Which binding should you recommend?
A Microsoft Windows Communication Foundation (WCF) service is hosted on a web server. You need to recommend the binding that can be used to access the WCF service from a Windows Phone 7 application. Which binding should you recommend?
What is the function of the XPath query?
Your company network includes Forefront Identity Manager (FIM) 2010.
The FIM server has the following XPath query:
/Request[Target = /Group[Type = ‘Security’] and Operation = ‘Put’ and CreatedTime >= op:subtract- dayTimeDuration-from-dateTime(fn:current-dateTime(), xs:dayTimeDuration(‘P7D’))] What is the function of the XPath query?
What should you do first?
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
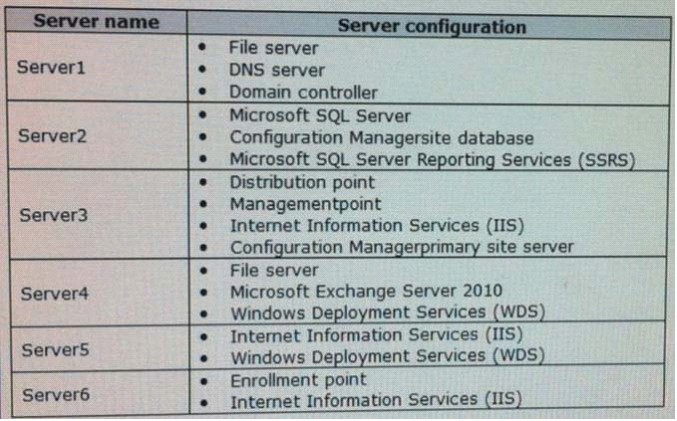
Your network contains a System Center 2012 Configuration Manager environment that contains six servers configured as shown in the following table. Server5 and Server6 are in the perimeter network, while Server1, Server2, Server3, and Server4 are in the internal network.
Administrators currently apply software updates to servers manually. You discover that Server4 was never updated. You need to centrally manage software updates for all of the servers by using configuration Manager. What should you do first?
What should you recommend?
You are designing a Windows Phone 7 application that uses several pages for the entry of user data. A user can navigate freely among the pages in the application at any time. The user can also perform actions that use a PhotoChooserTask object to select images. You need to recommend a way for the selected images to persist when the user navigates through the application. What should you recommend?
What should you recommend?
You are designing a Windows Phone 7 application that uses several pages for the entry of user data. A user can navigate freely among the pages in the application at any time. The user can also perform actions that use a PhotoChooserTask object to select images. You need to recommend a way for the selected images to persist when the user navigates through the application. What should you recommend?
What should you do?
You administer a Forefront Identity Manager (FIM) 2010 server for your company named Contoso, Ltd. You discover that several users have not been assigned to a manager within the FIM metaverse. You need to identify the users who have no manager within the metaverse. What should you do?
What should you do?
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
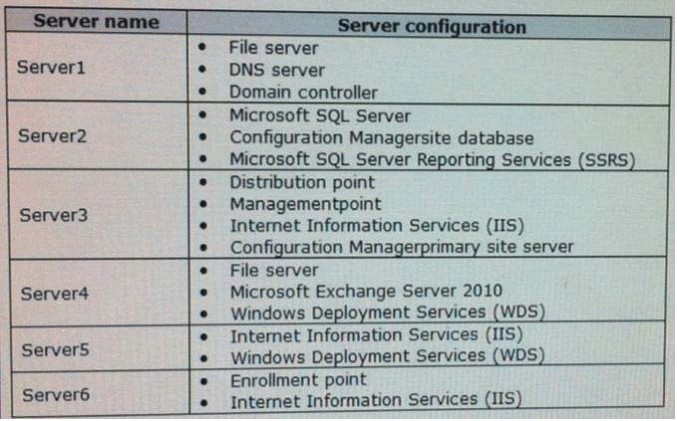
Your network contains a System Center 2012 Configuration Manager environment that contains six servers configured as shown in the following table. Server5 and Server6 are in the perimeter network, while Server1, Server2, Server3, and Server4 are in the internal network.
A corporate security policy states that remote computers are forbidden to communicate directly with servers on the internal network. You need to ensure that you collect inventory data from the remote computers. What should you do?
What should you do?
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment that contains six servers configured as shown in the following table. Server5 and Server6 are in the perimeter network, while Server1, Server2, Server3, and Server4 are in the internal network.
A corporate security policy states that remote computers are forbidden to communicate directly with servers on the internal network. You need to ensure that you collect inventory data from the remote computers. What should you do?
What should you do?
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment that contains six servers configured as shown in the following table. Server5 and Server6 are in the perimeter network, while Server1, Server2, Server3, and Server4 are in the internal network.
A corporate security policy states that remote computers are forbidden to communicate directly with servers on the internal network. You need to ensure that you collect inventory data from the remote computers. What should you do?
What should you do?
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
Your network contains a System Center 2012 Configuration Manager environment that contains six servers configured as shown in the following table. Server5 and Server6 are in the perimeter network, while Server1, Server2, Server3, and Server4 are in the internal network.
A corporate security policy states that remote computers are forbidden to communicate directly with servers on the internal network. You need to ensure that you collect inventory data from the remote computers. What should you do?