what would you call such an attack?
In the context of password security, a simple dictionary attack involves loading a dictionary file (a
text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper,
and running it against user accounts located by the application. The larger the word and word
fragment selection, the more effective the dictionary attack is. The brute force method is the most
inclusive, although slow. It usually tries every possible letter and number combination in its
automated exploration.
If you would use both brute force and dictionary methods combined together to have variation of
words, what would you call such an attack?
which you will NOT be able to accomplish with this probe?
What is the algorithm used by LM for Windows2000 SAM?
What is the algorithm used by LM for Windows2000 SAM?
Which of the following Trojans would be considered ‘Botnet Command Control Center’?
Which of the following Trojans would be considered ‘Botnet Command Control Center’?
which of the following?
E-mail scams and mail fraud are regulated by which of the following?
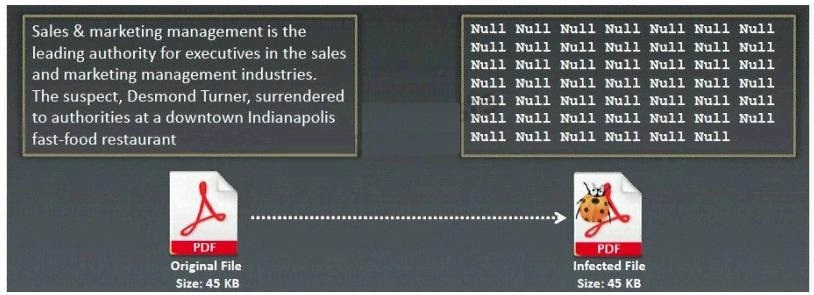
What type of Virus is shown here?
Which of the following LM hashes represent a password of less than 8 characters?
Which of the following LM hashes represent a password of less than 8 characters? (Select 2)
What would be the name of this tool?
John is using a special tool on his Linux platform that has a database containing signatures to be
able to detect hundreds of vulnerabilities in UNIX, Windows, and commonly used web CGI/ASPX
scripts. Moreover, the database detects DDoS zombies and Trojans as well. What would be the
name of this tool?
Which of the following is the primary objective of a rootkit?
Which of the following is the primary objective of a rootkit?
What does this mean?
Fred is scanning his network to ensure it is as secure as possible. Fred sends a TCP probe packet
to a host with a FIN flag and he receives a RST/ACK response. What does this mean?