which two statements are correct?
What is a secure key management protocol used by IPsec?
What is a secure key management protocol used by IPsec?
Which command would you use to accomplish this task?
Your manager asks you to show which attacks have been detected on your SRX Series
device using the IPS feature. Which command would you use to accomplish this task?
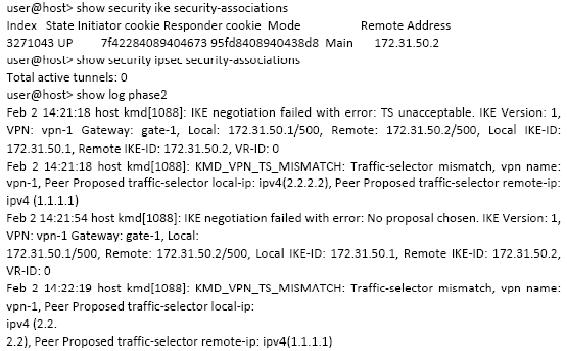
What are two reasons for this problem?
A local user complains that they cannot connect to an FTP server on the DMZ network. You
investigate and confirm that the security policy allows FTP traffic from the trust zone to the
DMZ zone. What are two reasons for this problem? (Choose two.)
what is the cause of this problem?
What is the result of the communication?
Where does the AppSecure suite of functions occur in the security flow process on an SRX Series device?
Where does the AppSecure suite of functions occur in the security flow process on an SRX
Series device?
Which two configuration statements are used to share interface routes between routing instances?
Which two configuration statements are used to share interface routes between routing
instances? (Choose two.)
which statement is true?
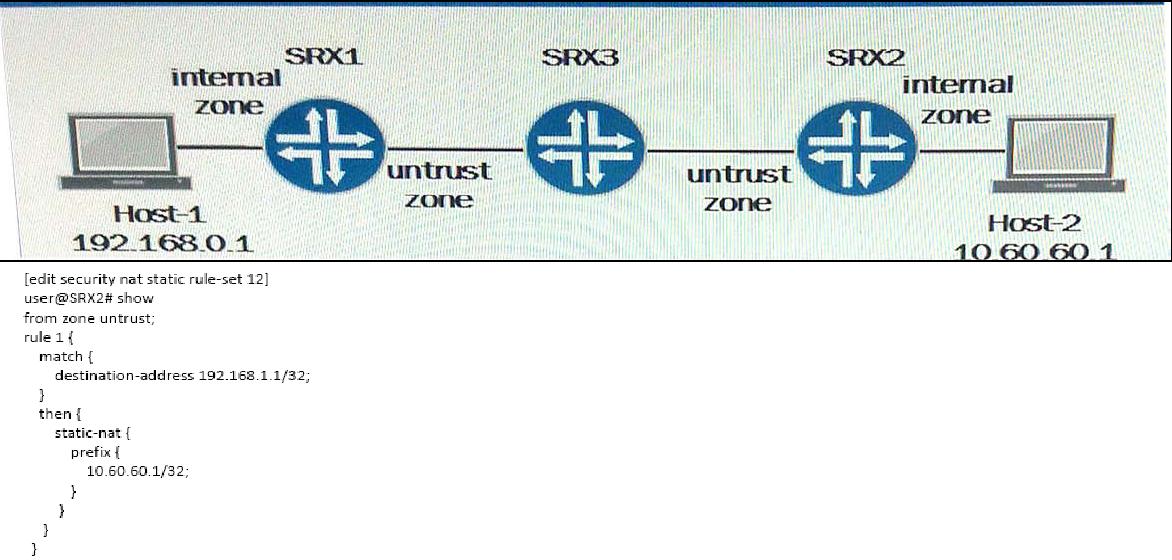
Click the Exhibit button. Traffic is being sent from Host-1 to Host-2 through an IPsec VPN.
In this process, SRX-2 is using NAT to change the destination address of Host-2 from
192.168.1.1 to 10.60.60.1 SRX-1 uses the 172.31.50.1 address for its tunnel endpoint and
SRX-2 uses the 10.10.50.1 address for its tunnel endpoint. Referring to the exhibit, which
statement is true?
How does the SRX5800, in transparent mode, signal failover to the connected switches?
How does the SRX5800, in transparent mode, signal failover to the connected switches?