Which of the following describes the encrypted data?
The administrator installs database software to encrypt each field as it is written to disk. Which of the following
describes the encrypted data?
which of the following is the MOST appropriate hashing …
When generating a request for a new x.509 certificate for securing a website, which of the following is the
MOST appropriate hashing algorithm?
Which of the following BEST describes the assessment th…
During a recent audit, it was discovered that many services and desktops were missing security patches. Which
of the following BEST describes the assessment that was performed to discover this issue?
Which of the following security-related trainings could…
Ann, a college professor, was recently reprimanded for posting disparaging remarks re-grading her coworkers
on a website. Ann stated that she was not aware that the public was able to view her remakes.
Which of the following security-related trainings could have made Ann aware of the repercussions of her
actions?
Which of the following algorithms is appropriate for se…
An organization wants to conduct secure transactions of large data files. Before encrypting and exchanging the
data files, the organization wants to ensure a secure exchange of keys. Which of the following algorithms is
appropriate for securing the key exchange?
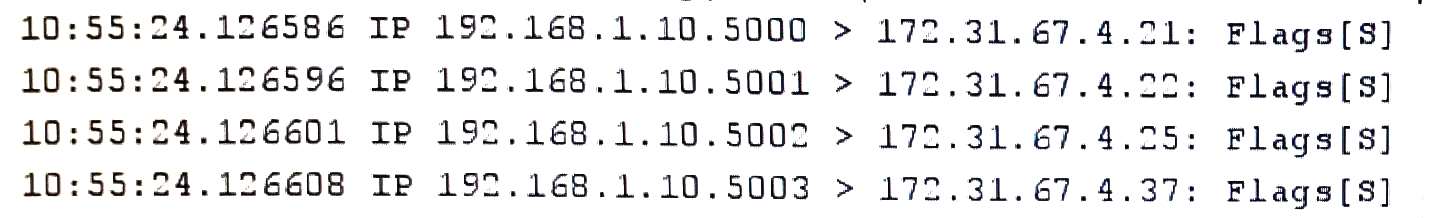
An attack that is using interference as its main attack…
An attack that is using interference as its main attack to impede network traffic is the following:
Which of the following would provide the BEST solution?
The IT department needs to prevent users from installing untested applications. Which of the following would
provide the BEST solution?
Which of the following ACLs provides the BEST protectio…
hown below: From IT department To employee Subject emai…
Many employees are receiving email messages similar to the one shown below:
From IT department
To employee
Subject email quota exceededPlease click on the following link http:www.website.info/email.php?quota=1Gb and provide your username and
password to increase your email quota. Upon reviewing other similar emails, the security administrator realized
that all the phishing URLs have the following common elements; they all use HTTP, they all come from .info
domains, and they all contain the same URI.
Which of the following should the security administrator configure on the corporate content filter to prevent
users from accessing the phishing URL, while at the same time minimizing false positives?
This is because the encryption scheme in use adheres to:
An attacker captures the encrypted communication between two parties for a week, but is unable to decrypt the
messages. The attacker then compromises the session key during one exchange and successfully
compromises a single message. The attacker plans to use this key to decrypt previously captured and future
communications, but is unable to. This is because the encryption scheme in use adheres to: