are authored by Author1. Which code segment should you insert at line 04?
Which approach should you recommend?
You ate designing an ASP NET MVC 2 Web application
The view content will be composed of user controls
You have the following requirements:
– Deliver content that is provided by user controls to the browser
– Select the appropriate user controls to render within the controller.
You need to ensure that your design meets the requirements.
Which approach should you recommend?
What should you do in the Application.Client Project?
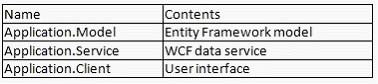
You use Microsoft Visual Studio 2010 and Microsoft .NET Framework 4.0 to create a Windows Communication
Foundation (WCF) Data Services service. The solution contains the projects shown in the following table.
The WCF data service exposes an Entity Framework model. You need to Access the service by using a WCF Data Services client.
What should you do in the Application.Client Project?
Which layer should you recommend?
You are designing a testing methodology for an ASP NET MVC 2 Web application.
The application has a simple domain model that provides a thin wrapper over a data access layer Controllers interact with the domain model directly and use methods on repository objects to save and retrieve objects from the data access layer.
You have the following requirements:
– Centralize data operations.
– Directly validate data access rules
You need to design tests against the appropriate layer to meet the requirements.
Which layer should you recommend?
What should you do?
You use Microsoft Visual Studio 2010 and Microsoft .NET Framework 4.0 to create a Windows Communication Foundation (WCF) Data Services service.
WCF Data Services uses an authentication scheme that requires an HTTP request that has the following header format:
GET /Odata.svc/Products(1)
Authorization: WRAP access_token=123456789
The application includes the following code. (Line numbers are included for reference only.)
01 public class program
02 {
03 Public void GetProducts()
04 {
05 var proxy = new MyDataServiceContext(“…”);
06 …
07 }
08 }
You need to ensure that the correct authentication header is present when requests are made by using MyDataServiceContext.
What should you do?
Which approach should you recommend?
You are designing an ASP. NET Web application.
The Web application includes a section for sales pages.
You need to ensure that the sales pages share a specific header and a specific footer that differ from those of all other pages in the application.
Which approach should you recommend?
Which code segment should you use?
You use Microsoft Visual Studio 2010 and .NET Framework 4.0 to create an application.
The application connects to a Microsoft SQL Server 2008 database. The application contains the following code segment.
string SQL = string.Format(SELECT * FROM Customer WHERE CompanyName LIKE %{0}%, companyName);
var cmd = new SqlCommand(SQL, con);
You need to reduce the vulnerability to SQL injection attacks. Which code segment should you use?
Which approach should you recommend?
You are planning a deployment process for a set of interrelated Web services.
You need to ensure maximum availability of the Web services in the event of a hardware or software failure.
Which approach should you recommend?
Which two actions should you recommend?
You are designing a class library that will be used for all of your company’s ASP.NET Web applications.
A specific variable in a helper class within the library holds very sensitive information.
You need to ensure that the variable is not visible to developers when they are debugging any of the Web applications.
Which two actions should you recommend.
(Each correct answer presents part of the solution. Choose two.)