what site can be used to view the website collection of…
When needing to search for a website that is no longer present on the Internet today but was online few years
back, what site can be used to view the website collection of pages?
What is the smallest physical storage unit on a hard drive?
What is the smallest physical storage unit on a hard drive?
What type of cipher was used by the accused in this case?
Heather, a computer forensics investigator, is assisting a group of investigators working on a large computer
fraud case involving over 20 people. These 20 people, working in different offices, allegedly siphoned off
money from many different client accounts. Heather responsibility is to find out how the accused people
communicated between each other. She has searched their email and their computers and has not found any
useful evidence. Heather then finds some possibly useful evidence under the desk of one of the accused.
In an envelope she finds a piece of plastic with numerous holes cut out of it. Heather then finds the same exact
piece of plastic with holes at many of the other accused peoples desks. Heather believes that the 20 people
involved in the case were using a cipher to send secret messages in between each other. What type of cipher
was used by the accused in this case?
What feature of Decryption Collection allows an investi…
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
How many data acquisition tools should Michael use when…
Daryl, a computer forensics investigator, has just arrived at the house of an alleged computer hacker. Daryltakes pictures and tags all computer and peripheral equipment found in the house. Daryl packs all the items
found in his van and takes them back to his lab for further examination. At his lab, Michael his assistant helps
him with the investigation. Since Michael is still in training, Daryl supervises all of his work very carefully.
Michael is not quite sure about the procedures to copy all the data off the computer and peripheral devices.
How many data acquisition tools should Michael use when creating copies of the evidence for the
investigation?
Which file should be used to restore archived email mes…
Why would this not be recommended?
A small law firm located in the Midwest has possibly been breached by a computer hacker looking to obtain
information on their clientele. The law firm does not have any on-site IT employees, but wants to search for
evidence of the breach themselves to prevent any possible media attention. Why would this not be
recommended?
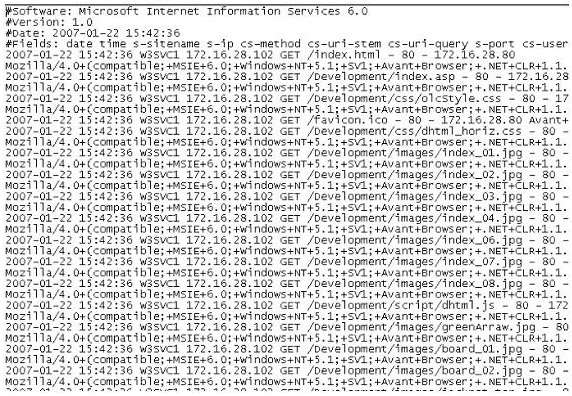
What time standard is used by IIS as seen in the screenshot?
What must an investigator do before disconnecting an iP…
What must an investigator do before disconnecting an iPod from any type of computer?
What technique used by Encase makes it virtually imposs…
What technique used by Encase makes it virtually impossible to tamper with evidence once it has been
acquired?