How does TKIP provide more protection for WLAN environments?
How does TKIP provide more protection for WLAN environments?
What does it mean if someone says they were a victim of a Bluejacking attack?
What does it mean if someone says they were a victim of a Bluejacking attack?
Which of the following is the proper mapping for the items missing in the provided table?
What type of material is shown in the following photo?
Of CPTED’s three main components, what is illustrated in the following photo?
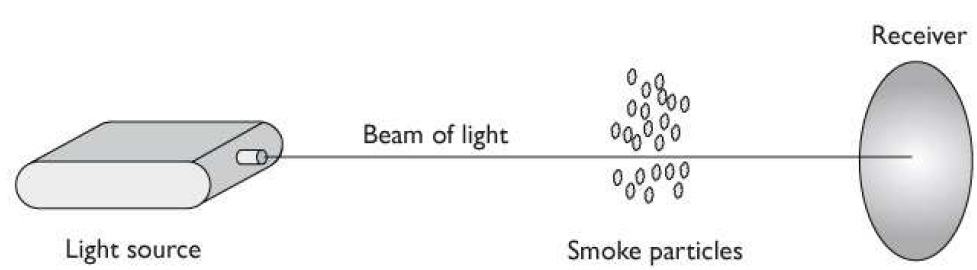
What type of detector is shown in the following graphic?
What type of fence detects if someone attempts to climb or cut it?
What type of fence detects if someone attempts to climb or cut it?
Which of the following is best to keep voltage steady and power clean?
A number of measures should be taken to help protect devices and the environment from electric power issues. Which of the following is best to keep voltage steady and power clean?
Which of the following steps comes first in the process of rolling out a security program?
Before an effective physical security program can be rolled out, a number of steps must be taken. Which of the following steps comes first in the process of rolling out a security program?
Which of the following is not true of IDSs?
Which of the following is not true of IDSs?