Which of the following steganography utilities exploits the nature of white space and allows the user to conce
Which of the following steganography utilities exploits the nature of white space and allows the
user to conceal information in these white spaces?
what is the hacker really trying to steal?
Exhibit:
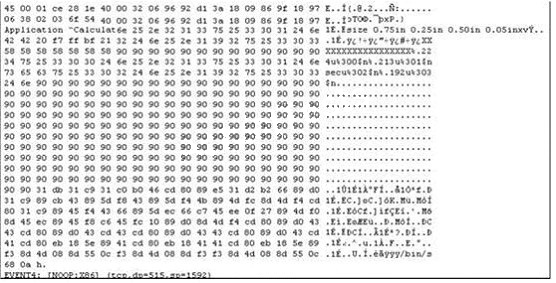
Based on the following extract from the log of a compromised machine, what is the hacker really
trying to steal?
How long will it take to crack the password by an attacker?
You have chosen a 22 character word from the dictionary as your password. How long will it take
to crack the password by an attacker?
what would you conclude about the attack?
The following is an entry captured by a network IDS.You are assigned the task of analyzing this
entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel
processor. You figure that the attacker is attempting a buffer overflow attack. You also notice
“/bin/sh” in the ASCII part of the output. As an analyst what would you conclude about the attack?
What vulnerability is detected in the web application here?
While testing web applications, you attempt to insert the following test script into the search area
on the company’s web site:
<script>alert(‘Testing Testing Testing’)</script>
Later, when you press the search button, a pop up box appears on your screen with the text
“Testing Testing Testing”. What vulnerability is detected in the web application here?
what are some of the things you would recommend to a company to ensure DNS security?
As a securing consultant, what are some of the things you would recommend to a company to
ensure DNS security? Select the best answers.
What techniques would you use to evade IDS during a Port Scan?
What techniques would you use to evade IDS during a Port Scan? (Select 4 answers)
Why would you consider sending an email to an address that you know does not exist within the company you are
Why would you consider sending an email to an address that you know does not exist within the
company you are performing a Penetration Test for?
What kind of Denial of Service attack was best illustrated in the scenario above?
Bob was frustrated with his competitor, Brownies Inc., and decided to launch an attack that would
result in serious financial losses. He planned the attack carefully and carried out the attack at the
appropriate moment.
Meanwhile, Trent, an administrator at Brownies Inc., realized that their main financial transaction
server had been attacked. As a result of the attack, the server crashed and Trent needed to reboot
the system, as no one was able to access the resources of the company. This process involves
human interaction to fix it.
What kind of Denial of Service attack was best illustrated in the scenario above?
What tool can crack Windows SMB passwords simply by listening to network traffic?
What tool can crack Windows SMB passwords simply by listening to network traffic?
Select the best answer.