Which of the following Nmap commands would be used to perform a stack fingerprinting?
Which of the following Nmap commands would be used to perform a stack fingerprinting?
Destination unreachable administratively prohibited messages can inform the hacker to what?
Destination unreachable administratively prohibited messages can inform the hacker to what?
Which Steganography technique uses Whitespace to hide secret messages?
Which Steganography technique uses Whitespace to hide secret messages?
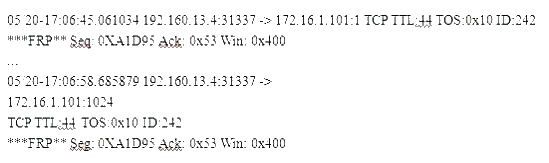
What is odd about this attack?
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic
TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration
tester finds it to be abnormal. If you were the penetration tester, why would you find this
abnormal?
What is odd about this attack? Choose the best answer.
How would you detect IP spoofing?
Cyber Criminals have long employed the tactic of masking their true identity. In IP spoofing, an
attacker gains unauthorized access to a computer or a network by making it appear that a
malicious message has come from a trusted machine, by “spoofing” the IP address of that
machine.
How would you detect IP spoofing?
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up
by and IDS?
How can David block POP3 at the firewall?
David is a security administrator working in Boston. David has been asked by the office’s manager
to block all POP3 traffic at the firewall because he believes employees are spending too much
time reading personal email. How can David block POP3 at the firewall?
Name two software tools used for OS guessing?
Name two software tools used for OS guessing? (Choose two.
What display filter should you use that shows all TCP packets that contain the word ‘facebook’?
You want to capture Facebook website traffic in Wireshark. What display filter should you use that
shows all TCP packets that contain the word ‘facebook’?
Which organization coordinates computer crime investigations throughout the United States?
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle
database server has been compromised and customer information along with financial data has
been stolen. The financial loss will be estimated in millions of dollars if the database gets into the
hands of competitors. Sandra wants to report this crime to the law enforcement agencies
immediately.
Which organization coordinates computer crime investigations throughout the United States?