Within Kerberos, which part is the single point of failure?
Within Kerberos, which part is the single point of failure?
A type II biometric is also known as what?
A type II biometric is also known as what?
What control combination are the security guards?
An attacker sees a building is protected by security guards, and attacks a building next door with no guards. What control combination are the security guards?
What access control method weighs additional factors such as time of attempted access before granting access?
What access control method weighs additional factors such as time of attempted access before granting access?
What is the most important decision an organization needs to make when implementing Role Based Access Control
What is the most important decision an organization needs to make when implementing Role Based Access Control (RBAC)?
What is the term used for describing when an attacker, through a command and control network, controls hundred
What is the term used for describing when an attacker, through a command and control network, controls hundreds, thousands, or even tens of thousands of computers and instructs all of these computers to perform actions all at once?
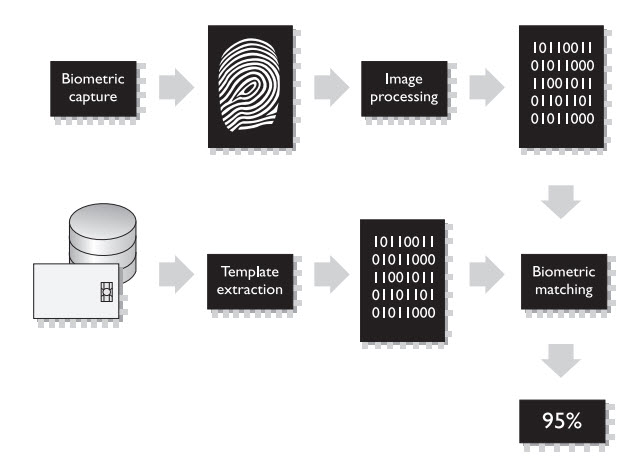
What are the main differences between retina scans and iris scans?
What are the main differences between retina scans and iris scans?
The most insidious part of Phishing and Spear Phishing attacks comes from which part of the attack anatomy?
The most insidious part of Phishing and Spear Phishing attacks comes from which part of the attack anatomy?
What is the difference between password cracking and password guessing?
What is the difference between password cracking and password guessing?