Which statement describes a security zone?
Which statement describes a security zone?
Which problem can arise from this type of attack?
A system administrator detects thousands of open idle connections from the same source.Which
problem can arise from this type of attack?
which Junos hierarchy level are security policies configured?
Under which Junos hierarchy level are security policies configured?
Which configuration meets this requirement?
You must configure a SCREEN option that would protect your device from a session table flood.
Which configuration meets this requirement?
Which three methods of source NAT does the Junos OS support?
Which three methods of source NAT does the Junos OS support? (Choose three.)
Which three firewall user authentication objects can be referenced in a security policy?
Which three firewall user authentication objects can be referenced in a security policy? (Choose
three.)
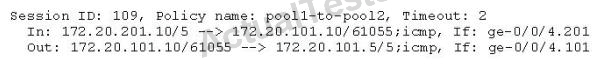
What is the default session timeout for TCP sessions?
What is the default session timeout for TCP sessions?
Which three advanced permit actions within security policies are valid?
Which three advanced permit actions within security policies are valid? (Choose three.)
Which statement is true regarding the Junos OS for security platforms?
Which statement is true regarding the Junos OS for security platforms?