Which of the following solutions should the security engineer recommend to meet the MOST goals?
Company A has a remote work force that often includes independent contractors and out of state
full time employees.
Company A’s security engineer has been asked to implement a solution allowing these users to
collaborate on projects with the following goals:
All communications between parties need to be encrypted in transport
Users must all have the same application sets at the same version
All data must remain at Company A’s site
All users must not access the system between 12:00 and 1:00 as that is the maintenance
window
Easy to maintain, patch and change application environment
Which of the following solutions should the security engineer recommend to meet the MOST
goals?
Drag and Drop the following information types on to the appropriate CIA category
Instructions The last install that is completed will be the final submission
CORRECT TEXT To perform the necessary tasks, please modify the DST port, protocol
Based on this information, the following tasks need to be completed:
CORRECT TEXT
The IDS has detected abnormal behavior on this network Click on the network devices to view
device information Based on this information, the following tasks need to be completed:
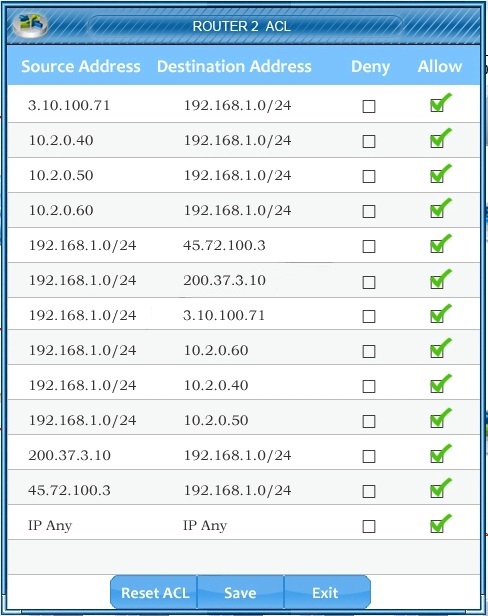
1. Select the server that is a victim of a SQL injection attack.
2 Select the source of the buffer overflow attack.
3. Modify the access control list (ACL) on the router(s) to ONLY block the buffer overflow attack.
Instructions: Simulations can be reset at any time to the initial state: however, all selections will be deleted.

Modify the network diagram to prevent SQL injections. XSS attacks, smurf attacks, e-mail spam, downloaded malw
DRAG DROP
Company A has experienced external attacks on their network and wants to minimize the attacks
from reoccurring. Modify the network diagram to prevent SQL injections. XSS attacks, smurf
attacks, e-mail spam, downloaded malware. viruses and ping attacks. The company can spend a
MAXIMUM of 550.000 USD. A cost list for each item is listed below
1. Anti-Virus Server- $10,000
2 Firewall-$15,000
3 Load Balanced Server – $10,000
4 NIDS/NIPS-$10,000
5. Packet Analyzer-55.000
6 Patch Server-$15,000
7 Proxy Server-$20,000 8. Router – S10.000
9 Spam Filter – S5 000
10 Traffic Shaper – $20,000
11. Web Application Firewall – $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once.

Which of the following designs is BEST suited for this purpose?
A startup company offering software on demand has hired a security consultant to provide
expertise on data security. The company’s clients are concerned about data confidentiality. The
security consultant must design an environment with data confidentiality as the top priority, over
availability and integrity. Which of the following designs is BEST suited for this purpose?
Which of the following BEST accomplishes this task?
A financial institution wants to reduce the costs associated with managing and troubleshooting
employees’ desktops and applications, while keeping employees from copying data onto external
storage. The Chief Information Officer (CIO) has asked the security team to evaluate four solutions
submitted by the change management group. Which of the following BEST accomplishes this
task?
Which of the following should the Information Security Officer be MOST concerned with based on this scenario?
A health service provider is considering the impact of allowing doctors and nurses access to the
internal email system from their personal smartphones. The Information Security Officer (ISO) has
received a technical document from the security administrator explaining that the current email
system is capable of enforcing security policies to personal smartphones, including screen lockout
and mandatory PINs. Additionally, the system is able to remotely wipe a phone if reported lost or
stolen. Which of the following should the Information Security Officer be MOST concerned with
based on this scenario? (Select THREE).
Which of the following should the security administrator check BEFORE responding to the request?
The security administrator at a company has received a subpoena for the release of all the email
received and sent by the company Chief Information Officer (CIO) for the past three years. The
security administrator is only able to find one year’s worth of email records on the server and is
now concerned about the possible legal implications of not complying with the request. Which of
the following should the security administrator check BEFORE responding to the request?





